User Manual of Network Fisheye Camera
66
alarm response action.
Steps:
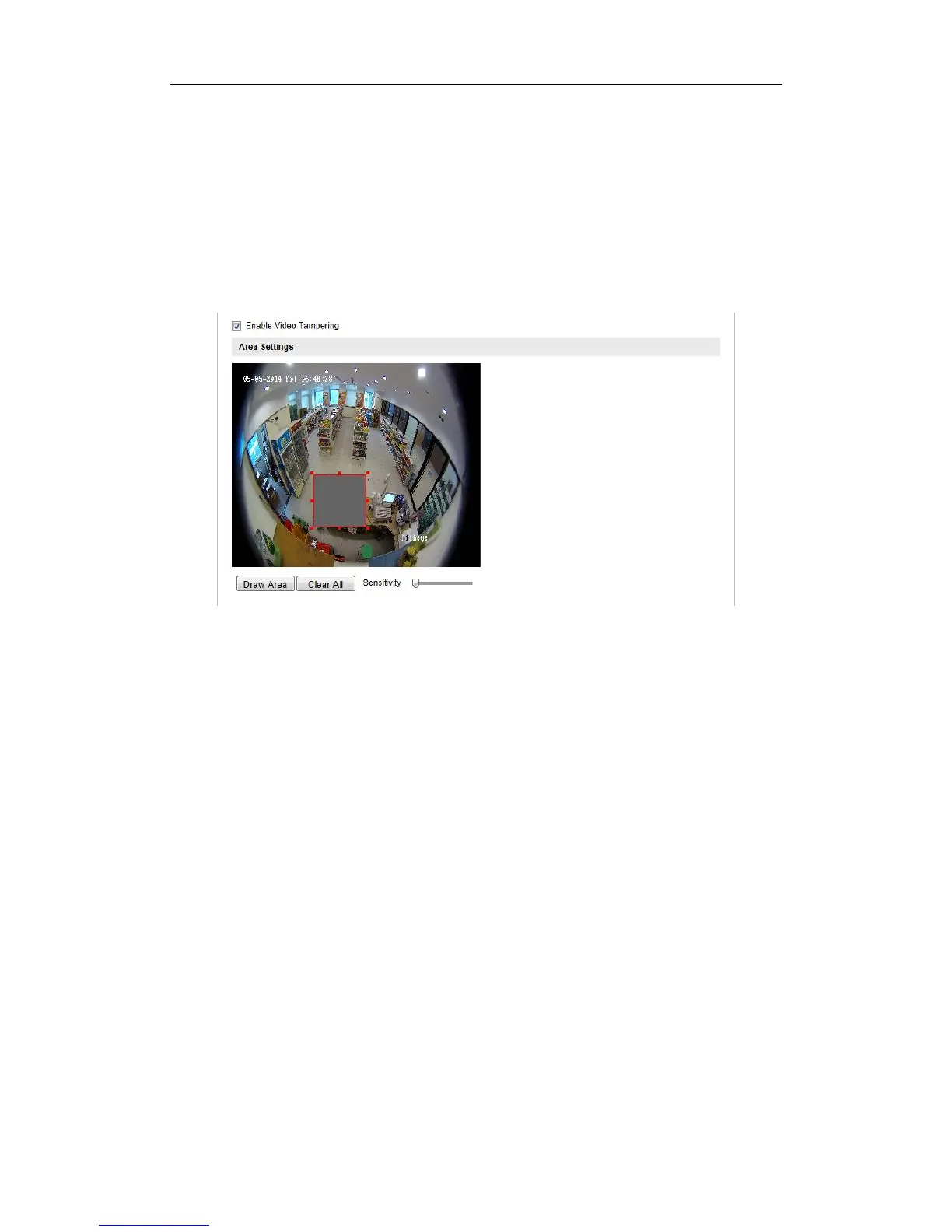
1. Enter the Tamper-proof Settings interface:
Configuration > Advanced Configuration > Events > Video Tampering
2. Check the checkbox of Enable Video Tampering to enable video tampering
detection function.
Figure 5-45 Video Tampering Detection Settings
3. Set the detection area for video tampering. For details, refer to Step 4 in Section
5.6.1.
4. Click Edit to edit the arming schedule for video tampering detection. For details,
refer to Step 5 in Section 5.6.1.
5. Check the checkbox to set the alarm actions for video tampering.
Notify surveillance center, send email and trigger alarm output are selectable. For
details, refer to Step 6 in Section 5.6.1.
6. Click Save to save the settings.
5.6.3 Configuring Alarm Input
Steps:
1. Enter the Alarm Input Settings interface:
Configuration > Advanced Configuration> Events > Alarm Input:
2. Choose the alarm input No. and the Alarm Type. The alarm type can be NO

 Loading...
Loading...











