For example, name the interface inside.
b) Check the Enabled check box.
c) Leave the Mode set to None.
d) From the Security Zone drop-down list, choose an existing inside security zone or add a new one by
clicking New.
For example, add a zone called inside_zone. Each interface must be assigned to a security zone and/or
interface group. An interface can belong to only one security zone, but can also belong to multiple interface
groups. You apply your security policy based on zones or groups. For example, you can assign the inside
interface to the inside zone; and the outside interface to the outside zone. Then you can configure your
access control policy to enable traffic to go from inside to outside, but not from outside to inside. Most
policies only support security zones; you can use zones or interface groups in NAT policies, prefilter
policies, and QoS policies.
e) Click the IPv4 and/or IPv6 tab.
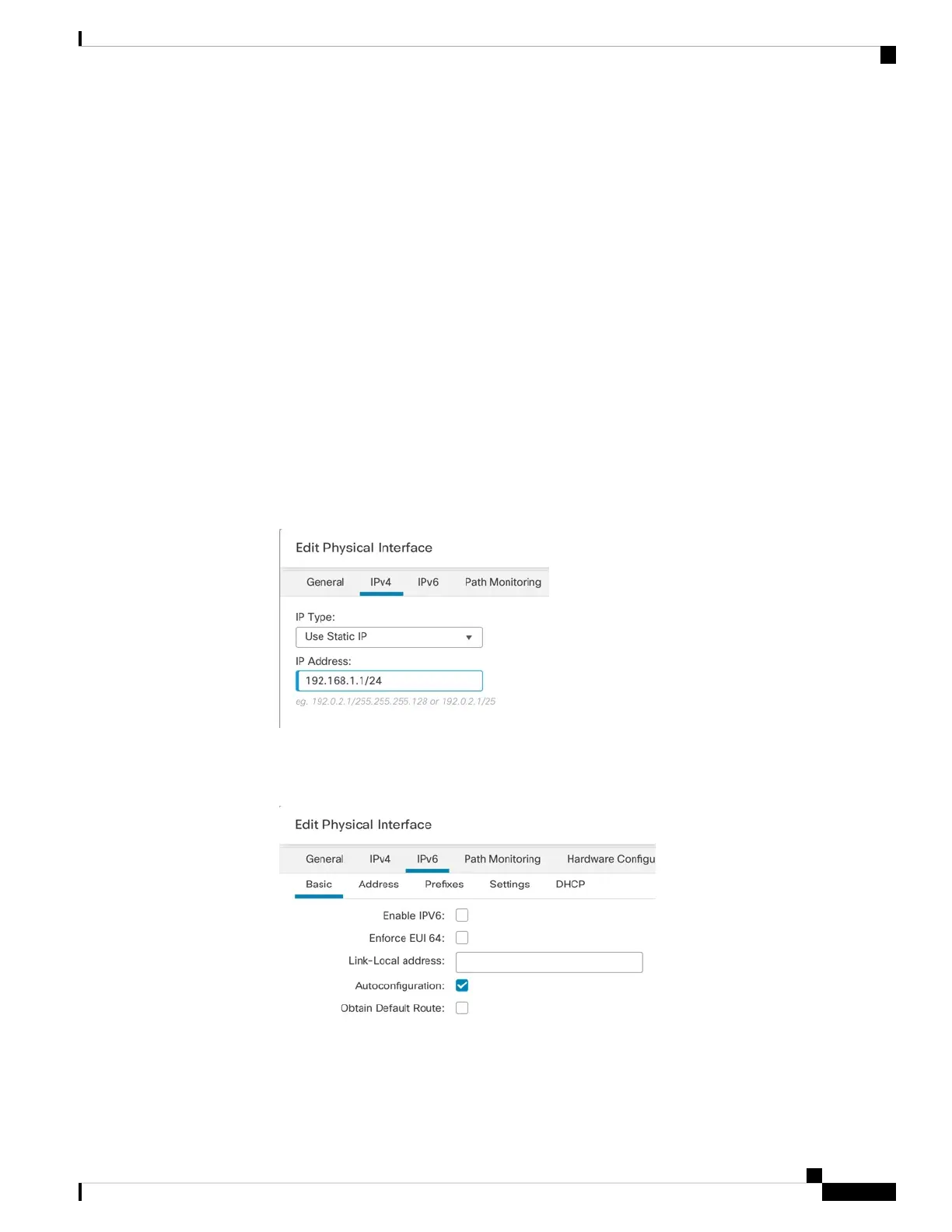
• IPv4—Choose Use Static IP from the drop-down list, and enter an IP address and subnet mask in
slash notation.
For example, enter 192.168.1.1/24
Figure 55: IPv4 Tab
• IPv6—Check the Autoconfiguration check box for stateless autoconfiguration.
Figure 56: IPv6 Tab
f) Click OK.
Cisco Firepower 2100 Getting Started Guide
81
Threat Defense Deployment with a Remote Management Center
Configure Interfaces

 Loading...
Loading...











