Configuration manual for 2N IP intercoms
•
•
•
•
•
•
List of Parameters
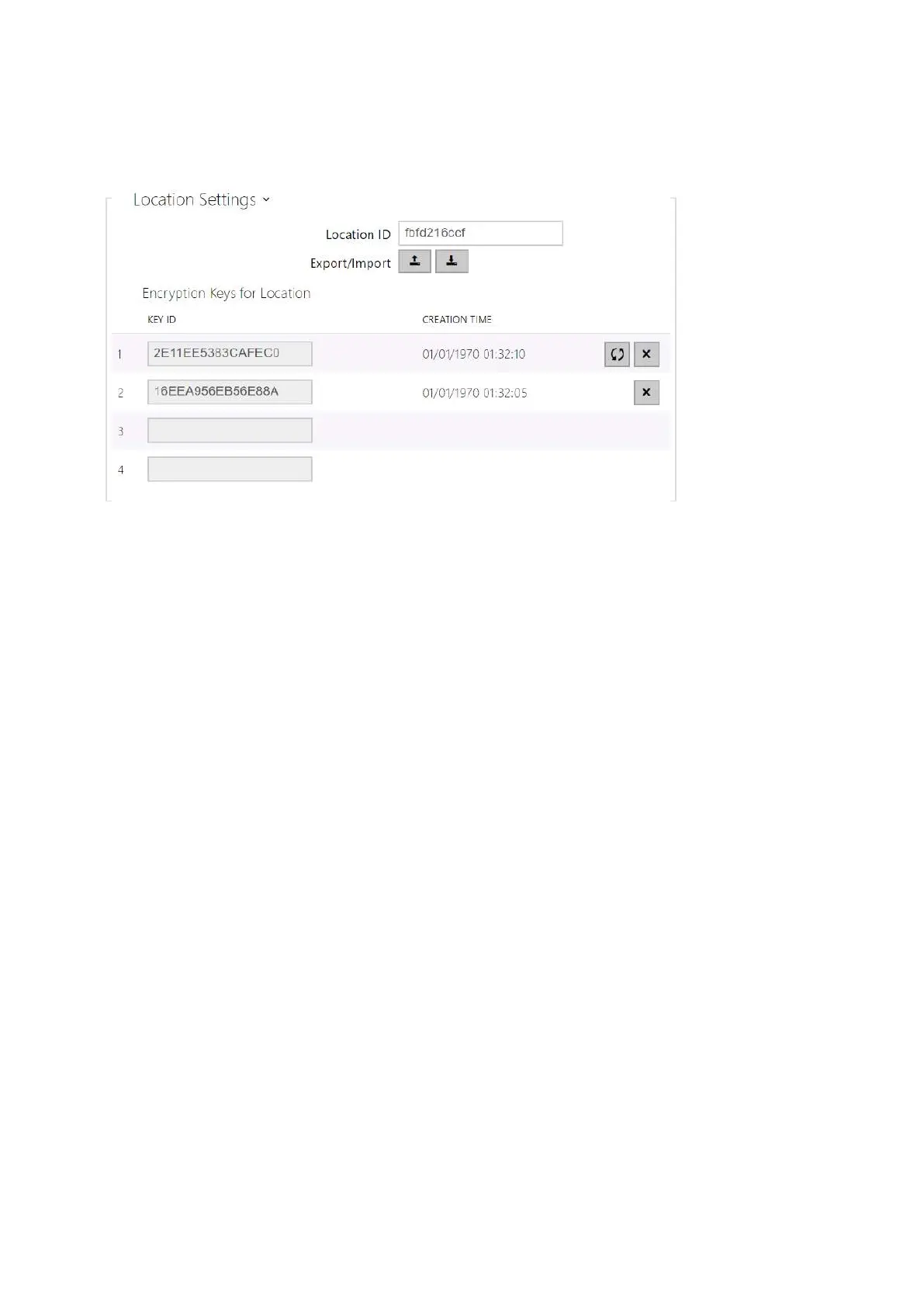
Location ID– set a unique identifier for the location in which the selected encryption key
set is valid.
Export– push the button to export the location ID and current encryption keys into a file.
Subsequently, the exported file can be imported to another device.
Import– push the button to import the location ID and current encryption keys from a file
exported from another intercom.
Restore Primary Key – by generating a new primary encryption key you delete the oldest
secondary key. Thus, the2NMobile Keyusers that still use this key will not be able to
authenticate themselves unless they have updated the encryption keys in their mobile
devices before deletion.The mobile device keys are updated at every use of the2NMobile
Keyapplication.
Delete Primary Key – delete the primary key to prevent the users that still use this key
from authentication.
Delete Secondary Key –the2NMobile Keyusers that still use this key will not be able to
authenticate themselves unless they have updated the encryption keys in their mobile
devices before deletion.The mobile device keys are updated at every use of the2NMobile
Keyapplication.
 Loading...
Loading...