4-15
Catalyst 6500 Series Switch and Cisco 7600 Series Router Firewall Services Module Configuration Guide
OL-6392-01
Chapter 4 Configuring the Firewall Mode
Firewall Mode Overview
4. If the destination MAC address is in its table, the FWSM forwards the packet out of the inside
interface on VLAN 200.
If the destination MAC address is not in the FWSM table, the FWSM attempts to discover the MAC
address by sending an ARP request and a ping. The first packet is dropped.
5. When the website responds to the request, the packet goes through the FWSM, and because the
session is already established, the packet bypasses the many lookups associated with a new
connection.
6. The FWSM forwards the packet to the outside user.
An Outside User Attempts to Access an Inside Host
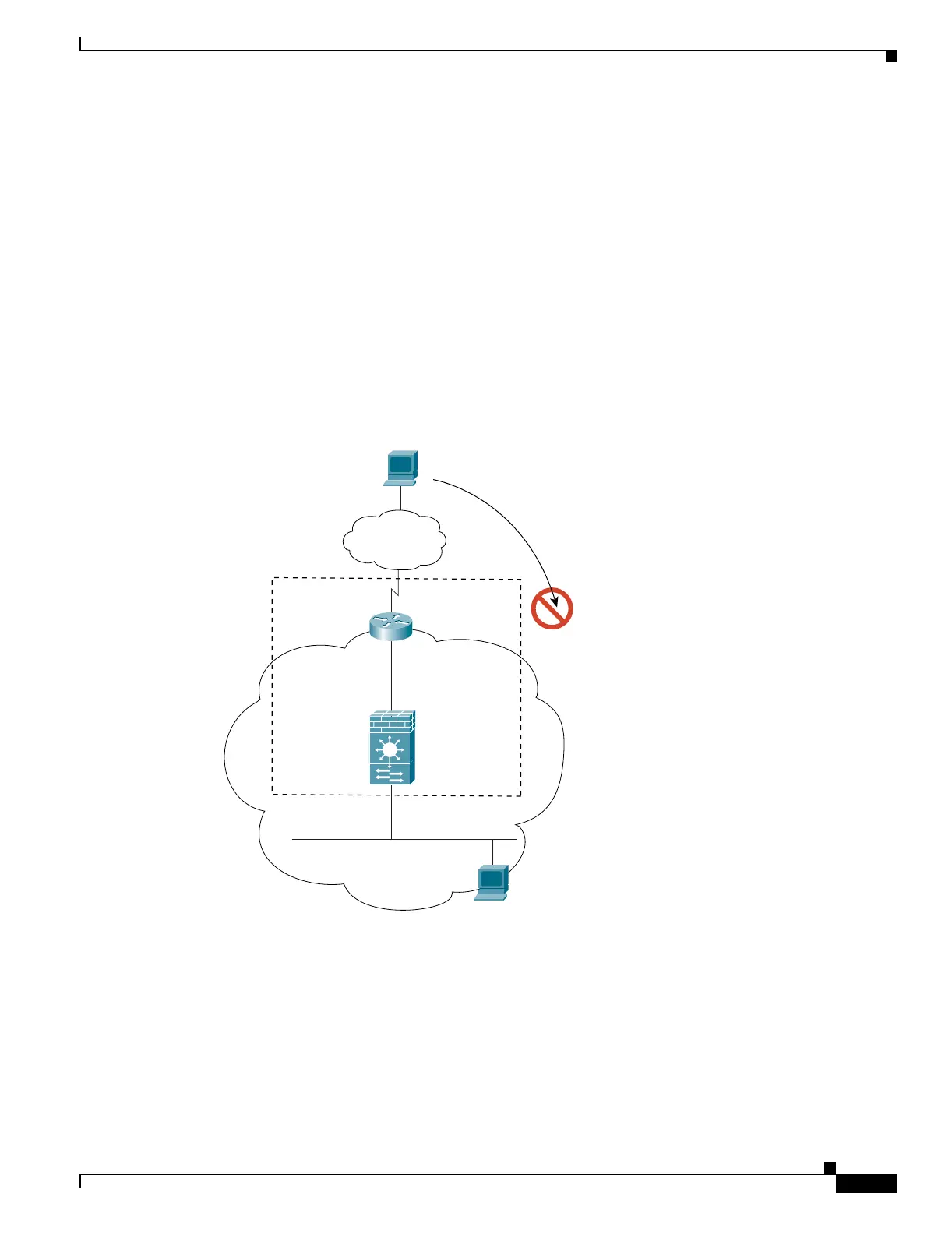
Figure 4-5 shows an outside user attempting to access a host on the inside network.
Figure 4-11 Outside to Inside
The steps below describe how data moves through the FWSM (see Figure 4-5):
1. A user on the outside network attempts to reach an inside host.
2. The FWSM receives the packet and, because it is a new session, it verifies if the packet is allowed
according to the terms of the security policy (ACLs, filters, AAA).
3. The packet is denied, and the FWSM drops the packet.
4. If the outside user is attempting to attack the inside network, the FWSM employs many technologies
to determine if a packet is valid for an already established session. See the “Other Protection
Features” section on page 1-6 for more information.
Switch
FWSM
209.165.201.6
Host
VLAN 100
VLAN 200
Internet
209.165.201.2
Host
209.165.201.3
104695
 Loading...
Loading...

















