• Both the management center and threat defense initially communicate with the Cisco Security Cloud
and CDO to establish the management connection
• After initial establishment, CDO is used to reestablish the management connection if it is disrupted; for
example, if the threat defense IP address changes due to a new DHCP assignment, CDO will inform the
management center of the change.
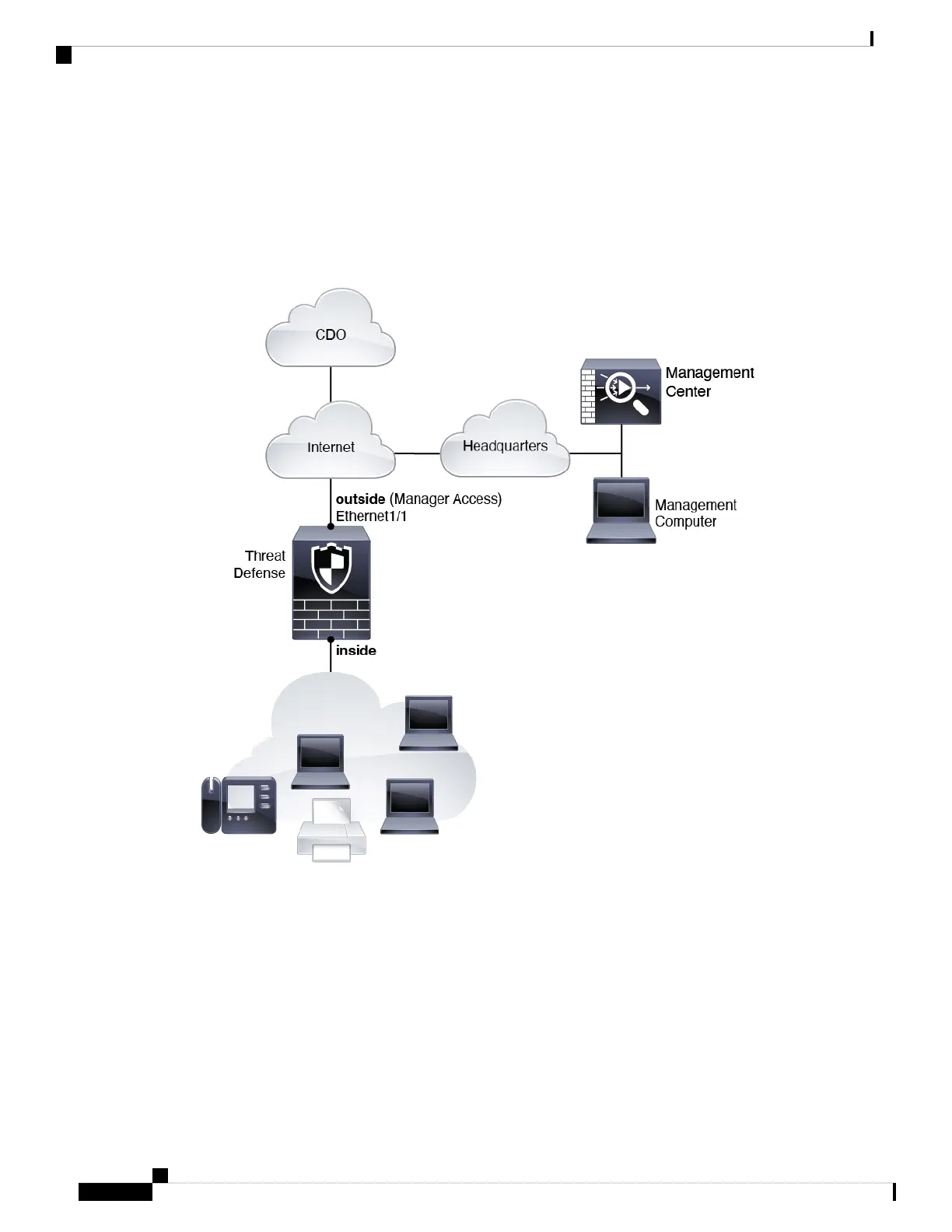
Figure 32: Low-Touch Provisioning Network
Manual Provisioning Network
The following figure shows a typical network deployment for the firewall where:
• The management center is at central headquarters.
• The threat defense uses the outside interface for manager access.
• Either the threat defense or management center needs a public IP address or hostname to allow to allow
the inbound management connection; you need to know this IP address for initial setup. You can also
optionally configure Dynamic DNS (DDNS) for the outside interface to accommodate changing DHCP
IP assignments.
Cisco Firepower 2100 Getting Started Guide
48
Threat Defense Deployment with a Remote Management Center
How Remote Management Works

 Loading...
Loading...











