TA410/810 User Manual
43/63
Security Center
This chapter describes how to secure your TA410/810. It is strongly recommended
that users configure firewall and other security options on TA410/810 to prevent
the attack fraud and the system failure or calls loss.
Security Center
Alert Settings
AMI Settings
Certificates
Firewall Rules
IP Blacklist
Security Center
All the security settings including Firewall, Service, Port Settings in TA410/810 are
displayed in Security Center. Users could rapidly check and configure the relevant
security settings here.
1) Firewall
In the “Firewall” tab, users could check firewall configuration and alert settings. By
clicking the relevant button, you can enter the configuration page directly.
Figure 10-1 Security Center—Firewall
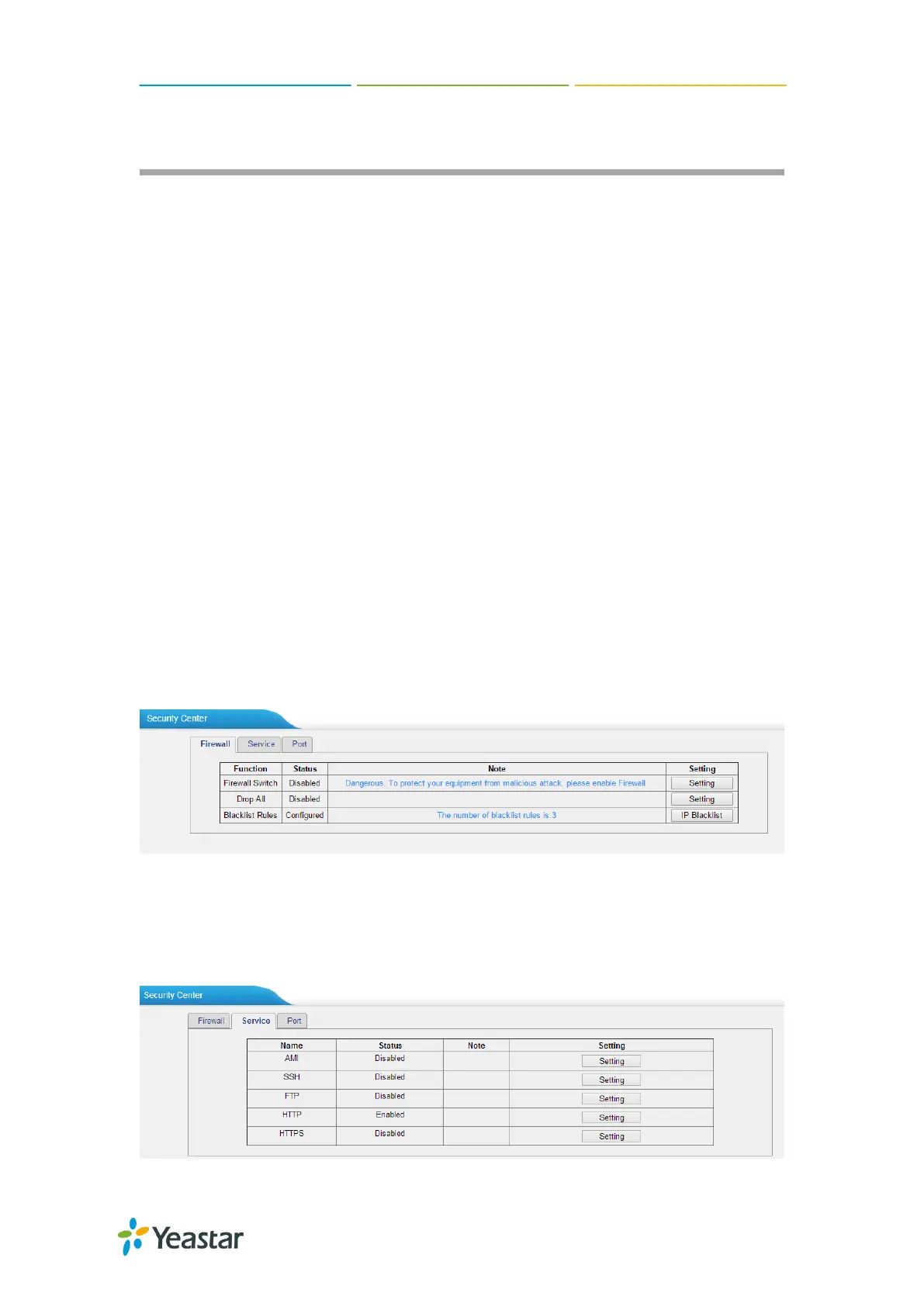
2) Service
In “Service” tab, you can check AMI/SSH status. For AMI/SSH, you can enter the
according page by clicking the button in “Setting” column.
Figure 10-2 Security Center—Service

 Loading...
Loading...











