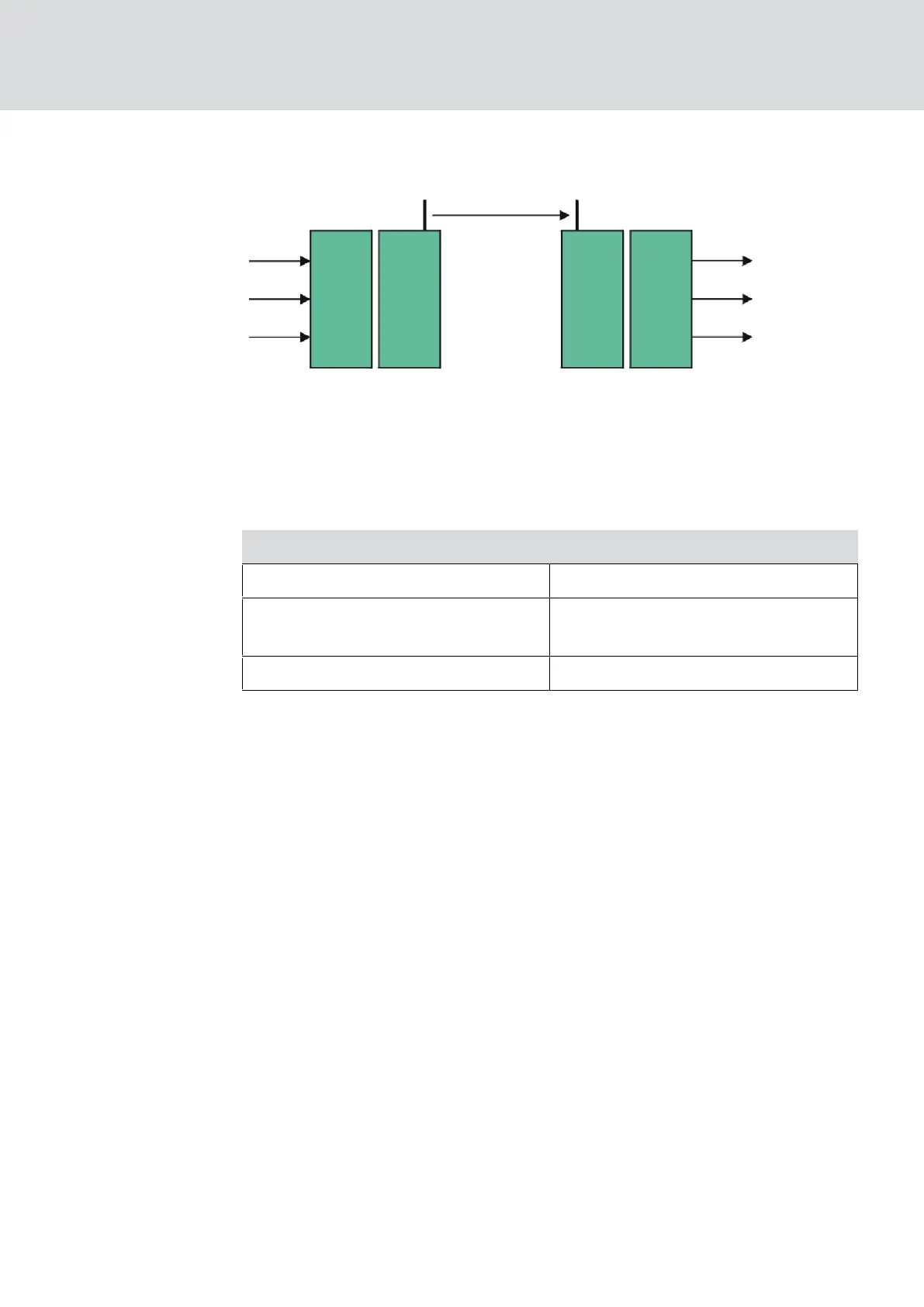
Technical realization
Data
Coding Decoding
Evaluation
Transmission
Sender
Receiver
End-to-end encryption
End-to-end means in this context: between central software and locking
devices. The data is encrypted and leaves the central software. It is only
decrypted again when the locking device is closed.
Communication Encryption
End-to-end (general) 3DES (112 bit)
Access lists (against unauthorised
reading)
Single DES (56 bit)
Broadcast signals AES (128 bit)
Digitally signed data packages
The 128-bit signing of the data packets protects against manipulation on
the radio link. If the signature of a data packet is not correct, the data
packet is ignored.
Protection against replay attacks
Each safety-relevant data packet contains a counter. This counter is
incremented for each new data packet. If a data packet with the same
counter reading arrives again, the data packet is ignored. This means that if
an attacker records a data packet and sends it again (replay attack), the
counter of the data packet is the same as that of the original packet and
the copy of the attacker is recognized and therefore ignored.
4.5.2 Monitoring the devices in the network
The devices on your WaveNet can be distributed over large parts of the
building. You can monitor the devices partially remotely:
the status of your
locking devices
If you use door monitoring locking devices, the current status of your locking
device is transmitted to LSM via WaveNet and displayed there (DM
column). As an alternative to the display in LSM, you can also monitor the
status of your locking devices using Smart.Surveil.
WaveNet (Manual)
4. WaveNet system
28 / 210
 Loading...
Loading...