28-4
Cisco Security Appliance Command Line Configuration Guide
OL-10088-01
Chapter 28 Configuring L2TP over IPSec
Configuring L2TP over IPSec Connections
Step 8 Configure the PPP authentication protocol using the authentication type command from tunnel group
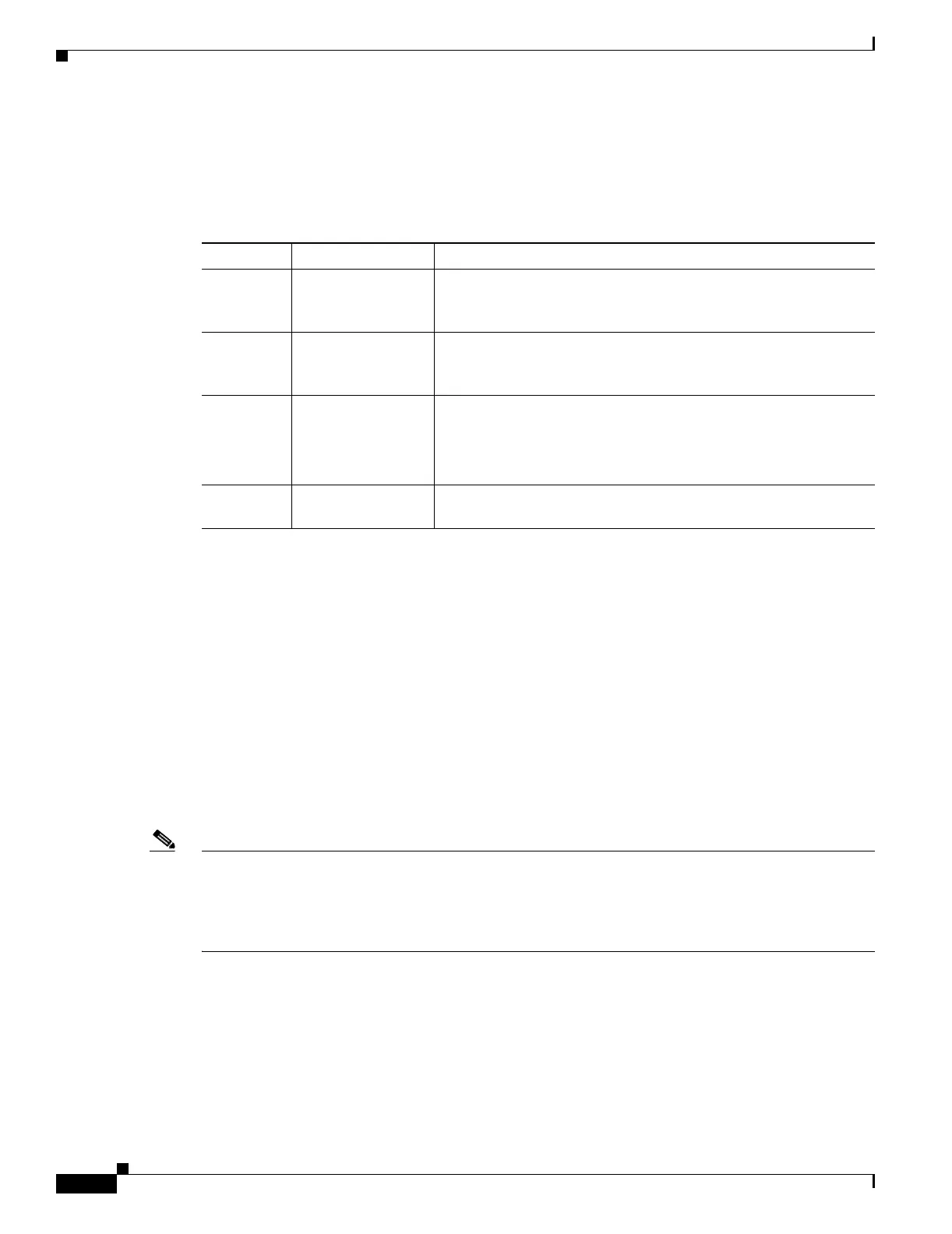
ppp-attributes mode. Table 28-1 shows the types of PPP authentication, and their characteristics.
hostname(config)# tunnel-group name ppp-attributes
hostname(config-ppp)# authentication pap
Step 9 Specify a method to authenticate users attempting L2TP over IPSec connections. Use the
authentication-server-group command from tunnel-group general-attributes mode to configure the
security appliance to use an authentication server or its own local database.
Using an Authentication Server
To use an authentication server, use the authentication server group keyword:
hostname(config)# tunnel-group name general-attributes
hostname(config-tunnel-general)# authentication-server-group auth_server_group
Using the Local Database
To use the local database, enter the LOCAL keyword.
hostname(config)# tunnel-group name general-attributes
hostname(config-tunnel-general)# authentication-server-group LOCAL
Note The security appliance only supports the PPP authentications PAP and Microsoft CHAP, Versions 1 and
2, on the local database. EAP and CHAP are performed by proxy authentication servers. Therefore, if a
remote user belongs to a tunnel group configured with the authentication eap-proxy or authentication
chap commands, and the security appliance is configured to use the local database, that user will not be
able to connect.
Step 10 Create a user in the local database with the username command from global configuration mode.
If the user is an L2TP client using Microsoft CHAP, Version 1 or Version 2, and the security appliance
is configured to authenticate against the local database, you must include the mschap keyword. For
Example:
hostname(config)# username t_wmith password eu5d93h mschap
Table 28-1 Authentication Type Characteristics
Keyword Authentication Type Characteristics
chap
CHAP In response to the server challenge, the client returns the encrypted
[challenge plus password] with a cleartext username. This protocol
is more secure than the PAP, but it does not encrypt data.
eap-proxy
EAP Enables EAP which permits the security appliance to proxy the
PPP authentication process to an external RADIUS authentication
server.
ms-chap-v1
ms-chap-v2
Microsoft CHAP,
Ver si on 1
Microsoft CHAP,
Ver si on, 2
Similar to CHAP but more secure in that the server stores and
compares only encrypted passwords rather than cleartext
passwords as in CHAP. This protocol also generates a key for data
encryption by MPPE.
pap
PAP Passes cleartext username and password during authentication and
is not secure.

 Loading...
Loading...











