8-7
Cisco ASA 5550 Getting Started Guide
78-17644-01
Chapter 8 Scenario: Site-to-Site VPN Configuration
Implementing the Site-to-Site Scenario
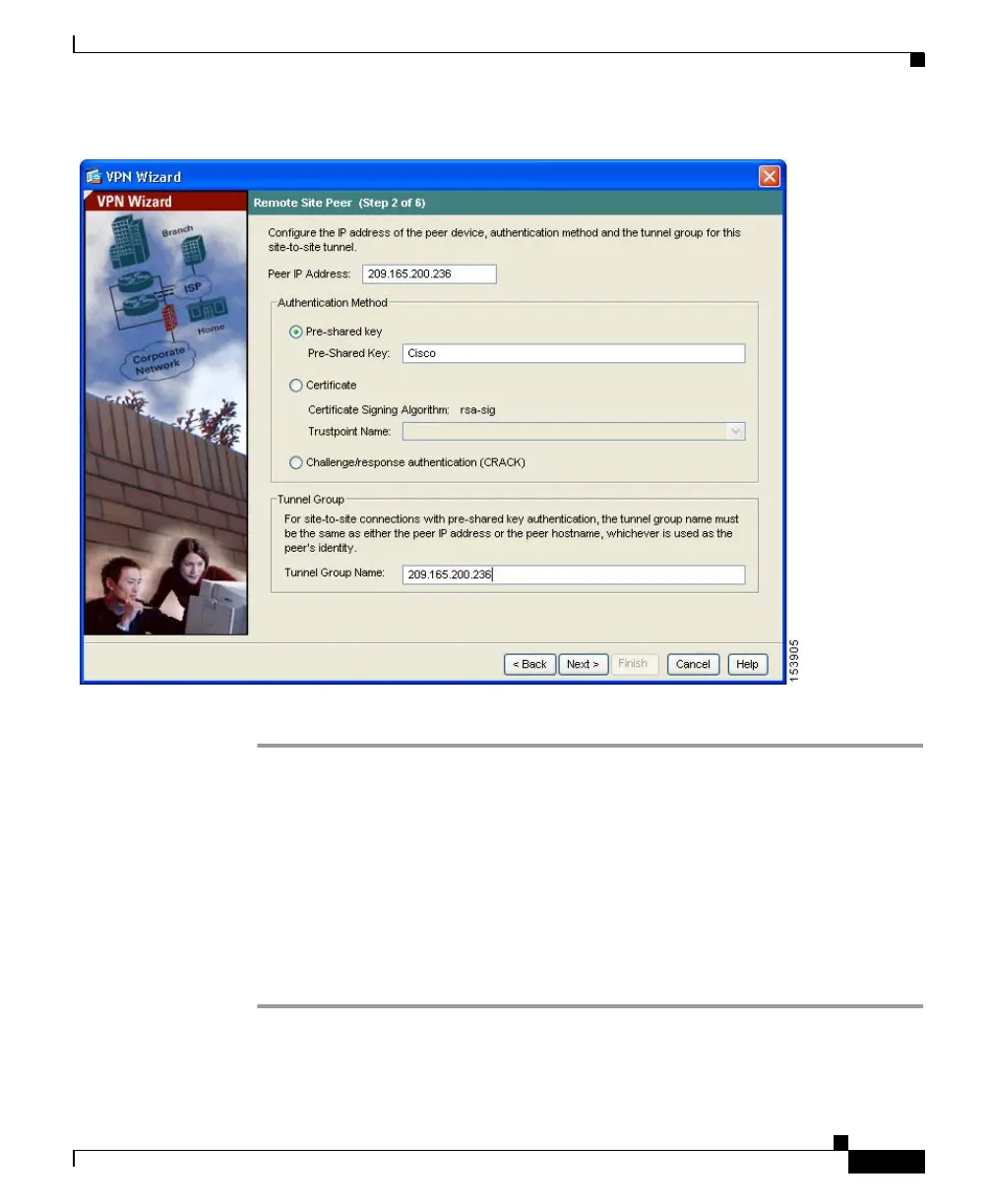
Step 3 Click Next to continue.
Configuring the IKE Policy
IKE is a negotiation protocol that includes an encryption method to protect data
and ensure privacy; it is also an authentication method to ensure the identity of the
peers. In most cases, the ASDM default values are sufficient to establish secure
VPN tunnels between two peers.
In Step 3 of the VPN Wizard, perform the following steps:
Step 1 Click the Encryption (DES/3DES/AES), authentication algorithms (MD5/SHA),
and the Diffie-Hellman group (1/2/5) used by the adaptive security appliance
during an IKE security association.

 Loading...
Loading...