37-10
Cisco Security Appliance Command Line Configuration Guide
OL-10088-01
Chapter 37 Configuring WebVPN
Getting Started with WebVPN
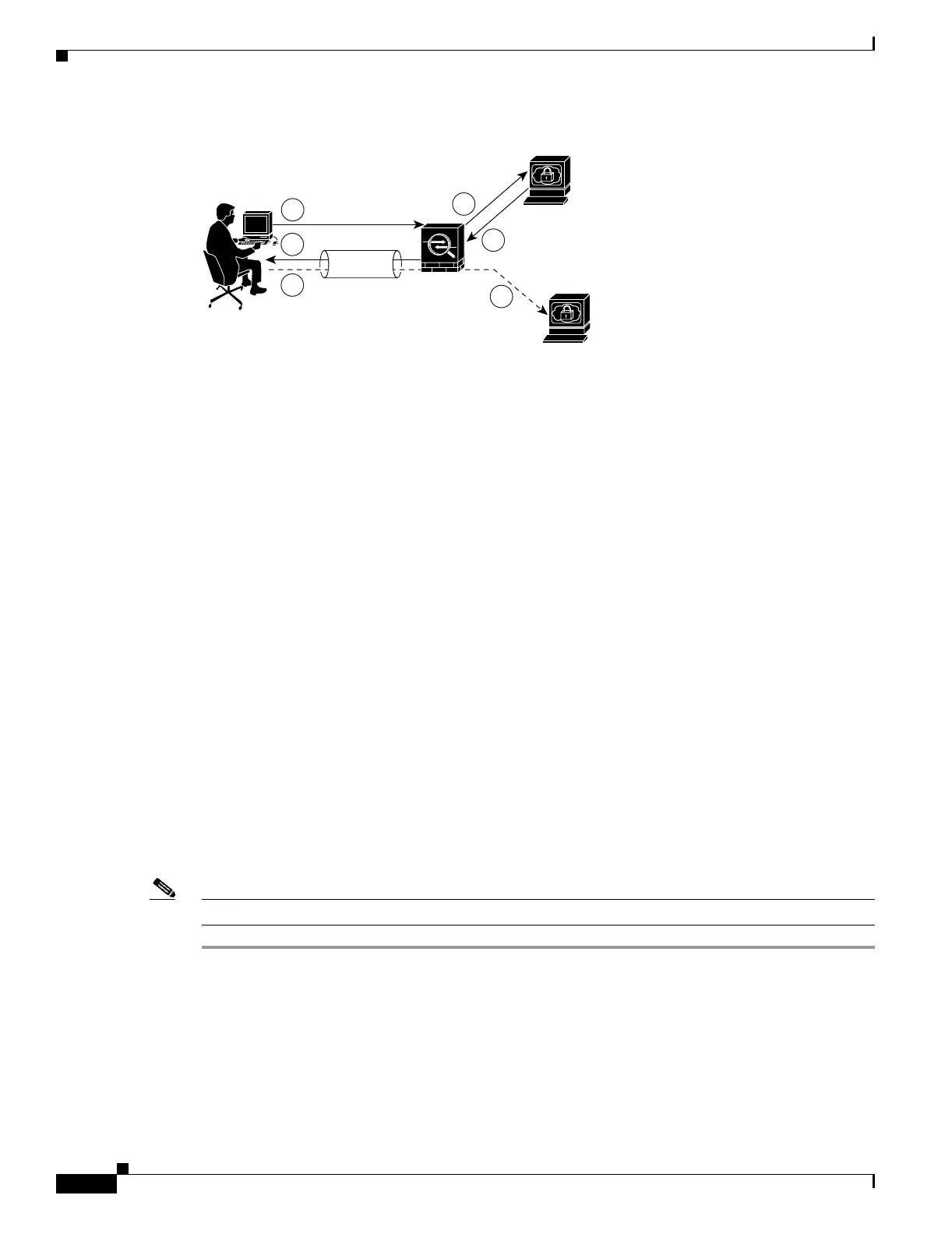
Figure 37-1 SSO Authentication Using HTTP Forms
While you would expect to configure form parameters that let the security appliance include POST data
such as the username and password, you initially might not be aware of additional hidden parameters
that the web server requires. Some authentication applications expect hidden data which is neither
visible to nor entered by the user. You can, however, discover hidden parameters the authenticating web
server expects by making a direct authentication request to the web server from your browser without
the security appliance in the middle acting as a proxy. Analyzing the web server response using an HTTP
header analyzer reveals hidden parameters in a format similar to the following:
<param name>=<URL encoded value>&<param name>=<URL encoded>
Some hidden parameters are mandatory and some are optional. If the web server requires data for a
hidden parameter, it rejects any authentication POST request that omits that data. Because a header
analyzer does not tell you if a hidden parameter is mandatory or not, we recommend that you include all
hidden parameters until you determine which are mandatory.
This section describes:
• Gathering HTTP Form Data
• Task Overview: Configuring SSO with HTTP Form Protocol
• Detailed Tasks: Configuring SSO with HTTP Form Protocol
Gathering HTTP Form Data
This section presents the steps for discovering and gathering necessary HTTP Form data. If you do not
know what parameters the authenticating web server requires, you can gather parameter data by
analyzing an authentication exchange using the following steps:
Note These steps require a browser and an HTTP header analyzer.
Step 1 Start your browser and HTTP header analyzer, and connect directly to the web server login page without
going through the security appliance.
Step 2 After the web server login page has loaded in your browser, examine the login sequence to determine if
a cookie is being set during the exchange. If the web server has loaded a cookie with the login page,
configure this login page URL as the start-URL.
Step 3 Enter the username and password to log in to the web server, and press Enter. This action generates the
authentication POST request that you examine using the HTTP header analyzer.
148147
Web VPN
server
1
4
5
5
3
2
Auth Web
server
Other protected
web server
Tunnel

 Loading...
Loading...











