12-5
Catalyst 6500 Series Switch and Cisco 7600 Series Router Firewall Services Module Configuration Guide
OL-6392-01
Chapter 12 Configuring AAA
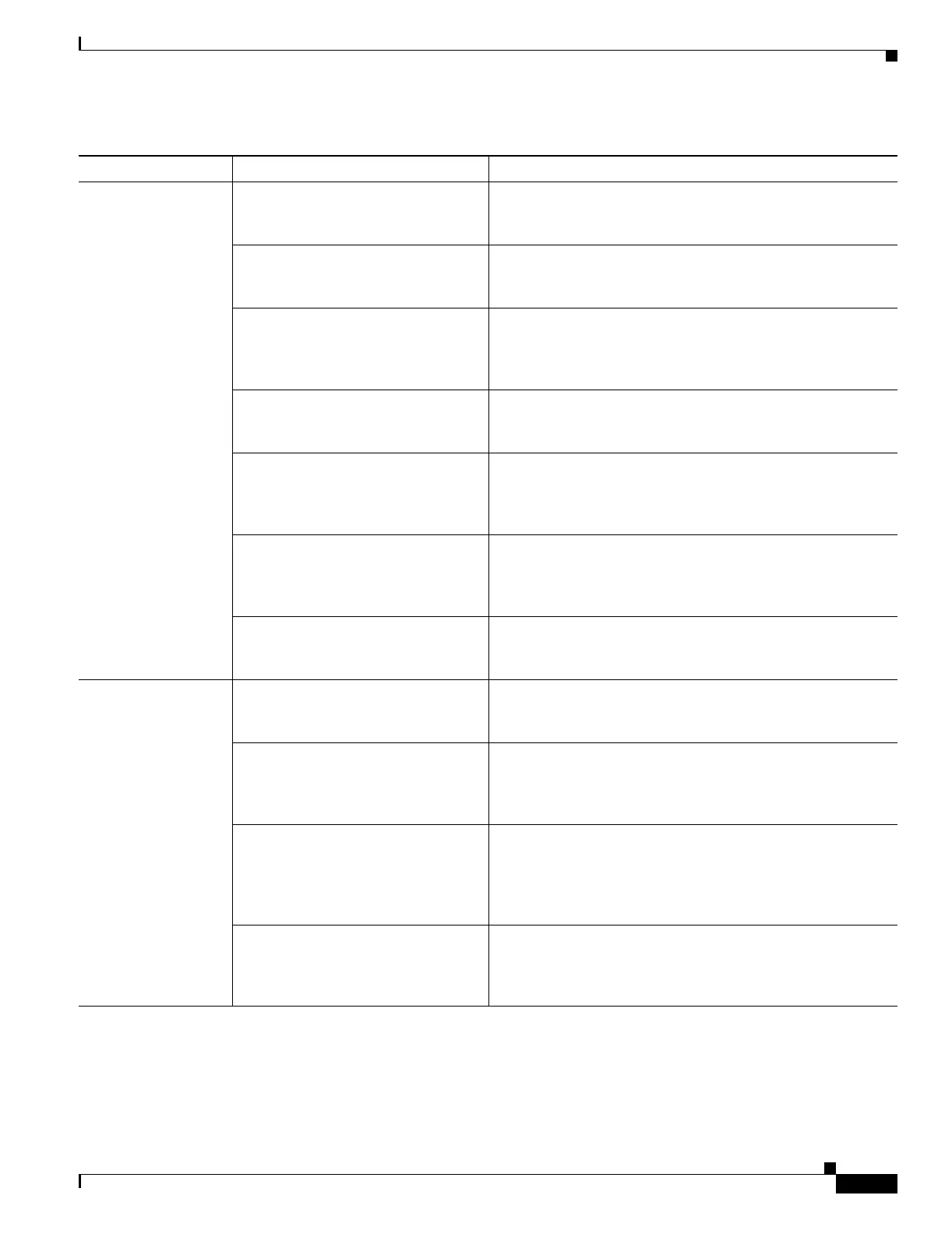
AAA Overview
TACACS+ User authentication for CLI access When a user attempts to access the FWSM for Telnet, SSH,
or HTTP, the FWSM consults the TACACS+ server for the
username and password.
User authentication for the enable
command
When a user attempts to access the enable command, the
FWSM consults the TACACS+ server for the username and
password.
User authentication for network
access
When a user attempts to access networks through the FWSM,
and the traffic matches an authentication statement, the
FWSM consults the TACACS+ server for the username and
password.
User authorization for network access When a user matches an authorization statement on the
FWSM after authenticating, the FWSM consults the
TACACS+ server for the user’s access privileges.
User authorization for management
commands.
On the TACACS+ server, configure the commands that a user
or group can use after they authenticate for CLI access. Every
command that a user enters at the CLI is checked with the
TACACS+ server.
VPN client authentication When you configure VPN management access using the
VPN client, you can use a TACACS+ server to authenticate
the client. (See the “Configuring VPN Client Access” section
on page 11-7 for more information.)
Accounting for network access per
user or IP address
You can configure the FWSM to send accounting information
to the TACACS+ server about any traffic that passes through
the FWSM.
Local database
1
User authentication for CLI access When a user attempts to access the FWSM for Telnet, SSH,
or HTTP, the FWSM consults the local user database for the
username and password.
User authentication for the enable or
login command
When a user attempts to access the enable or login command,
the FWSM consults the local user database for the username
and password. You do not need to configure login user
authentication; it is on by default.
User authorization for management
commands.
When a user authenticates with the enable command (or logs
in with the login command), the FWSM places that user in the
privilege level defined by the local database. You can
configure each command to belong to privilege level between
0 and 15 on the FWSM.
VPN client authentication When you configure VPN management access using the
VPN client, you can use the local database to authenticate the
client. (See the “Configuring VPN Client Access” section on
page 11-7 for more information.)
1. The local database can act as a fallback method for each of these functions if the AAA server is unavailable.
Table 12-1 AAA Server and Local Database Support (continued)
Server/Database Type Functionality Description

 Loading...
Loading...

















