E-21
Cisco Security Appliance Command Line Configuration Guide
OL-10088-01
Appendix E Configuring an External Server for Authorization and Authentication
Configuring an External LDAP Server
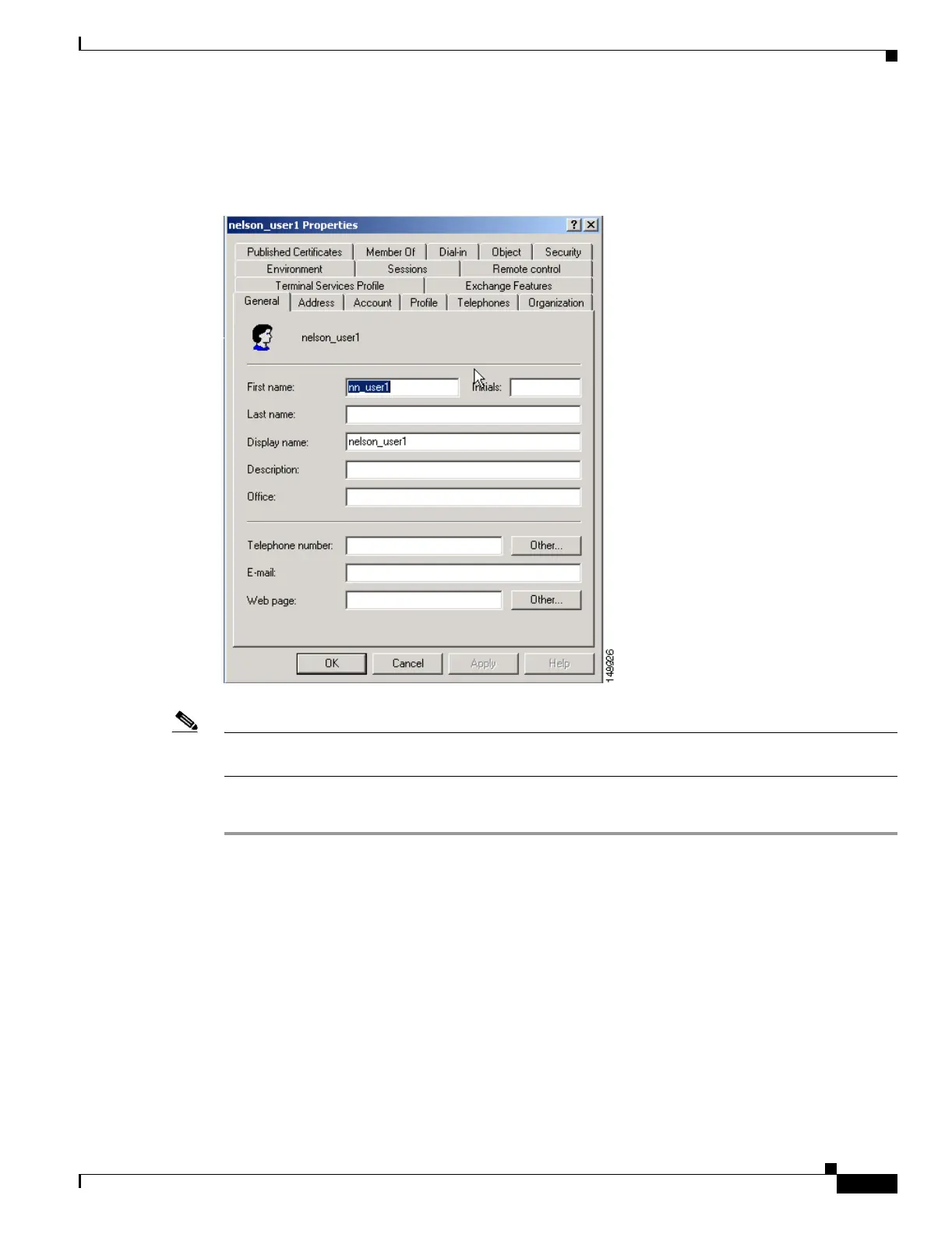
Review specific user attributes and values by right-clicking the username and clicking Properties. The
Username Properties dialog box appears as shown in Figure E-4.
Figure E-4 The Username Properties Dialog Box
Note The department attribute is configured under the Organization tab in the Active Directory Users and
Computers window.
To configure this example, perform the following steps on the security appliance:
Step 1 Create a aaa-server record for the LDAP authentication server and use the ldap-base-dn to specify the
search location for the Active Directory user records as shown in the following example commands:
hostname(config)# aaa-server ldap-authenticate-grp protocol ldap
hostname(config-aaa-server-group)# aaa-server ldap-authenticate-grp host 10.1.1.4
hostname(config-aaa-server-host)# ldap-base-dn cn=Users,dc=frdevtestad,dc=local
hostname(config-aaa-server-host)# ldap-scope subtree
hostname(config-aaa-server-host)# ldap-naming-attribute cn
hostname(config-aaa-server-host)# ldap-login-password anypassword
hostname(config-aaa-server-host)# ldap-login-dn cn=Administrator,cn=Users,
dc=frdevtestad,dc=local
hostname(config-aaa-server-host)#
Step 2 Create an LDAP mapping table entry to map the AD attribute department to the Cisco attribute
cVPN3000-IETF-Radius-Class as shown in the following example commands:
hostname(config)# ldap attribute-map ActiveDirectoryMapTable

 Loading...
Loading...











