13-3
Catalyst 6500 Series Switch and Cisco 7600 Series Router Firewall Services Module Configuration Guide
OL-6392-01
Chapter 13 Configuring Application Protocol Inspection
Inspection Engine Overview
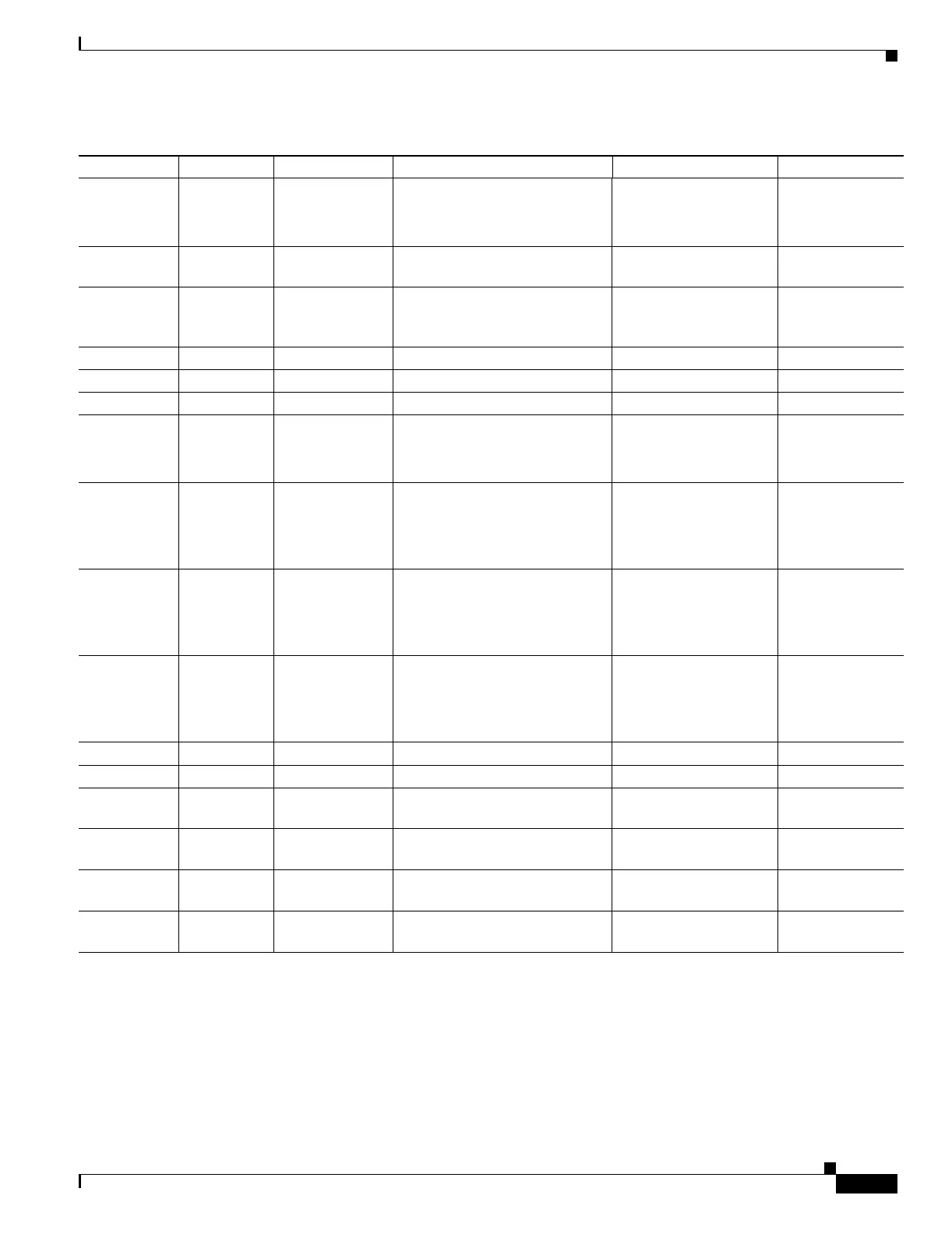
ILS (LDAP) Yes TCP/389 No outside NAT. Use the alias
command.
No PAT.
——
MGCP Yes UDP/2427,
2727
No NAT or PAT. Use NAT
identity or NAT exemption only.
— RFC2705bis-05
NetBIOS
Name Server
over IP
No UDP/137-138 — — —
OraServ No UDP/1525 — —
RealAudio No UDP/7070 — —
RSH Yes TCP/514 No PAT. — Berkeley UNIX
RTSP Yes TCP/554 No PAT.
No outside NAT. Use the alias
command.
No handling for HTTP
cloaking.
RFC 2326, RFC
2327, RFC 1889
SIP TCP Yes TCP/5060 No outside NAT. Use the alias
command.
No NAT on same security
interfaces.
— RFC 2543
SIP UDP Yes UDP/5060 No outside NAT. Use the alias
command.
No NAT on same security
interfaces.
— RFC 2543
SKINNY
(SCCP)
Yes TCP/2000 No outside NAT. Use the alias
command.
No NAT on same security
interfaces.
Does not handle TFTP
uploaded Cisco IP
Phone configurations.
—
SMTP Yes TCP/25 — — RFC 821, 1123
SQL*Net Yes TCP/1521 (v1) No policy NAT. v1 and v2. —
Sun RPC
over UDP
No UDP/111 No NAT or PAT. Use NAT
identity or NAT exemption only.
——
Sun RPC
over TCP
Yes TCP/111 No NAT or PAT. Use NAT
identity or NAT exemption only.
——
TFTP No UDP/69 Payload IP address not
translated.
— RFC 1350
XDMCP No UDP/177 No NAT or PAT. Use NAT
identity or NAT exemption only.
——
1. Inspection engines that are enabled by default for the default port are in bold.
2. The FWSM is in compliance with these standards, but it does not enforce compliance on packets being inspected. For example, FTP commands are
supposed to be in a particular order, but the FWSM does not enforce the order.
Table 13-1 Inspection Engine Support (continued)
Application
1
Configurable Default Port NAT Limitations Comments Standards
2

 Loading...
Loading...

















