228
Source MAC address-based ARP attack detection configuration
example
Network requirements
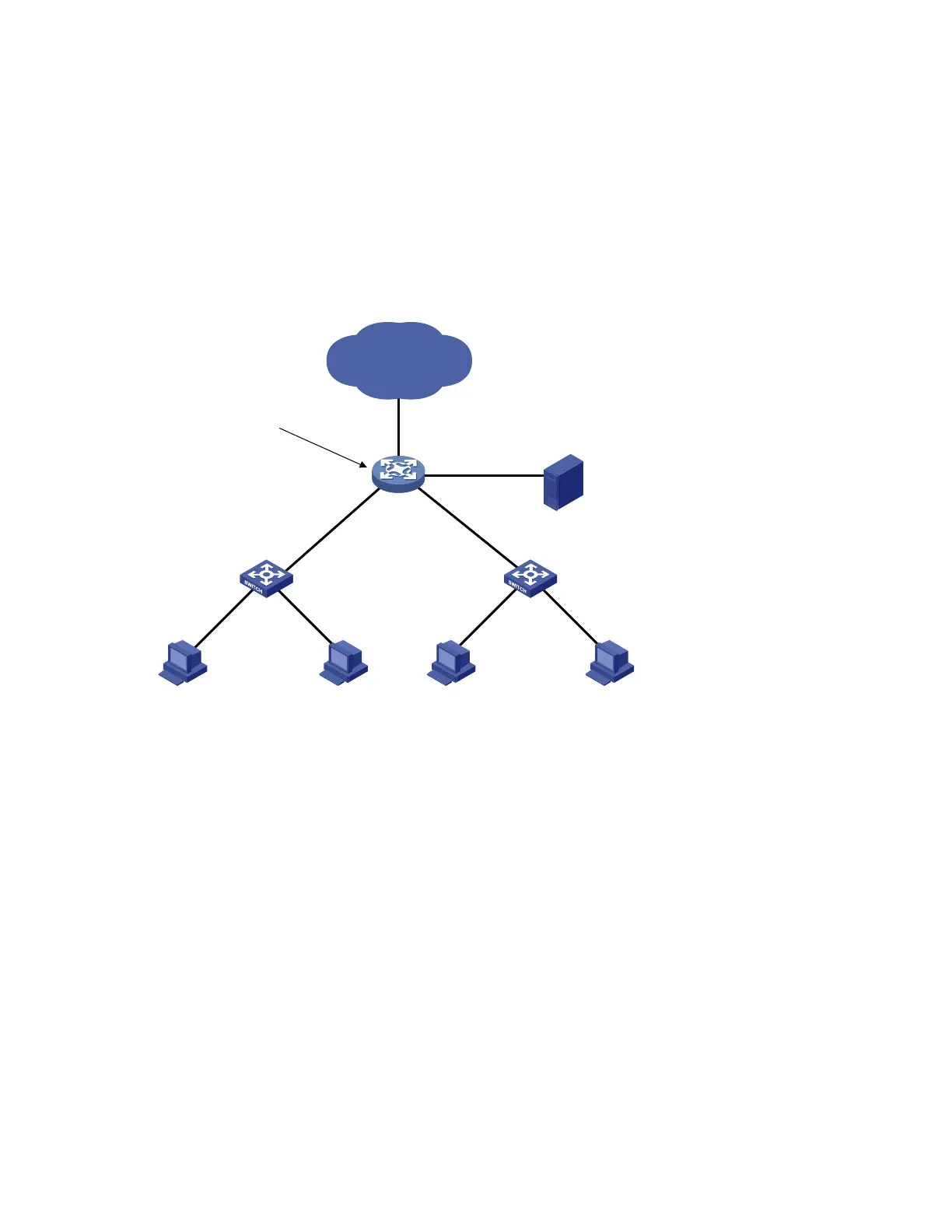
As shown in Figure 74, the hosts access the Internet through a gateway (Device). If malicious users send
a large number of ARP requests to the gateway, the gateway may crash and cannot process requests
from the clients. To solve this problem, configure source MAC address-based ARP attack detection on the
gateway.
Figure 74 Network diagram for configuring source MAC address-based ARP attack detection
IP network
Gateway
Device
Host A Host B Host C Host D
ARP attack protection
Server
0012-3f86-e 94c
Configuration considerations
An attacker may forge a large number of ARP packets by using the MAC address of a valid host as the
source MAC address. To prevent such attacks, configure the gateway as follows:
1. Enable source MAC address-based ARP attack detection, and specify the filter mode.
2. Set the threshold.
3. Set the age timer for detection entries.
4. Configure the MAC address of the server as a protected MAC address so that it can send ARP
packets.
Configuration procedure
# Enable source MAC address-based ARP attack detection, and specify the filter mode.
<Device> system-view
[Device] arp anti-attack source-mac filter
# Set the threshold to 30.
[Device] arp anti-attack source-mac threshold 30
# Set the age timer for detection entries to 60 seconds.

 Loading...
Loading...











