103
RADIUS-based MAC authentication configuration example
Network requirements
As shown in Figure 38, a host connects to port GigabitEthernet 1/0/1 on the access device. The device
uses RADIUS servers for authentication, authorization, and accounting.
Perform MAC authentication on port GigabitEthernet 1/0/1 to control Internet access. Make sure that:
• The device detects whether a user has gone offline every 180 seconds. If a user fails
authentication, the device does not authenticate the user within 180 seconds.
• All MAC authentication users belong to ISP domain 2000 and share the user account aaa with
password 123 456 .
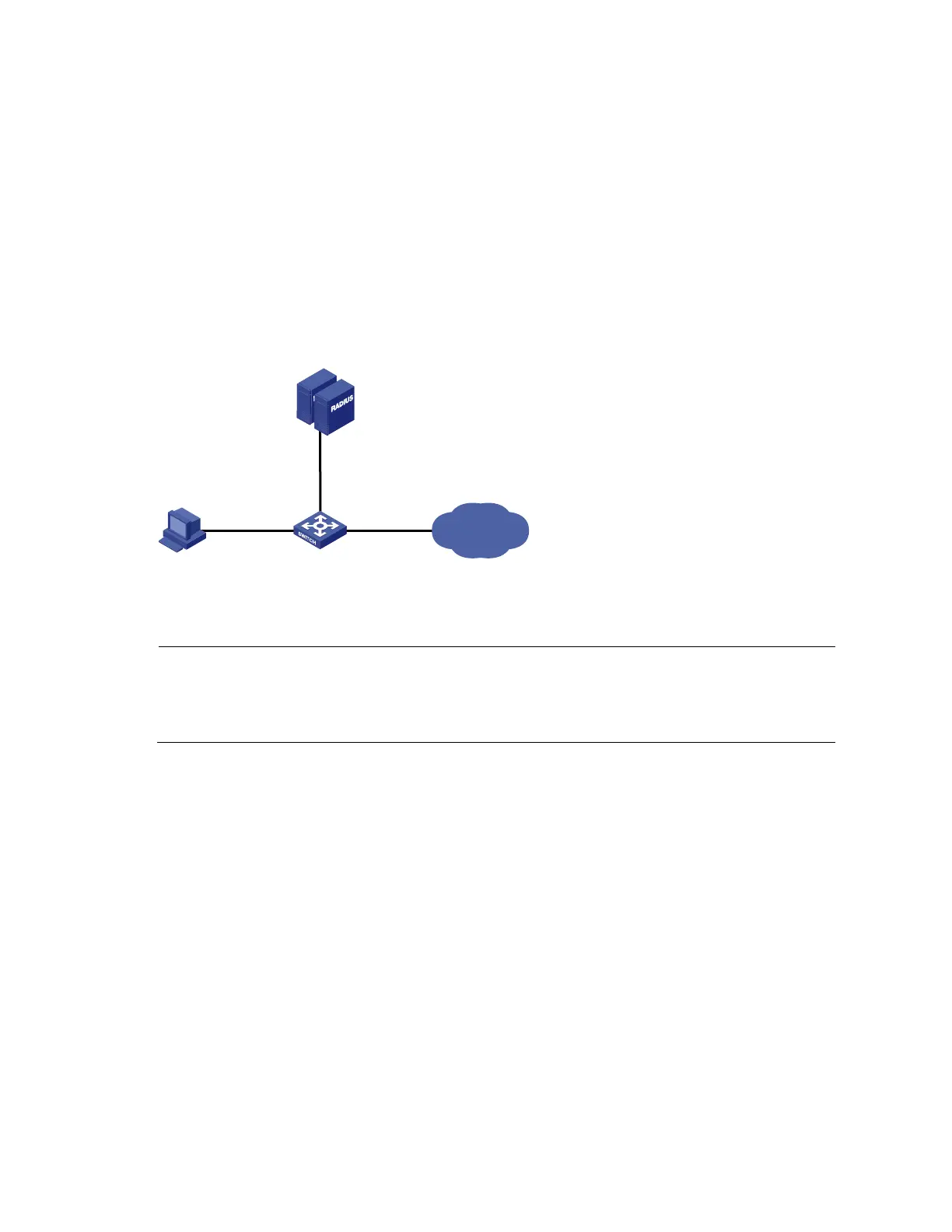
Figure 38 RADIUS-based MAC authentication
IP network
GE1/0/1
DeviceHost
RADIUS servers
Auth:10.1.1.1
Acct:10.1.1.2
Configuration procedure
NOTE:
Make sure that the RADIUS server and the access device can reach each other. Create a shared
account for MAC authentication users on the RADIUS server, and set the username aaa and password
123456 for the account.
1. Configure RADIUS-based MAC authentication on the device.
# Configure a RADIUS scheme.
<Device> system-view
[Device] radius scheme 2000
[Device-radius-2000] primary authentication 10.1.1.1 1812
[Device-radius-2000] primary accounting 10.1.1.2 1813
[Device-radius-2000] key authentication abc
[Device-radius-2000] key accounting abc
[Device-radius-2000] user-name-format without-domain
[Device-radius-2000] quit
# Apply the RADIUS scheme to ISP domain 2000 for authentication, authorization, and accounting.
[Device] domain 2000
[Device-isp-2000] authentication default radius-scheme 2000
[Device-isp-2000] authorization default radius-scheme 2000
[Device-isp-2000] accounting default radius-scheme 2000
[Device-isp-2000] quit

 Loading...
Loading...











