Vigor2920 Series User’s Guide
161
User Name This field is applicable when you select, PPTP or L2TP with or
without IPSec policy above.
Password This field is applicable when you select PPTP or L2TP with or
without IPSec policy above.
PPP Authentication This field is applicable when you select, PPTP or L2TP with or
without IPSec policy above. PAP/CHAP is the most common
selection due to wild compatibility.
VJ compression This field is applicable when you select PPTP or L2TP with or
without IPSec policy above. VJ Compression is used for
TCP/IP protocol header compression. Normally set to Yes to
improve bandwidth utilization.
IKE Authentication
Method
This group of fields is applicable for IPSec Tunnels and L2TP
with IPSec Policy.
Pre-Shared Key - Input 1-63 characters as pre-shared key.
Digital Signature (X.509) - Select one predefined Profiles set
in the VPN and Remote Access >>IPSec Peer Identity.
IPSec Security Method This group of fields is a must for IPSec Tunnels and L2TP with
IPSec Policy.
Medium Authentication Header (AH) means data will be authenticated,
but not be encrypted. By default, this option is active.
High (ESP-Encapsulating Security Payload)- means payload
(data) will be encrypted and authenticated. Select from below:
DES without Authentication -Use DES encryption algorithm
and not apply any authentication scheme.
DES with Authentication-Use DES encryption algorithm and
apply MD5 or SHA-1 authentication algorithm.
3DES without Authentication-Use triple DES encryption
algorithm and not apply any authentication scheme.
3DES with Authentication-Use triple DES encryption
algorithm and apply MD5 or SHA-1 authentication algorithm.
AES without Authentication-Use AES encryption algorithm
and not apply any authentication scheme.
AES with Authentication-Use AES encryption algorithm and
apply MD5 or SHA-1 authentication algorithm.
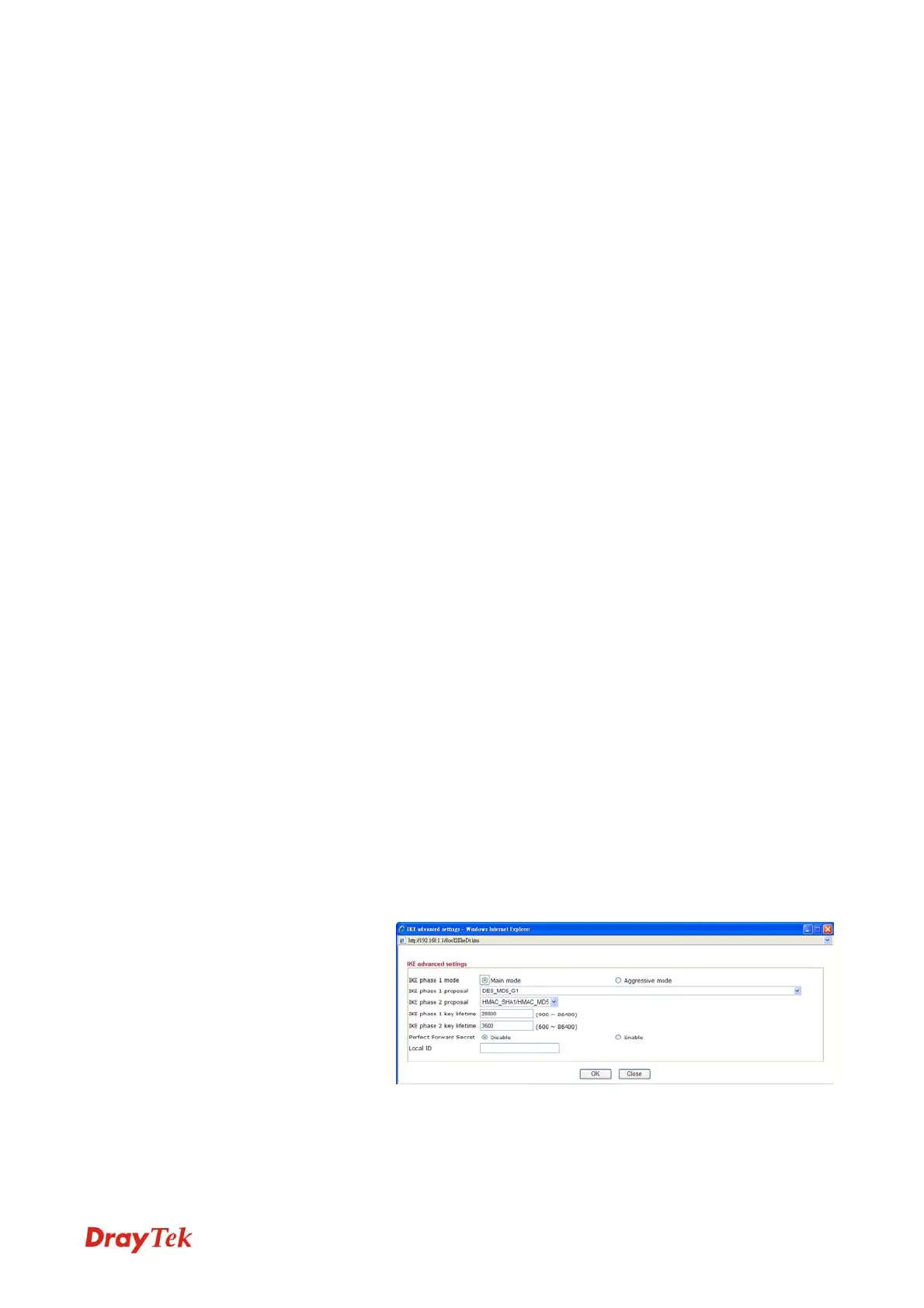
Advanced Specify mode, proposal and key life of each IKE phase,
Gateway, etc.
The window of advance setup is shown as below:
IKE phase 1 mode -Select from Main mode and Aggressive
mode. The ultimate outcome is to exchange security proposals
to create a protected secure channel. Main mode is more secure
than Aggressive mode since more exchanges are done in a
secure channel to set up the IPSec session. However, the
VoIPon www.voipon.co.uk sales@voipon.co.uk Tel: +44 (0)1245 808195 Fax: +44 (0)1245 808299
 Loading...
Loading...











