E-23
Cisco Security Appliance Command Line Configuration Guide
OL-10088-01
Appendix E Configuring an External Server for Authorization and Authentication
Configuring an External LDAP Server
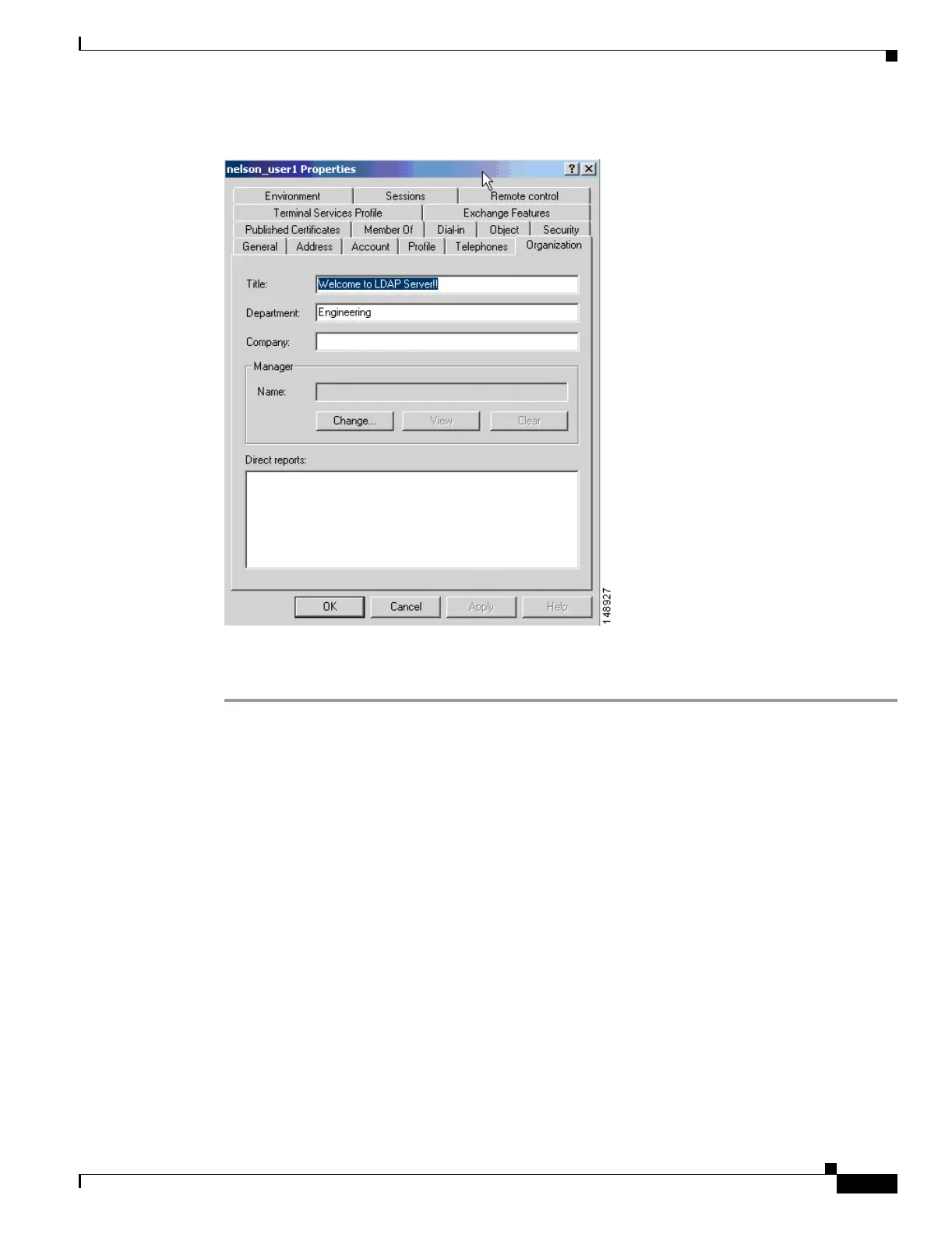
Figure E-5 The Organization Tab of the Active Directory Users and Computer Dialog
To configure this example, perform the following steps on the security appliance:
Step 1 Create an LDAP mapping table entry to map the Active Directory attribute department to the Cisco
attribute cVPN3000-IETF-Radius-Class as shown in the following example commands:
hostname(config)# ldap attribute-map ActiveDirectoryMapTable
hostname(config-ldap-attribute-map)# map-name department cVPN3000-IETF-Radius-Class
Step 2 Create a aaa-server record for the LDAP authentication server and use the ldap-base-dn to specify the
search location for the Active Directory user records as shown in the following example commands:
hostname(config)# aaa-server ldap-authenticate protocol ldap
hostname(config-aaa-server-group)# aaa-server ldap-authenticate host 10.1.1.4
hostname(config-aaa-server-host)# ldap-base-dn cn=Users,dc=frdevtestad,dc=local
hostname(config-aaa-server-host)# ldap-scope subtree
hostname(config-aaa-server-host)# ldap-naming-attribute cn
hostname(config-aaa-server-host)# ldap-login-password anypassword
hostname(config-aaa-server-host)# ldap-login-dn cn=Administrator,cn=Users,
dc=frdevtestad,dc=local
hostname(config-aaa-server-host)#
Step 3 Configure the name of the LDAP attribute map as shown in the following example command:
hostname(config-aaa-server-host)# ldap-attribute-map ActiveDirectoryMapTable
hostname(config-aaa-server-host)#

 Loading...
Loading...











