6-23
Cisco ASA 5550 Getting Started Guide
78-17644-01
Chapter 6 Scenario: DMZ Configuration
Configuring the Security Appliance for a DMZ Deployment
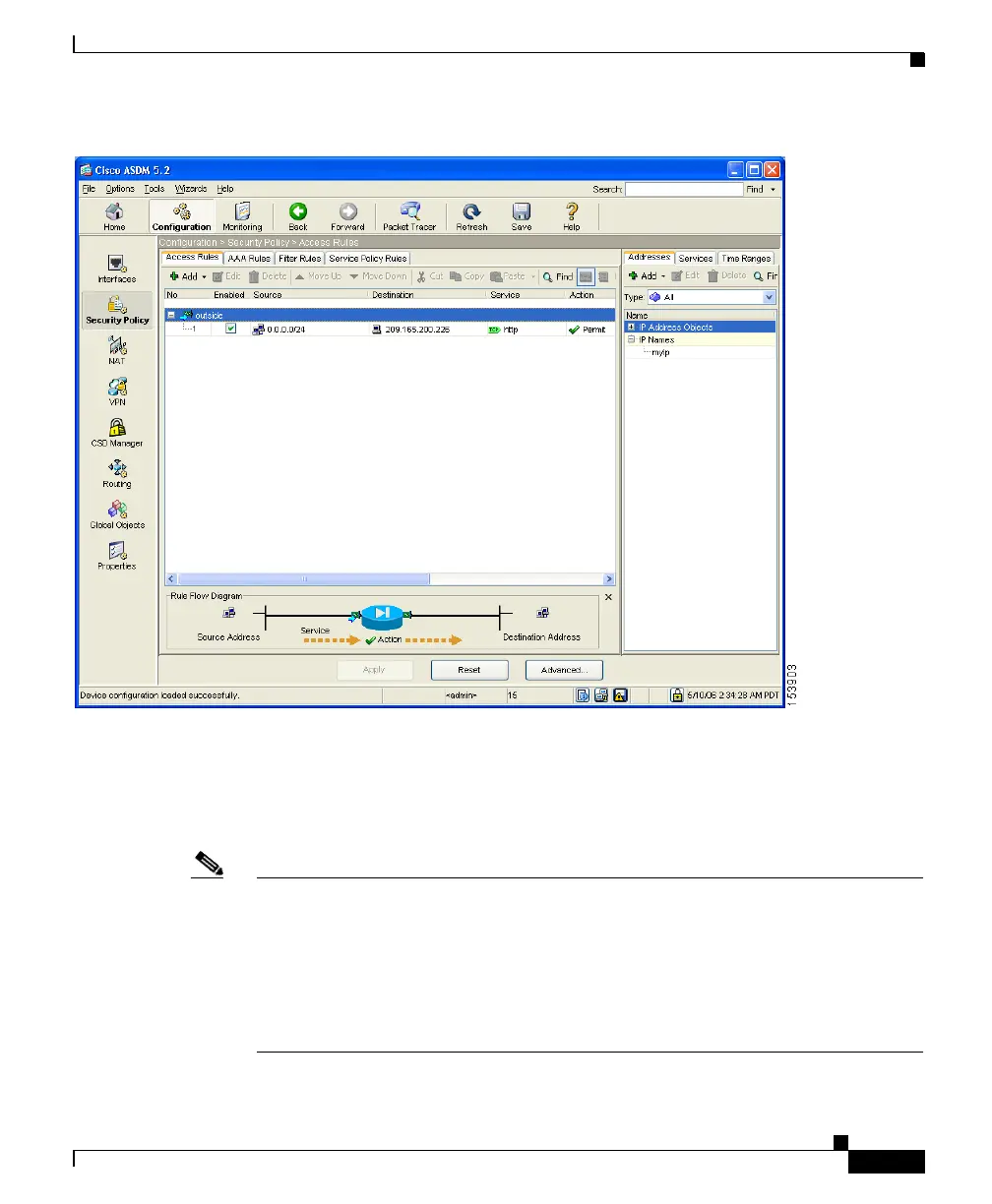
Step 7 Click Apply to save the configuration changes to the configuration that the
adaptive security appliance is currently running.
Clients on both the private and public networks can now resolve HTTP requests
for content from the DMZ web server, while keeping the private network secure.
Note Although the destination address specified is the private address of the DMZ web
server (10.30.30.30), HTTP traffic from any host on the Internet destined for the
public address 209.165.200.226 is permitted through the adaptive security
appliance. The address translation (209.165.200.226 to 10.30.30.30) allows the
traffic to be permitted. For information about creating the translation rule, see the
“Configuring NAT for Inside Clients to Communicate with the DMZ Web Server”
section on page 6-12.

 Loading...
Loading...