3 Check the Enable box to the right of the entry to store settings.
4 Click the Apply button to activate the forwarding rules.
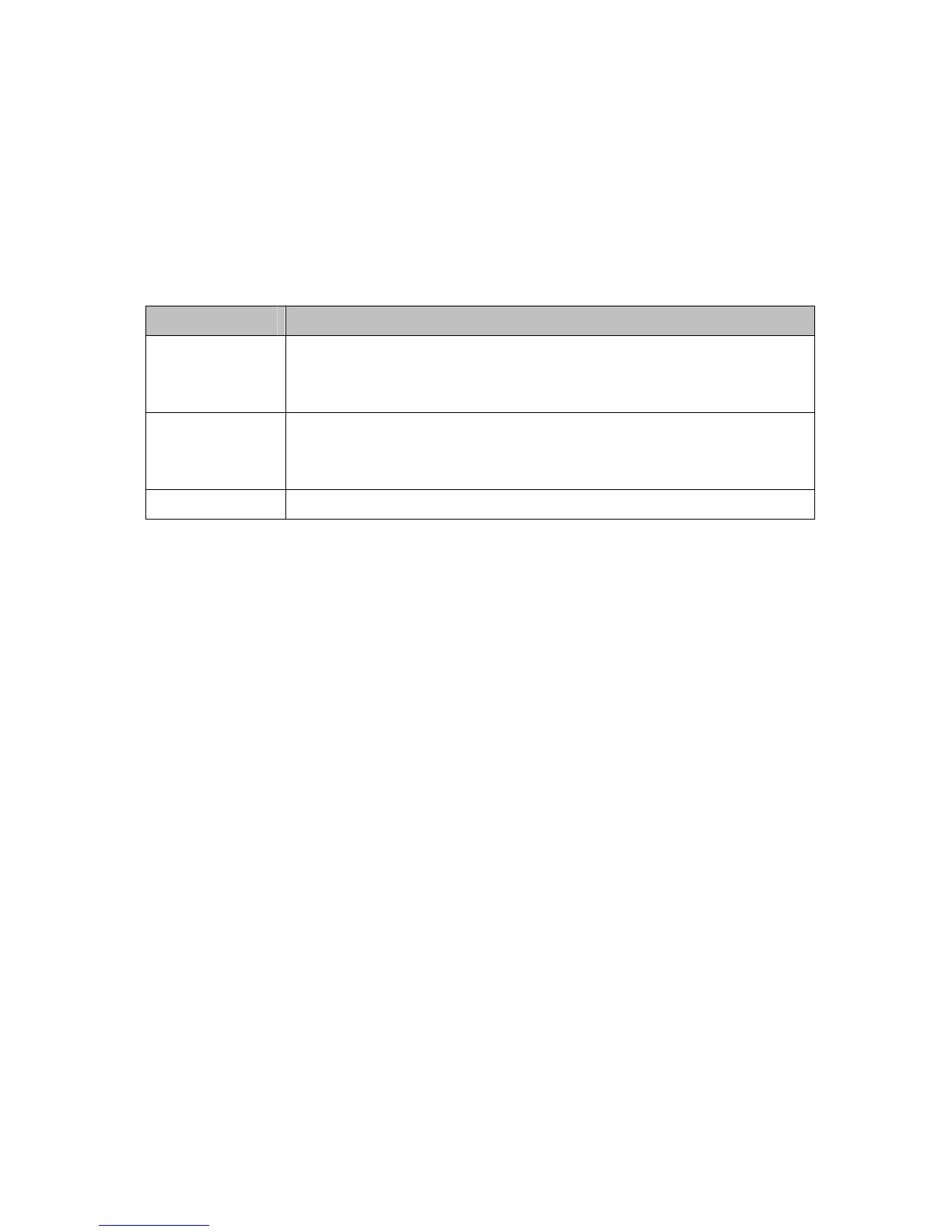
Table 14. Port Triggers Menu Option
Option Description
Trigger Range
(Start / End
Port)
Enter the trigger range (starting and ending ports) of the application for which
you want to enable port triggering. The application will send data from these
ports.
Target Range
(Start / End
Port)
Enter the target range (starting and ending ports) to open for the same
application. The application will receive data on these ports.
Protocol Select the protocol for this rule.
DMZ Host
The DMZ (De-militarized Zone) Host page allows you to configure a network device (e.g. a PC) to be
exposed or visible directly to the Internet. This may be used if an application doesn’t work with port
triggers. If you have an application that won’t run properly behind the NAT firewall, you can
configure it for unrestricted two-way Internet access by defining it as a virtual DMZ host. Adding a
client to the DMZ may expose your local network to various security risks because the client is not
protected, so use this option as a last resort.
To access the DMZ Host page:
1 Click Advanced in the menu bar.
2 Then click the DMZ Host submenu.
Figure 20 shows an example of the menu.
50
 Loading...
Loading...