Page 70 of 72
8 Security Measures for the Operational Environment
Proper operation of the TOE requires functionality from the environment. It is the
responsibility of the authorized administrator of the TOE to ensure that the Operational
Environment provides the necessary functions, and adheres to the environment security
objectives listed below. The environment security objective identifiers map to the
environment security objectives as defined in the Security Target.
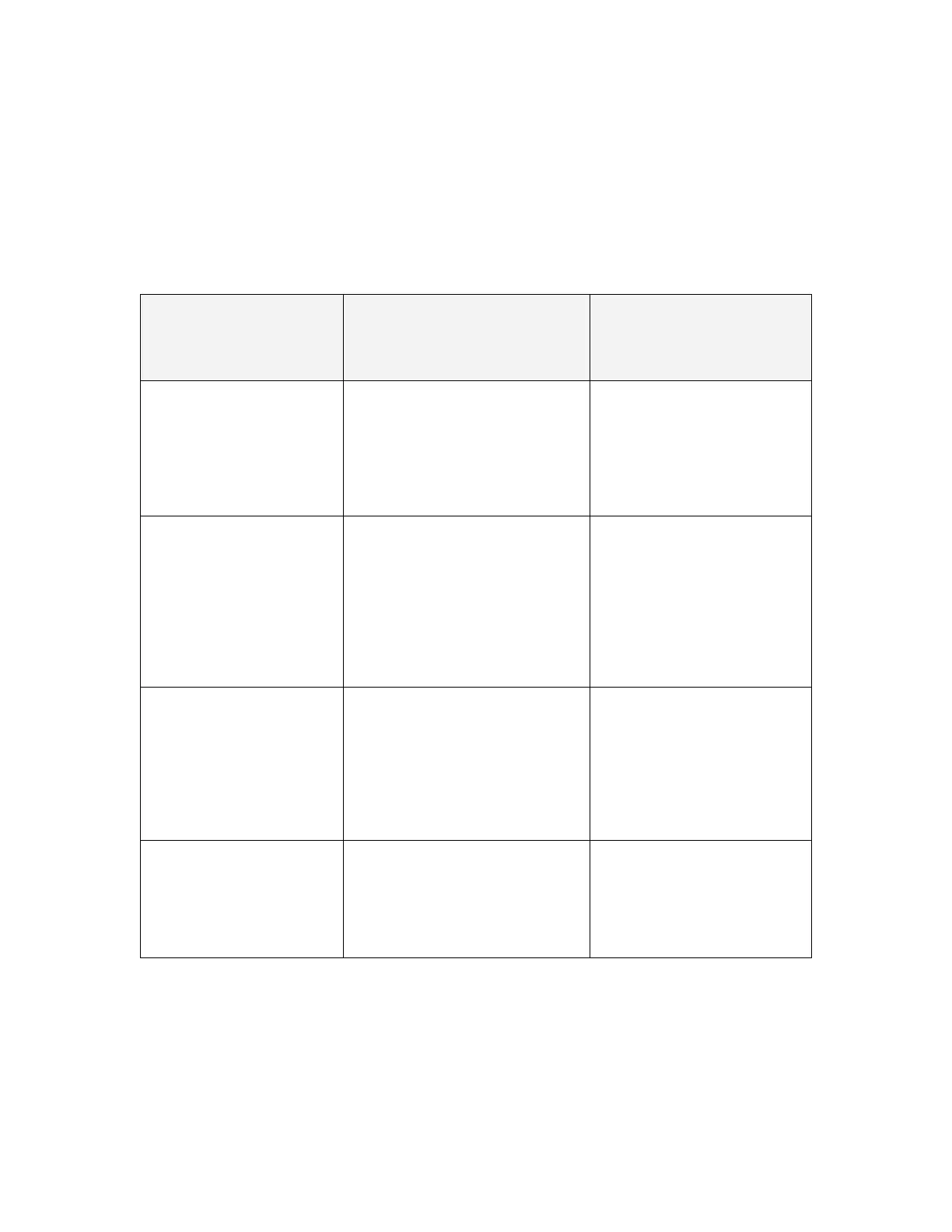
Table 10: Operational Environment Security Measures
Environment
Security Objective
Operational Environment
Security Objective
Definition
Privileged and Semi-
privileged
administrator
responsibility
There are no general-purpose
computing capabilities (e.g.,
compilers or user applications)
available on the TOE, other than
those services necessary for the
operation, administration and
support of the TOE.
Administrators will make sure
there are no general-purpose
computing capabilities (e.g.,
compilers or user applications)
available on the TOE.
Physical security, commensurate
with the value of the TOE and the
data it contains, is provided by the
environment.
Administrators must ensure the
TOE is installed and maintained
within a secure physical
location. This can include a
secured building with key card
access or within the physical
control of an authorized
administrator in a mobile
environment.
TOE Administrators are trusted to
follow and apply all administrator
guidance in a trusted manner.
Administrators must be properly
trained in the usage and proper
operation of the TOE and all the
provided functionality per the
implementing organization’s
operational security policies.
These administrators must
follow the provided guidance.
TOE administrators will ensure that
the TOE is installed in a manner that
will allow the TOE to effectively
enforce its policies on network
traffic flowing among attached
networks.
Administrators must ensure that
the TOE can enforce its security
policies on the network traffic
and not allowed to be ineffective
due to faulty installation.

 Loading...
Loading...
















