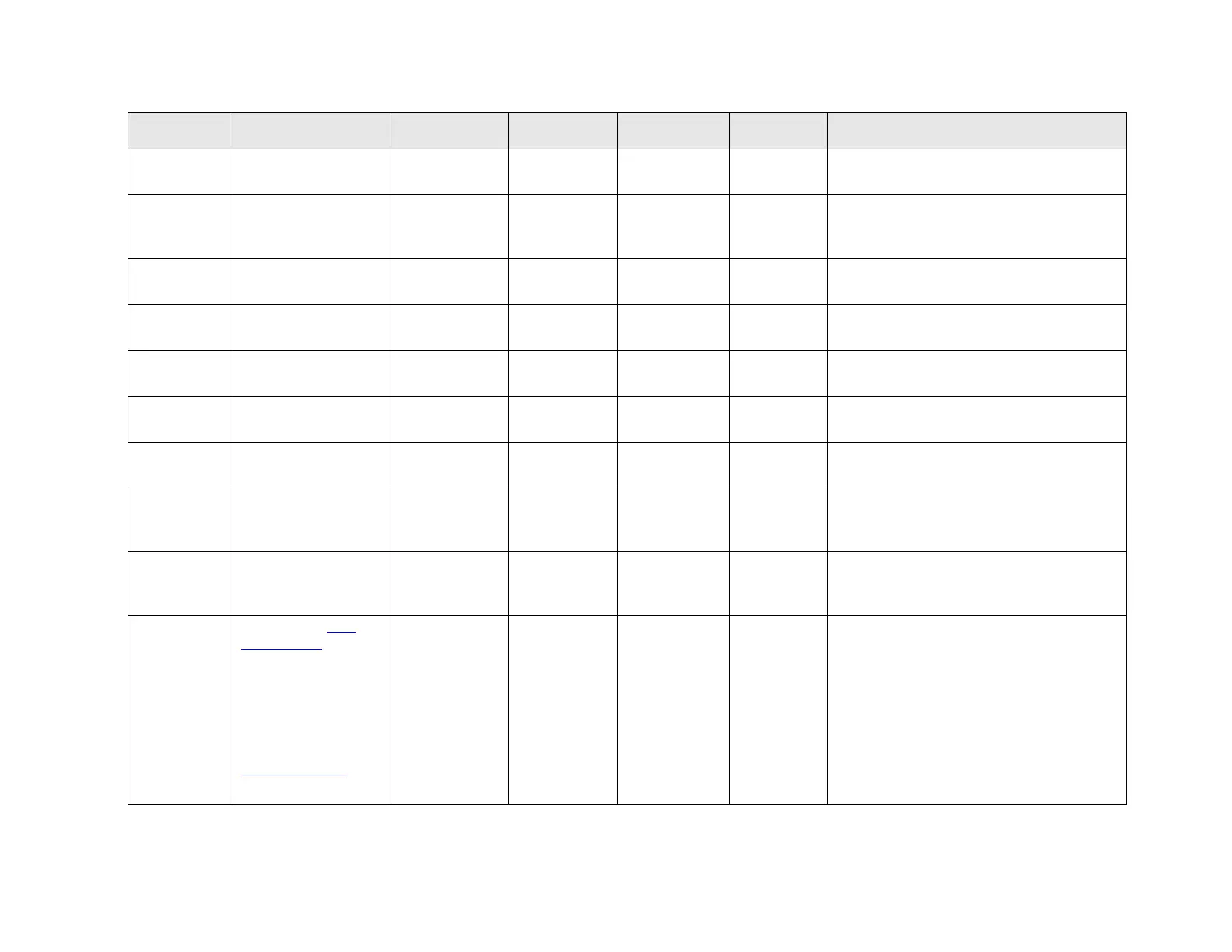
Allowed use in the certified configuration
Any configuration. Use of key-based
authentication is recommended.
Remote
Authentication Dial In
User Service
If used for authentication of ASA
administrators, secure through IPsec.
RSA SecurID
authentication
If used for authentication of ASA
administrators, secure through IPsec.
Simple Network
Management Protocol
Outbound (traps) only. Recommended to
tunnel through IPsec.
As described in the section 3.3.1 of this
document.
A protocol used for
terminal emulation
Use of SSH is recommended.
Trivial File Transfer
Protocol
Recommend using SCP instead, or tunneling
through IPsec.
Follow best practices for the secure usage as
there are no restrictions on use of these
protocols
Dynamic Trunking
Protocol
Follow best practices for the secure usage as
there are no restrictions on use of these
protocols
Standardized wide
area network
technology that
specifies the physical
and logical link layers
of digital
telecommunications
channels using a
packet switching
methodology
Follow best practices for the secure usage as
there are no restrictions on use of these
protocols
 Loading...
Loading...
















