79
Table of Contents
Linksys
When an authentication method finishes successfully for a client
authenticated by a method with a lower priority, the attributes of the new
method are applied. When the new method fails, the client is left authorized
with the old method.
802.1x-Based Authentication
The device supports the 802.1x authentication mechanism, as described in
the standard, to authenticate and authorize 802.1x supplicants.
The 802.1x-based authenticator relays transparent EAP messages between
802.1x supplicants and authentication servers. The EAP messages between
supplicants and the authenticator are encapsulated into the 802.1x messages,
and the EAP messages between the authenticator and authentication servers
are encapsulated into the RADIUS messages.
This is described in the following:
Figure 1 802.1x-Based Authentication
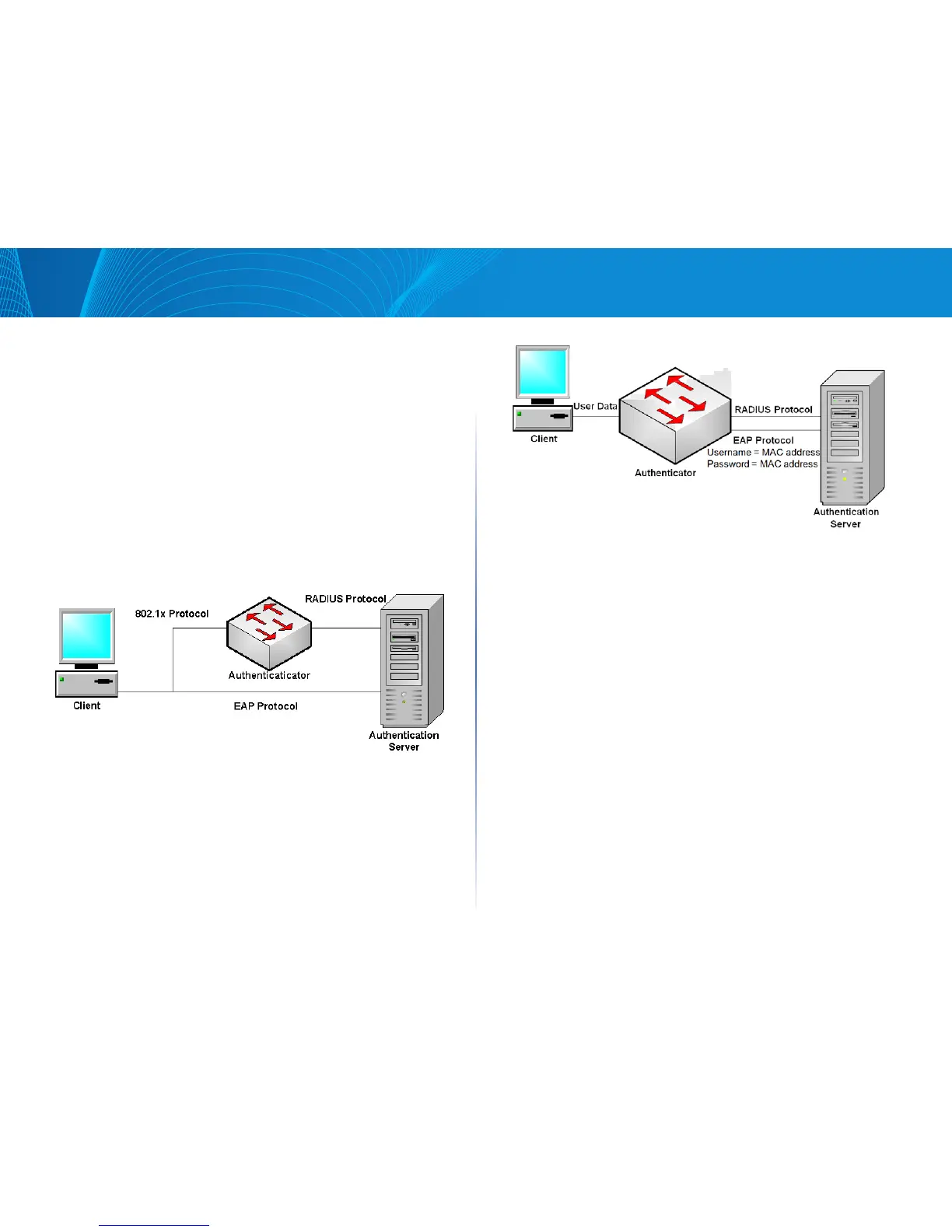
MAC-Based Authentication
MAC-based authentication is an alternative to 802.1X authentication that
allows network access to devices (such as printers and IP phones) that do not
have the 802.1X supplicant capability. MAC-based authentication uses the
MAC address of the connecting device to grant or deny network access.
In this case, the switch supports EAP MD5 functionality with the username
and password equal to the client MAC address, as shown below.
Figure 2 MAC-Based Authentication
The method does not have any specific configuration.
Guest VLAN
The guest VLAN provide access to services that do not require the subscribing
devices or ports to be 802.1X or MAC-based authenticated and authorized.
The guest VLAN is the VLAN that is assigned to an unauthorized client. You
can configure the guest VLAN and one or more VLANs to be unauthenticated
in the Security > Network Access Control > Feature Configuration page.
The guest VLAN, if configured, is a static VLAN with the following characteristics:
• It must be manually defined from an existing static VLAN.
• The guest VLAN cannot be used as the Voice VLAN.
Host Modes with Guest VLAN
The host modes work with guest VLAN in the following way:
• Single-Host and Multi-Host Mode
Untagged traffic and tagged traffic belonging to the guest VLAN arriving
on an unauthorized port are bridged via the guest VLAN. All other traffic
is discarded.
Dynamic VLAN Assignment
An authorized client can be assigned a VLAN by the RADIUS server, if this
option is enabled in the Port Authentication page. This is called either
Dynamic VLAN Assignment (DVA) or RADIUS-Assigned VLAN. In this guide, the
term RADIUSAssigned VLAN is used.
 Loading...
Loading...