13-2
Catalyst 6500 Series Switch and Cisco 7600 Series Router Firewall Services Module Configuration Guide
OL-6392-01
Chapter 13 Configuring Application Protocol Inspection
Inspection Engine Overview
When you enable application inspection for a service that uses dynamically assigned ports, the FWSM
monitors sessions to identify the dynamic port assignments, and permits data exchange on these ports
for the duration of the specific session.
Inspection Limitations
See the following limitations for application protocol inspection:
• You can configure up to 32 inspection engines per context. This limit includes the following
inspection engines that are enabled by default, making the total number of configurable inspection
engines 27: TFTP, Sun RPC over UDP, NetBIOS NameServer, XDMCP, and CUSeeMe. The
OraServ and RealAudio inspection engines, which are also enabled by default, do not affect this
limit.
• State information for multimedia sessions that require inspection are not passed over the state link
for stateful failover.
• For fragmented IP packets, only the first fragment is inspected.
• For segmented TCP packets, if messages are divided between segments, the FWSM cannot inspect
the packets.
• Some inspection engines do not support PAT, NAT, policy NAT, outside NAT, or NAT between same
security interfaces. See “Inspection Support” for more information about NAT support.
• DNS fixups are limited to 4000 per second.
Inspection Support
Table 13-1 describes the inspection engines supported by the FWSM and whether they are compatible
with Network Address Translation (NAT), Port Address Translation (PAT), outside NAT, or NAT
between same security interfaces. If a inspection engine does not support outside NAT, consider using
the alias command instead of outside NAT. See the Catalyst 6500 Series Switch and Cisco 7600 Series
Router Firewall Services Module Command Reference for more information about the alias command.
Inspection engines that are enabled for the default port by default are in bold.
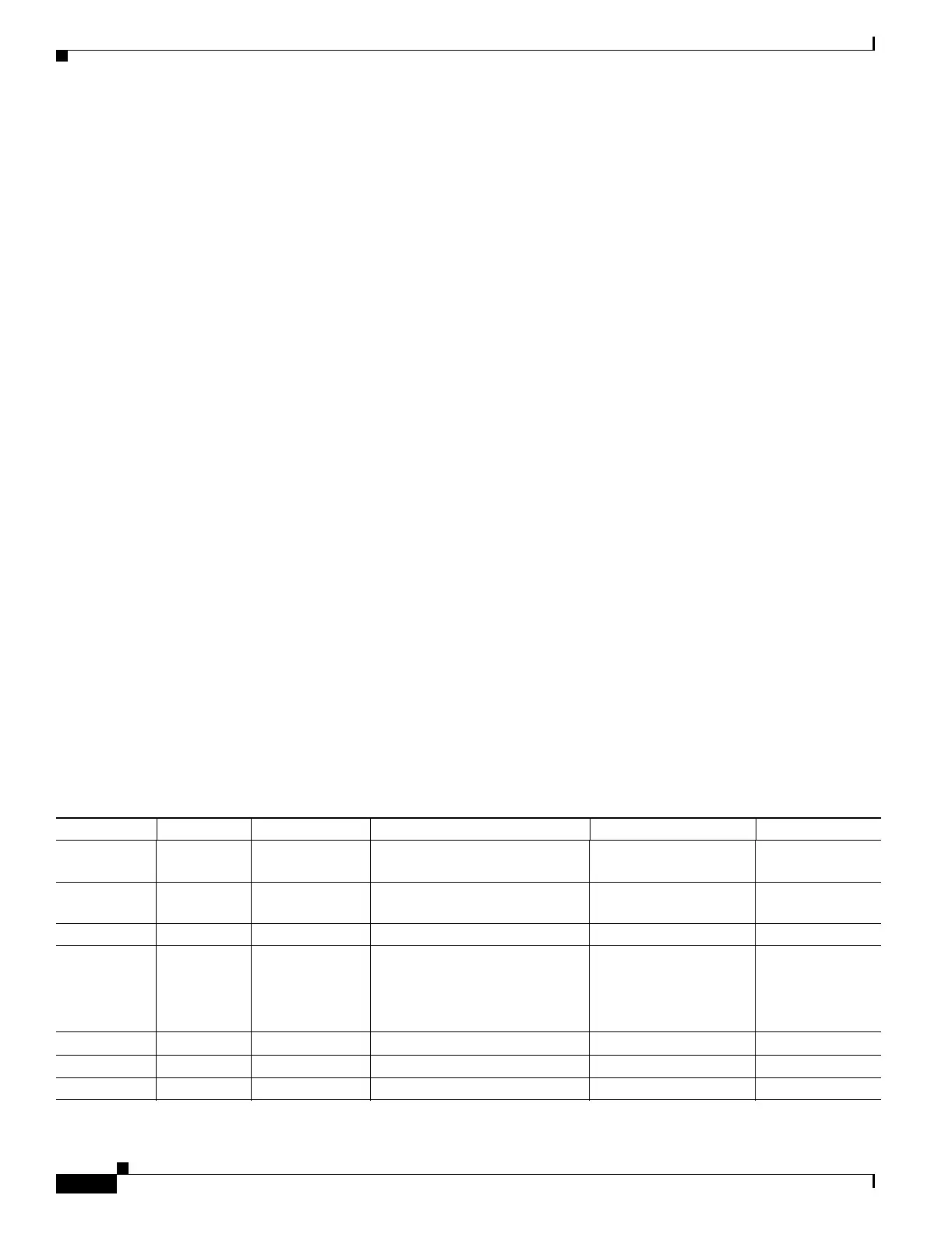
Table 13-1 Inspection Engine Support
Application
1
Configurable Default Port NAT Limitations Comments Standards
2
CUSeeMe No UDP/7648 No NAT or PAT. Use NAT
identity or NAT exemption only.
——
DNS over
UDP
Yes UDP/53 No NAT support is available for
name resolution through WINS.
No PTR records are
changed.
RFC 1123
FTP Yes TCP/21 — — RFC 1123
H.323 H.225
and RAS
Yes TCP/1720
UDP/1718-1719
No outside NAT. Use the alias
command.
No NAT on same security
interfaces.
Does not support
segmented messages.
ITU-T H.323,
H.245, H225.0,
Q.931, Q.932
HTTP Yes TCP/80 — — RFC 2616
ICMP Yes — — — —
ICMP error Yes — — — —

 Loading...
Loading...

















