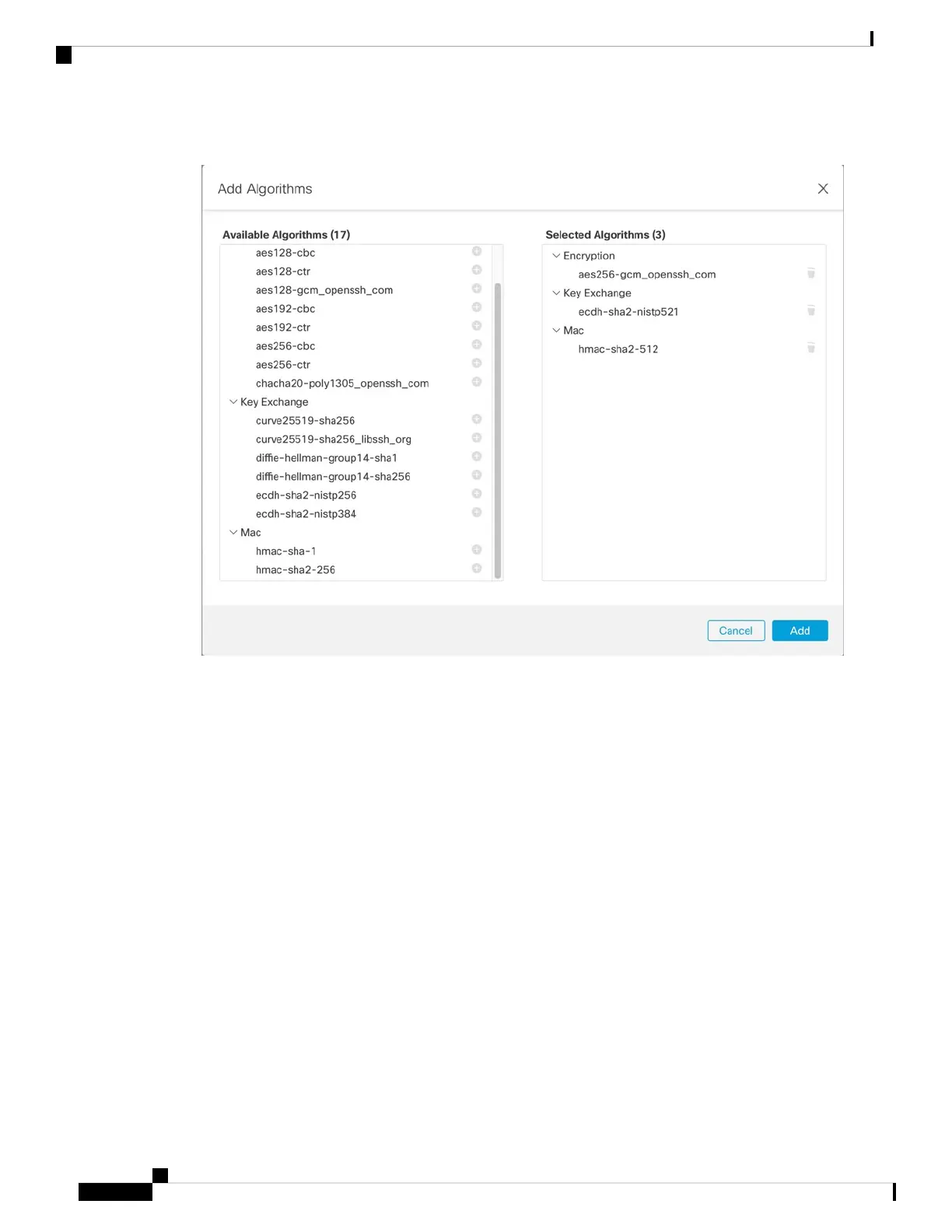
Figure 47: Add Algorithms
a) Select the Encryption algorithms.
b) Select the Key Exchange algorithms.
The key exchange provides a shared secret that cannot be determined by either party alone. The key
exchange is combined with a signature and the host key to provide host authentication. This key-exchange
method provides explicit server authentication.
c) Select the Mac integrity algorithms.
Step 5 For Host Key, enter the modulus size for the RSA key pairs.
The modulus value (in bits) is in multiples of 8 from 1024 to 2048. The larger the key modulus size you
specify, the longer it takes to generate an RSA key pair. We recommend a value of 2048.
Step 6 For the server Volume Rekey Limit, set the amount of traffic in KB allowed over the connection before
FXOS disconnects from the session.
Step 7 For the server Time Rekey Limit, set the minutes for how long an SSH session can be idle before FXOS
disconnects the session.
Step 8 For the SSH Client, configure the following settings.
Multi-Instance Mode for the Secure Firewall 3100
46
Multi-Instance Mode for the Secure Firewall 3100
Configure SSH and SSH Access List
 Loading...
Loading...











