27-18
Cisco Security Appliance Command Line Configuration Guide
OL-10088-01
Chapter 27 Configuring IPSec and ISAKMP
Configuring IPSec
To complete the security appliance configuration in the example network, we assign mirror crypto maps
to Security Appliances B and C. However, because security appliances ignore deny ACEs when
evaluating inbound, encrypted traffic, we can omit the mirror equivalents of the deny A.3 B
and deny A.3 C ACEs, and therefore omit the mirror equivalents of Crypto Map 2. So the configuration
of cascading ACLs in Security Appliances B and C is unnecessary.
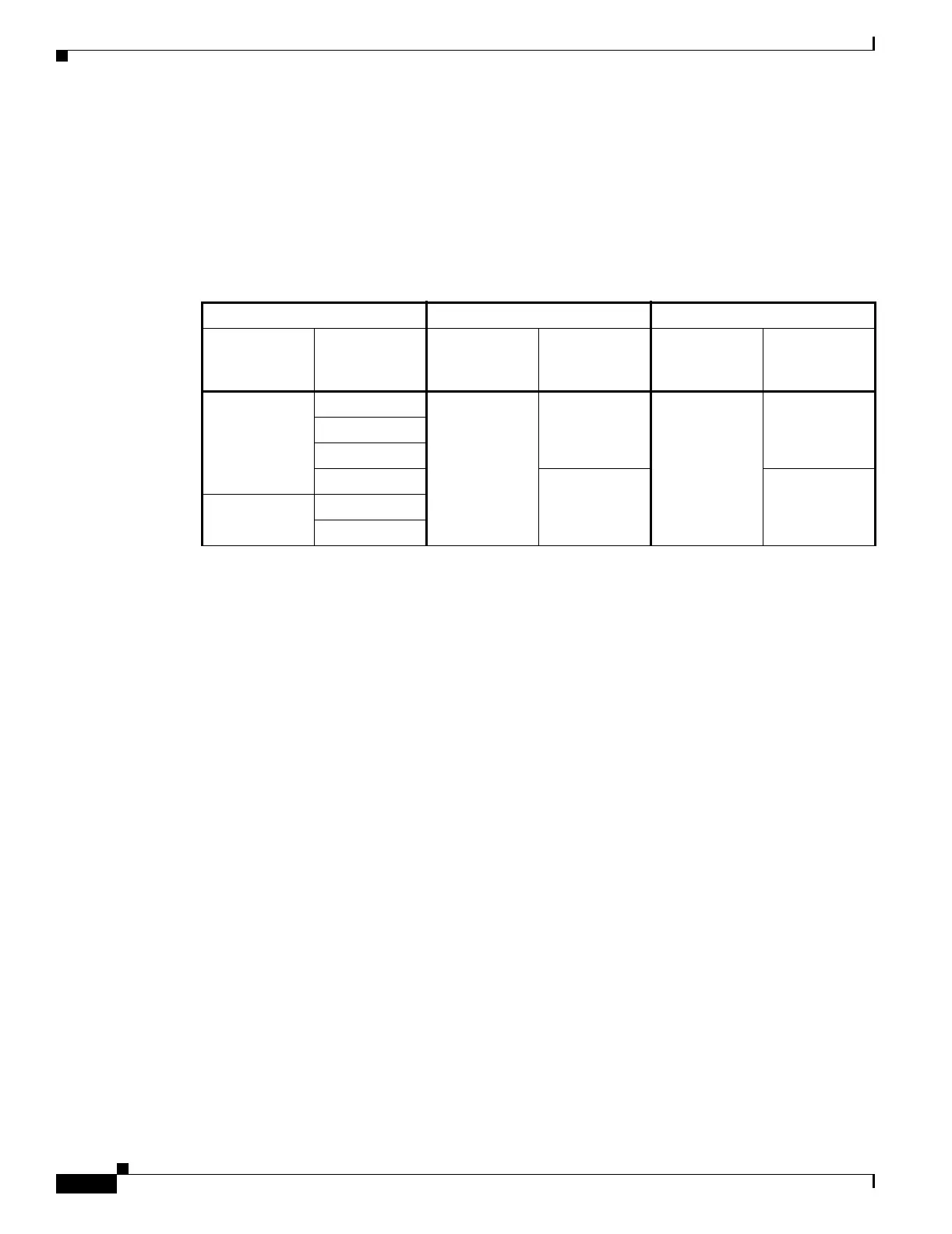
Table 27-3 shows the ACLs assigned to the crypto maps configured for all three security appliances in
Figure 27-1.
Figure 27-3 maps the conceptual addresses shown in Figure 27-1 to real IP addresses.
Table 27-3 Example Permit and Deny Statements (Conceptual)
Security Appliance A Security Appliance B Security Appliance C
Crypto Map
Sequence
No. ACE Pattern
Crypto Map
Sequence
No. ACE Pattern
Crypto Map
Sequence
No. ACE Pattern
1 deny A.3 B 1 permit B A 1 permit C A
deny A.3 C
permit A B
permit A C permit B C permit C B
2 permit A.3 B
permit A.3 C

 Loading...
Loading...











