Firewall
152
IDB operates by offering a number of services to the outside world that are monitored for
connection attempts. Remote machines attempting to connect to these services
generate a system log entry providing details of the access attempt, and the access
attempt is denied.
Because network scans often occur before an attempt to compromise a host, you can
also deny all access from hosts that have attempted to scan monitored ports. To enable
this facility, select one or both of the block options and these hosts are automatically
blocked once detected.
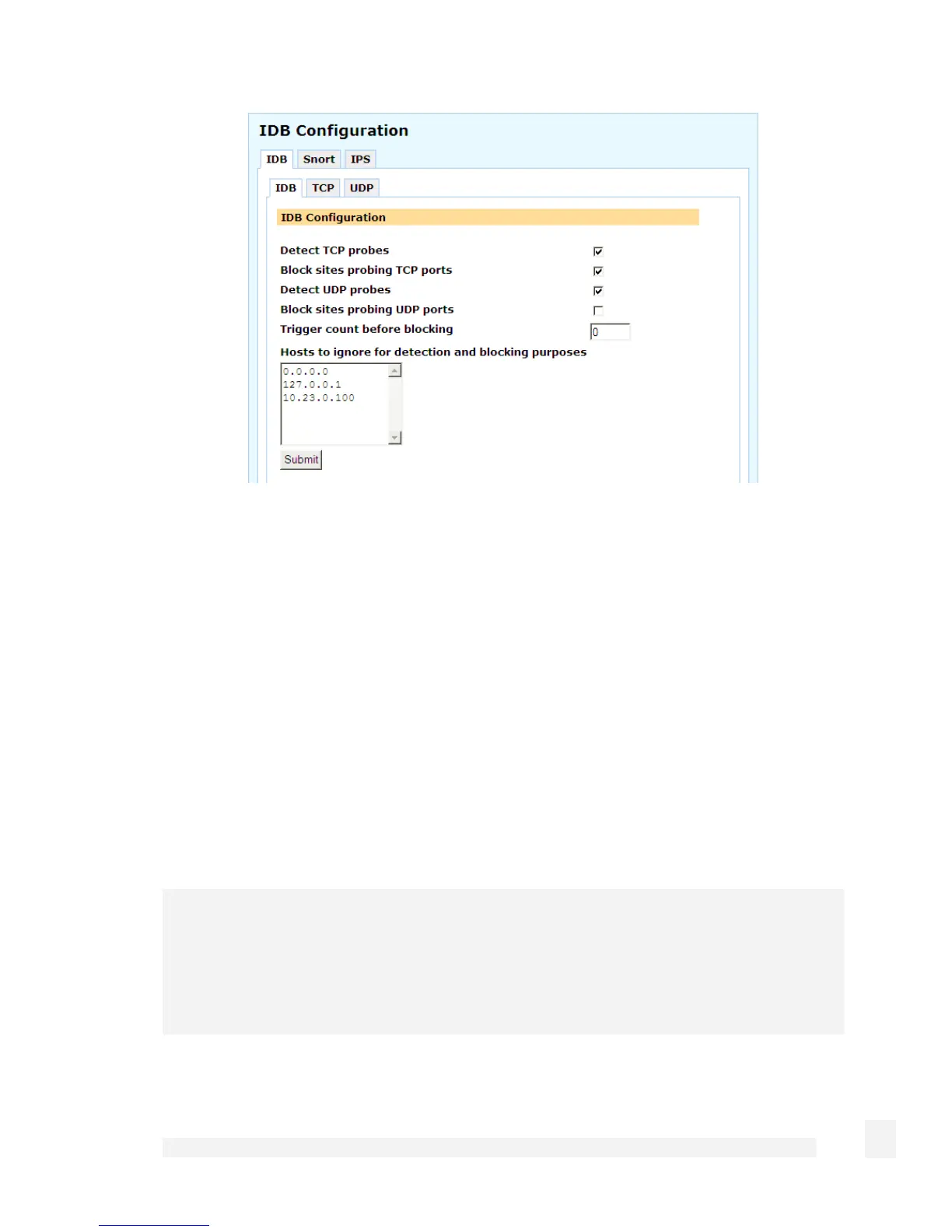
IDB Configuration
Detect TCP probes monitors dummy TCP services, Detect UDP probes monitors
dummy UDP services. Block sites probing TCP ports and Block sites probing UDP
ports blocks hosts attempting to connect to these services from all access to the
CyberGuard SG appliance. Connection attempts are logged under Scanning Hosts.
Warning
A word of caution regarding automatically blocking UDP requests. Because an attacker
can easily forge the source address of these requests, a host that automatically blocks
UDP probes can be tricked into restricting access from legitimate services. Proper
firewall rules and ignored hosts lists significantly reduces this risk.
 Loading...
Loading...