The management connection is a secure, TLS-1.3-encrypted communication channel between itself and the
device. You do not need to run this traffic over an additional encrypted tunnel such as Site-to-Site VPN for
security purposes. If the VPN goes down, for example, you will lose your management connection, so we
recommend a simple management path.
Note
Data Interfaces
You can configure other interfaces after you connect the threat defense to the management center.
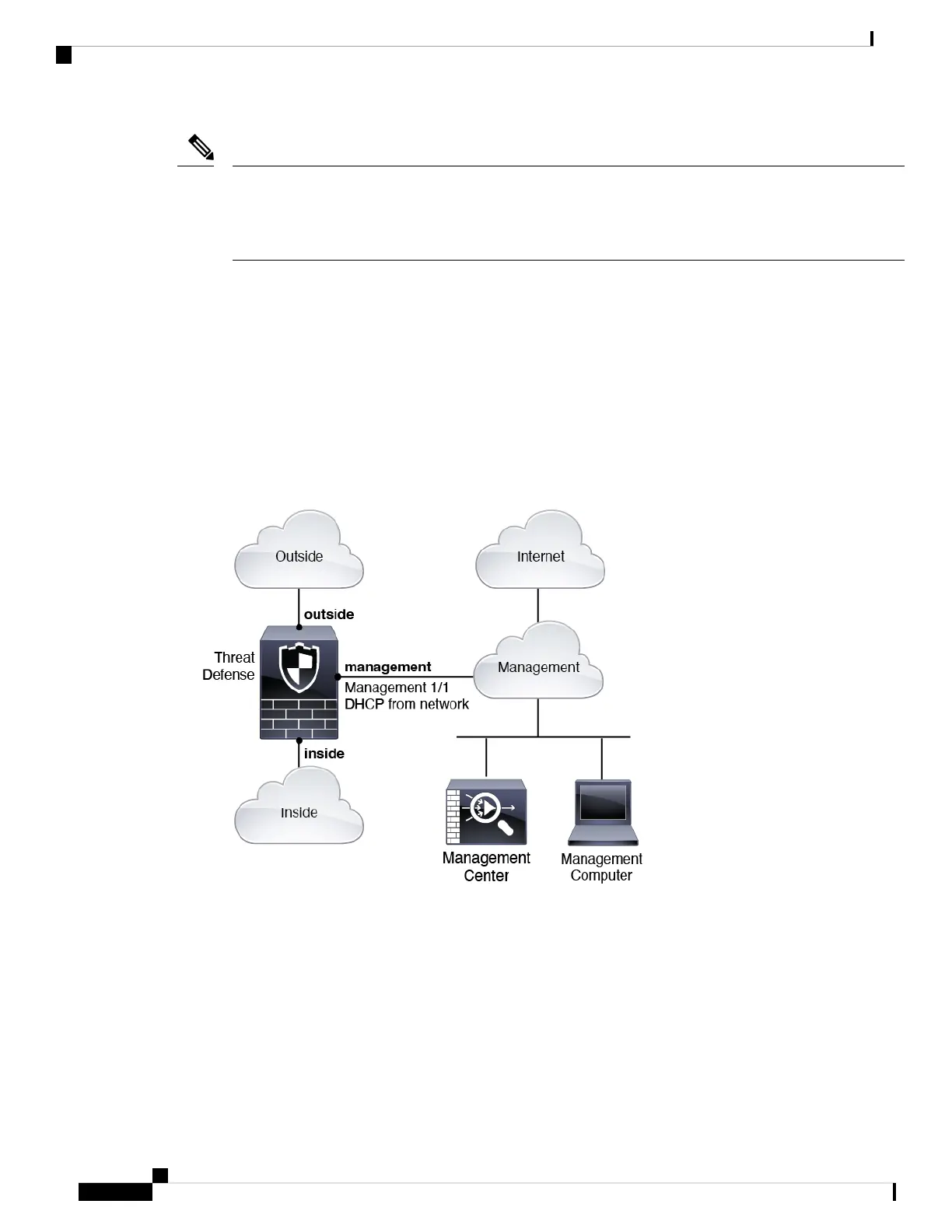
Typical Separate Management Network Deployment
The following figure shows a typical network deployment for the firewall where:
• The threat defense, management center, and management computer connect to the management network
• The management network has a path to the internet for licensing and updates.
Figure 1: Separate Management Network
Typical Edge Network Deployment
The following figure shows a typical network deployment for the firewall where:
• The inside interface acts as the internet gateway for Management and for the management center.
• Connects Management 1/1 to an inside interface through a Layer 2 switch.
• Connects the management center and management computer to the switch.
Cisco Firepower 2100 Getting Started Guide
8
Threat Defense Deployment with the Management Center
Review the Network Deployment

 Loading...
Loading...











