10-3
Catalyst 6500 Series Switch and Cisco 7600 Series Router Firewall Services Module Configuration Guide
OL-6392-01
Chapter 10 Controlling Network Access with Access Control Lists
Access Control List Overview
ACLs to allow ICMP in both directions (by applying ACLs to the source and destination interfaces), or
you need to enable the ICMP inspection engine (see the “ICMP Inspection Engine” section on
page 13-10). The ICMP inspection engine treats ICMP sessions as stateful connections.
You can apply one ACL of each type to each direction of an interface. You can also apply the same ACLs
on multiple interfaces.
To control network access for IP traffic, perform the following task:
• Create and apply the ACL according to the “Adding an Extended Access Control List” section on
page 10-13.
Allowing Special Traffic through the Transparent Firewall
In routed firewall mode, some types of traffic are blocked even if you allow them in an ACL, including
unsupported dynamic routing protocols, DHCP (unless you configure DHCP relay), and multicast
traffic. Transparent firewall mode can allow any IP traffic through. Because these special types of traffic
are connectionless, you need to apply an ACL to both interfaces, so returning traffic is allowed through.
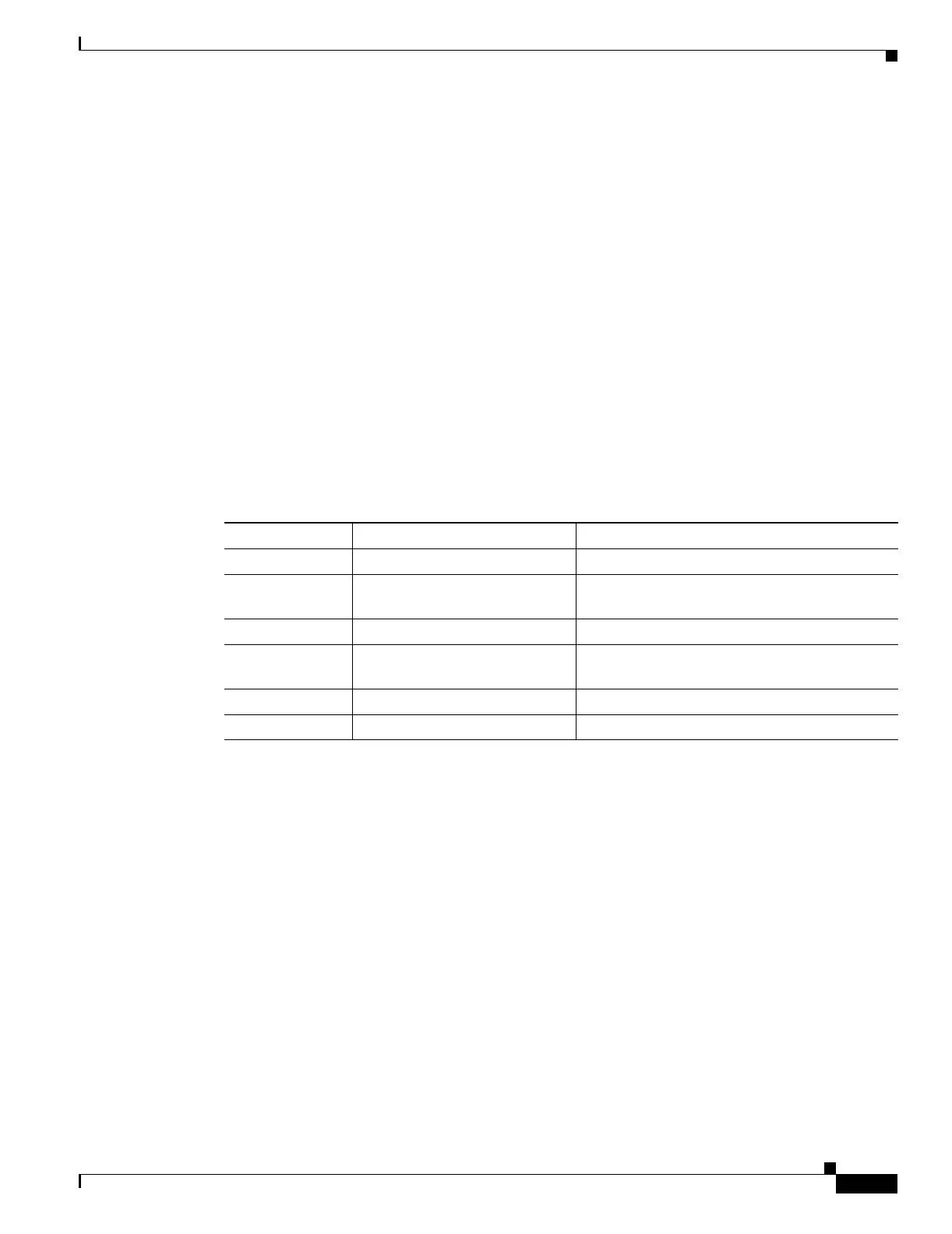
Table 10-2 lists common traffic types that you can allow through the transparent firewall. See
Appendix D, “Addresses, Protocols, and Ports Reference,” for more protocols and ports.
Identifying Traffic for AAA rules (Extended)
ACLs can be used with AAA in several ways.
• To identify traffic for network access authorization using a TACACS+ server, perform the following
tasks:
a. Add the ACL using the “Adding an Extended Access Control List” section on page 10-13.
Permit entries in the ACL mark matching traffic for authorization, while deny entries exclude
matching traffic from authorization.
b. Apply the ACL using the aaa authorization match command in the “Configuring TACACS+
Authorization” section on page 12-24.
Table 10-2 Transparent Firewall Special Traffic
Traffic Type Protocol or Port Notes
BGP
1
1. Border Gateway Protocol
TCP port 179 —
DHCP
2
2. Dynamic Host Configuration Protocol
UDP ports 67 and 68 If you enable the DHCP server, then the FWSM
does not pass DHCP packets.
EIGRP
3
3. Enhanced Interior Gateway Routing Protocol
Protocol 88 —
Multicast streams The UDP ports vary depending
on the application.
Multicast streams are always destined to a
Class D address (224.0.0.0 to 239.x.x.x).
OSPF Protocol 89 —
RIP (v1 or v2) UDP port 520 —

 Loading...
Loading...

















