1-14
Firepower 7000 and 8000 Series Installation Guide
Chapter 1 Introduction to the Firepower System
Security, Internet Access, and Communication Ports
Communication Ports Requirements
Firepower System appliances communicate using a two-way, SSL-encrypted communication channel,
which by default uses port 8305/tcp. The system requires this port remain open for basic intra-appliance
communication. Other open ports allow:
• access to an appliance’s web interface
• secure remote connections to an appliance
• certain features of the system to access the local or Internet resources they need to function correctly
In general, feature-related ports remain closed until you enable or configure the associated feature. For
example, until you connect the Firepower Management Center to a User Agent, the agent
communications port (3306/tcp) remains closed. As another example, port 623/udp remains closed on
7000 and 8000 Series appliances until you enable LOM.
Caution Do not close an open port until you understand how this action will affect your deployment.
For example, closing port 25/tcp (SMTP) outbound on a managed device blocks the device from sending
email notifications for individual intrusion events (see the Firepower Management Center Configuration
Guide). As another example, you can disable access to a physical managed device’s web interface by
closing port 443/tcp (HTTPS), but this also prevents the device from submitting suspected malware files
to the cloud for dynamic analysis.
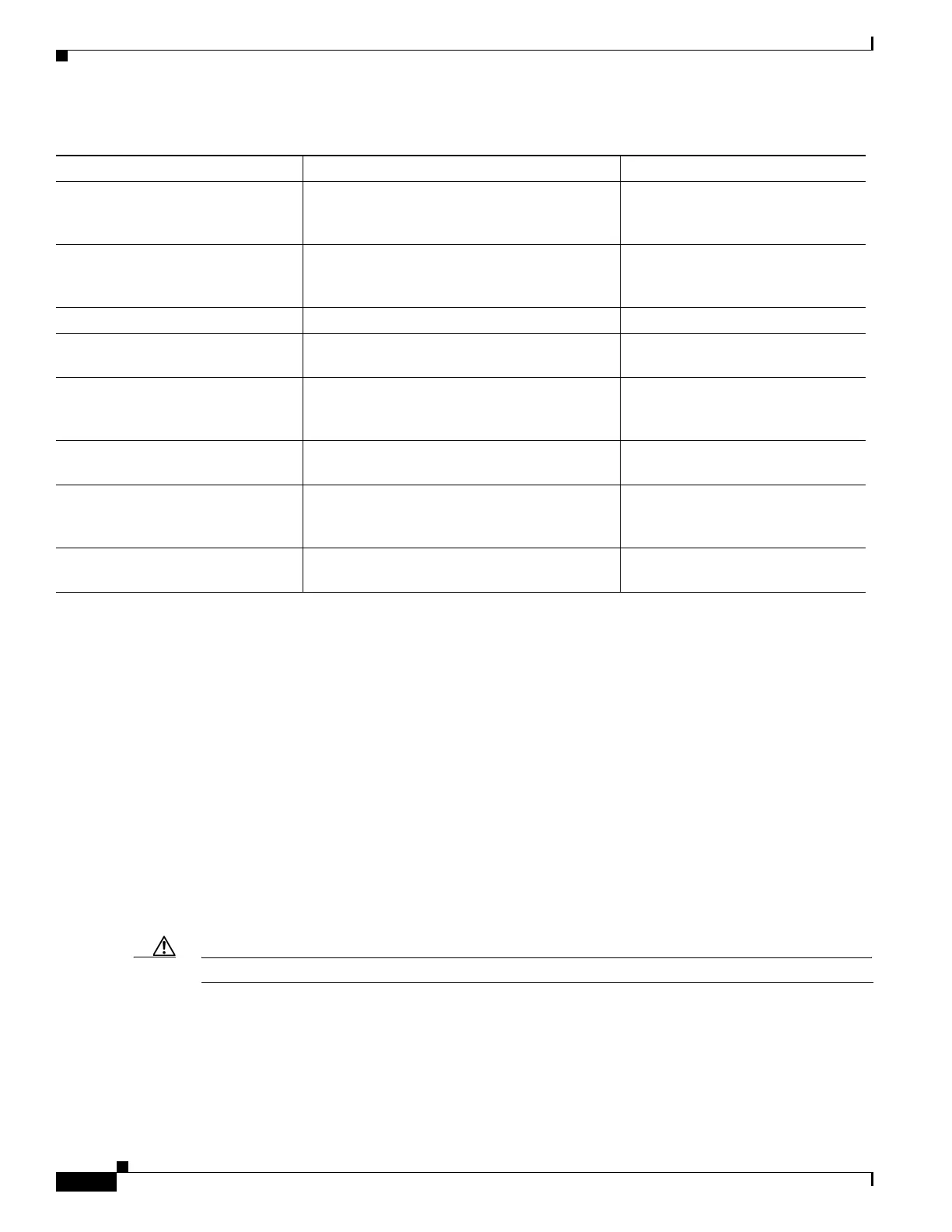
FireAMP integration receive endpoint-based (FireAMP) malware
events from the Collective Security Intelligence
Cloud cloud.
Management Center
intrusion rule, VDB, and GeoDB
updates
download or schedule the download of a
intrusion rule, GeoDB, or VDB update directly
to an appliance.
Management Center
network-based AMP perform malware cloud lookups. Management Center
RSS feed dashboard widget download RSS feed data from an external
source, including Cisco.
Any except virtual devices and
ASA FirePOWER
Security Intelligence filtering download Security Intelligence feed data from
an external source, including the Firepower
System Intelligence Feed.
Management Center
system software updates download or schedule the download of a system
update directly to an appliance.
Any except virtual devices and
ASA FirePOWER
URL Filtering download cloud-based URL category and
reputation data for access control, and perform
lookups for uncategorized URLs.
Management Center
whois request whois information for an external host. Any except virtual devices and
ASA FirePOWER
Table 1-6 Firepower System Feature Internet Access Requirements (continued)
Feature Internet access is required to... Appliances
 Loading...
Loading...











