one (encrypted or unencrypted) stored on the server if you have configured to back up the
MAC-local CFG file to the server by the parameter “static.auto_provision.custom.sync”.
If it is set to 1 (Enabled), the MAC-local CFG file is uploaded encrypted and replaces the one
(encrypted or unencrypted) stored on the server if you have configured to back up the MAC-
local CFG file to the server by the parameter “static.auto_provision.custom.sync”. The
plaintext AES key is configured by the parameter “static.auto_provision.aes_key_16.mac”.
Web User Interface:
None
Handset User Interface:
None
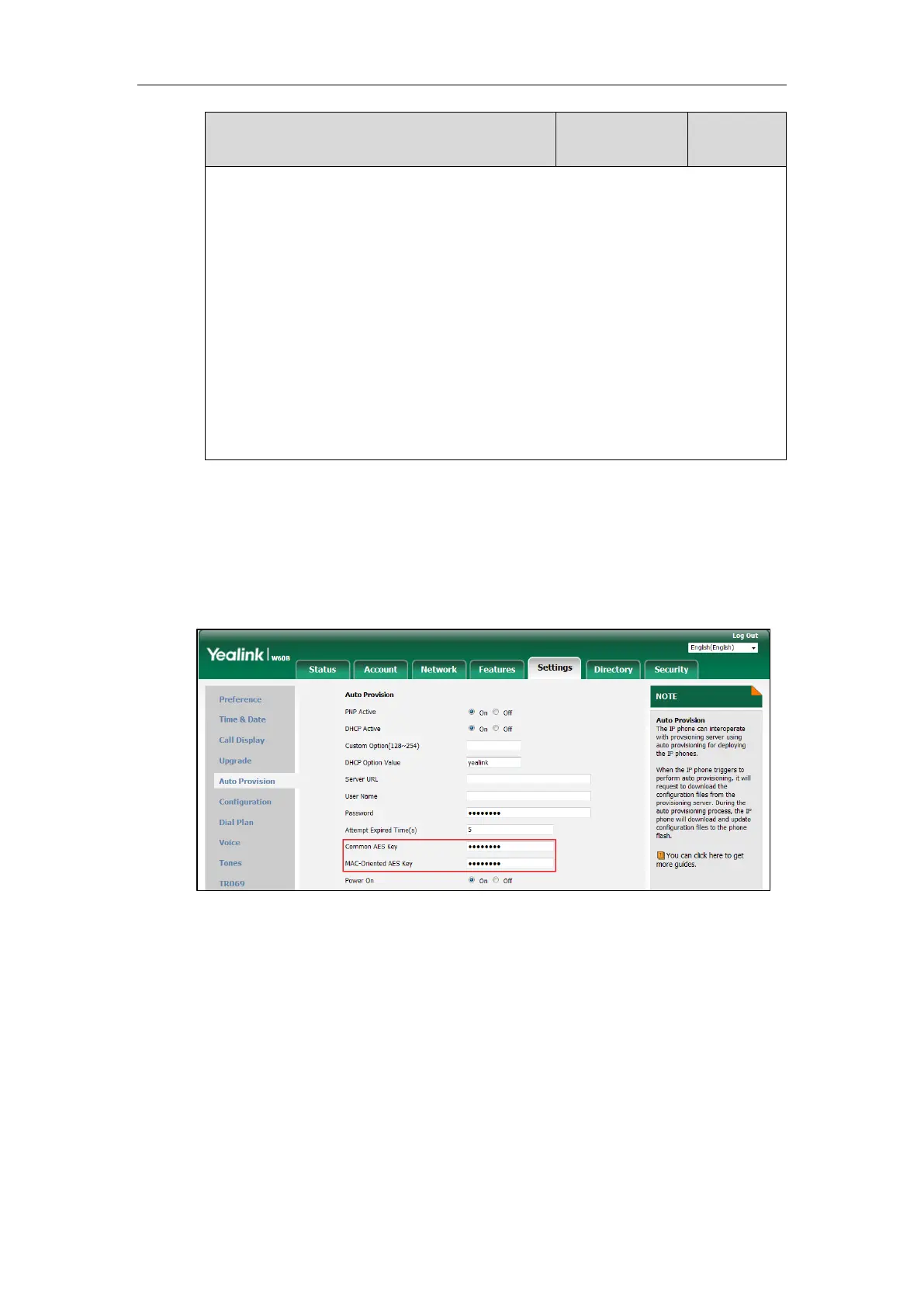
To configure AES keys via web user interface:
1. Click on Settings->Auto Provision.
2. Enter the values in the Common AES Key and MAC-Oriented AES Key fields.
AES keys must be 16 characters and the supported characters contain: 0-9, A-Z, a-z and
the following special characters are also supported: # $ % * + , - . : = ? @ [ ] ^ _ { } ~.
3. Click Confirm to accept the change.
Encrypting and Decrypting Configuration Files
Encrypted configuration files can be downloaded from the provisioning server to protect
against unauthorized access and tampering of sensitive information (e.g., login passwords,
registration information).
Yealink supplies a configuration encryption tool for encrypting configuration files. The
encryption tool encrypts plaintext configuration files (e.g., account.cfg, y000000000077.cfg,
<MAC>.cfg) (one by one or in batch) using 16-character symmetric keys (the same or different
keys for configuration files) and generates encrypted configuration files with the same file

 Loading...
Loading...