8.2.1 Security codes
The datalogger employs a security scheme that includes three levels of security. Security codes
can effectively lock out innocent tinkering and discourage wannabe hackers on all
communication links. However, any serious hacker with physical access to the datalogger or to
the communications hardware can, with only minimal trouble, overcome the five-digit security
codes. Security codes are held in the datalogger Settings Editor.
The preferred methods of enabling security include the following:
l Device Configuration Utility: Security codes are set on the Deployment> Datalogger tab.
l Network Planner:Security codes can be set as dataloggers are added to the network.
Alternatively, in CRBasic the SetSecurity() instruction can be used. It is only executed at
program compile time. This is not recommended because deleting SetSecurity() from a
CRBasic program is not equivalent to SetSecurity(0,0,0). Settings persist when a new
program is downloaded that has no SetSecurity() instruction.
Up to three levels of security can be set. Valid security codes are 1 through 65535 ( 0 confers no
security). Security 1 must be set before Security 2. Security 2 must be set before Security 3. If any
one of the codes is set to 0, any security code level greater than it will be set to 0. For example, if
Security 2 is 0 then Security 3 is automatically set to 0. Security codes are unlocked in reverse
order: Security 3 before Security 2, Security 2 before Security 1.
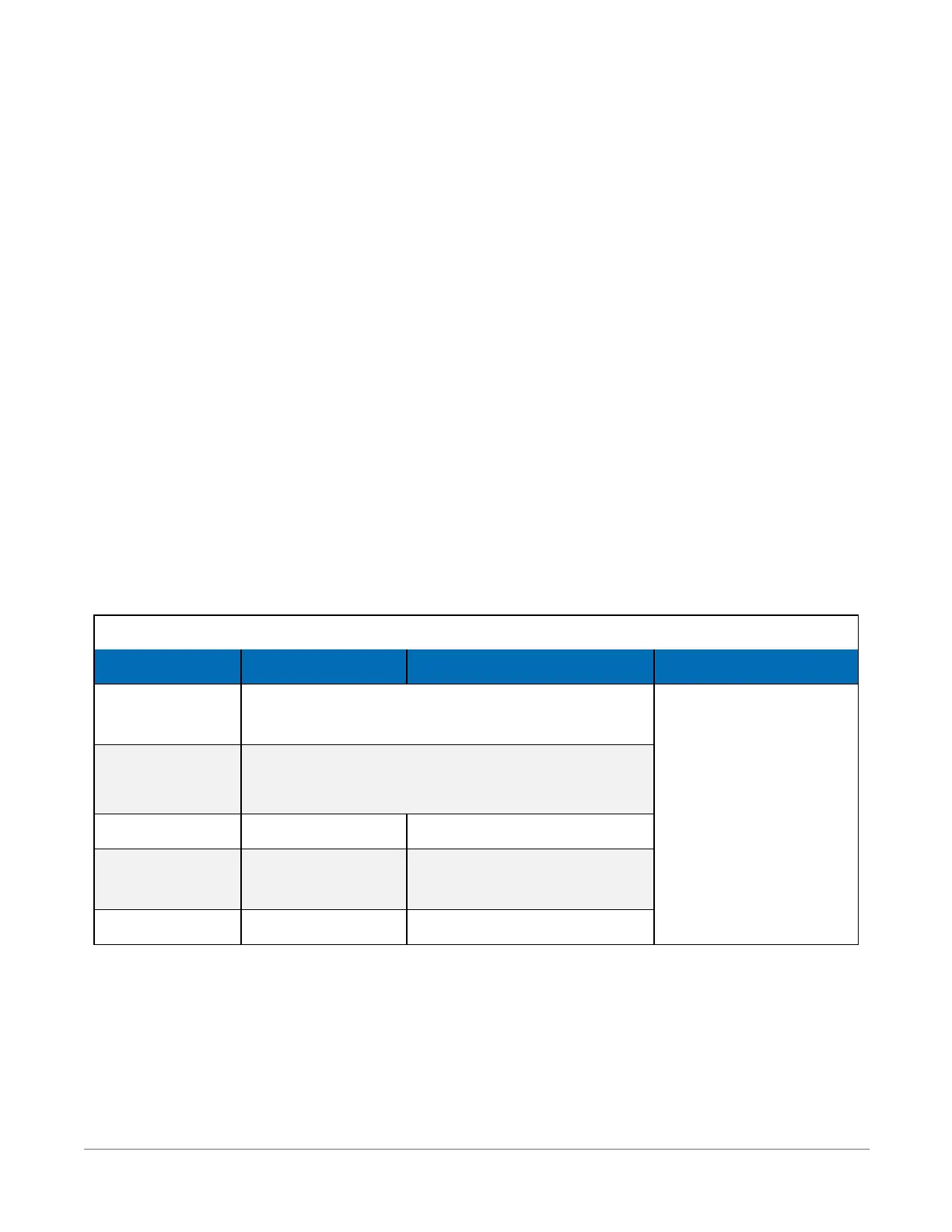
Table 8-1: Functions affected by security codes
Function Security code 1 set Security code 2 set Security code 3 set
Datalogger
program
Cannot change or retrieve
All communications
prohibited
Settings editor
and Status table
Writable variables cannot be changed
Setting clock unrestricted Cannot change or set
Public table unrestricted
Writable variables cannot be
changed
Collecting data unrestricted unrestricted
See Security (p. 127) for the related fields in the Settings Editor.
For additional information on datalogger security, see:
l 4 Ways to Make your Data More Secure
l Available Security Measures for Internet-Connected Dataloggers
8. Maintaining your datalogger 102

 Loading...
Loading...