77
Table of Contents
Linksys
• Key String—Enter the key string used for authenticating and encrypting
communication between the device and the RADIUS server. This key must
match the key configured on the RADIUS server. If Use Default is selected,
the device attempts to authenticate to the RADIUS server by using the
default Key String.
• Usage Type—Enter the RADIUS server authentication type. The options are:
• Login—RADIUS server is used for authenticating users that ask to
administer the device.
• 802.1X—RADIUS server is used for 802.1x authentication.
• All—RADIUS server is used for authenticating user that ask to
administer the device and for 802.1X authentication.
STEP 5 Click Apply. The RADIUS server definition is added to the Running
Configuration file of the device.
Network Access Control
This section describes 802.1x configuration. It covers the following topics:
• Overview
• Feature Configuration
• Port Authentication
• Authentication Hosts
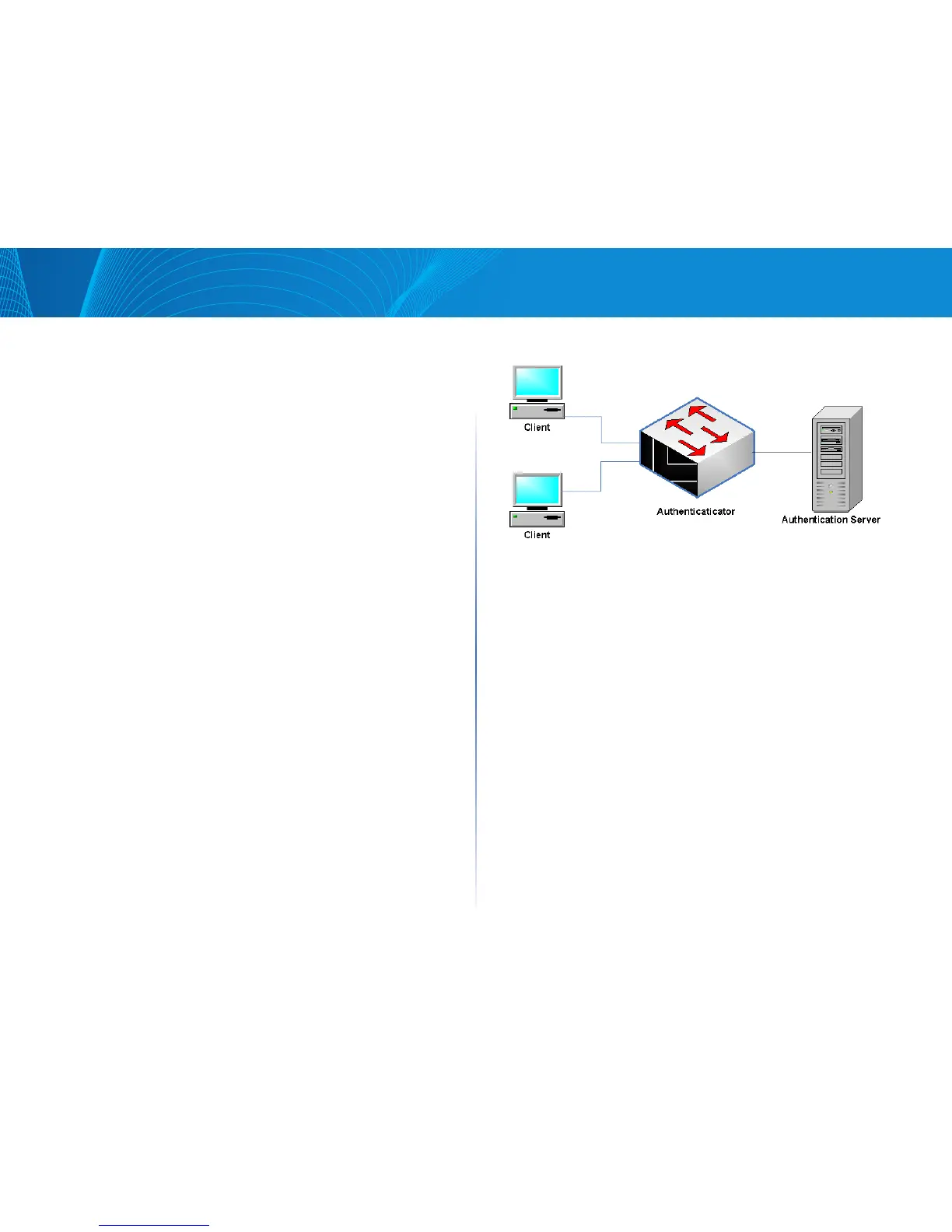
Overview
802.1x authentication restricts unauthorized clients from connecting to a LAN
through publicity-accessible ports. 802.1x authentication is a client-server
model. In this model, network devices have the following specific roles.
• Client or supplicant
• Authenticator
• Authentication server
This is described in the figure below:
A network device can be either a client/supplicant, an authenticator or both
per port.
Client or Supplicant
A client or supplicant is a network device that requests access to the LAN. The
client is connected to an authenticator.
If the client uses the 802.1x protocol for authentication, it runs the supplicant part
of the 802.1x protocol and the client part of the EAP protocol.
No special software is required on the client to use MAC-based
authentication.
Authenticator
An authenticator is a network device that provides network services and to
which supplicant ports are connected.
The following authentication modes on ports are supported:
• Multiple Host (802.1x)—Supports port-based authentication. If one client
is authenticated, all client devices attaching to the port have access.
• Multiple Sessions—Supports client-based authentication. Each client
must be authenticated individually before receiving access.
See Port Host Modes for more information.
The following authentication methods are supported:
• 802.1x-based—Supported in all authentication modes.

 Loading...
Loading...