10-15
IPv4 Access Control Lists (ACLs)
Overview
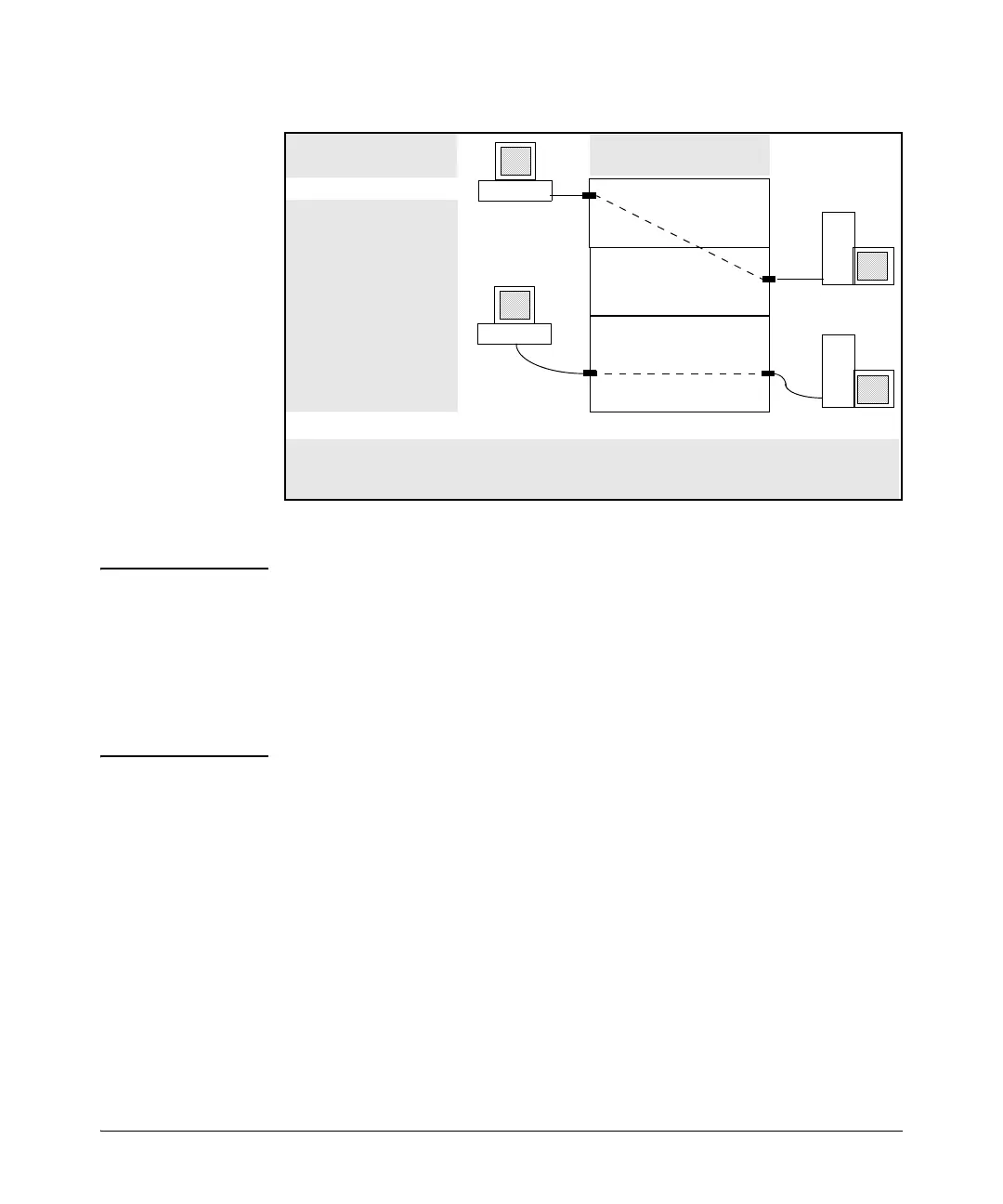
Figure 10-1. Example of RACL Filter Applications on Routed IPv4 Traffic
Notes The switch allows one inbound RACL assignment and one outbound RACL
assignment configured per VLAN. This is in addition to any other ACL assigned
to the VLAN or to any ports on the VLAN. You can use the same RACL or
different RACLs to filter inbound and outbound routed traffic on a VLAN.
RACLs do not filter IPv4 traffic that remains in the same subnet from source
to destination (switched traffic) unless the destination address (DA) or source
address (SA) is on the switch itself.
VLAN 1
10.28.10.1
(One Subnet)
VLAN 3
10.28.40.1 10.28.30.1
(Multiple Subnets)
VLAN 2
10.28.20.1
(One Subnet)
Switch with IPv4 Routing
Enabled
10.28.10.5
10.28.20.99
10.28.30.33
10.28.40.17
Because of multinetting, traffic routed from the 10.28.40.0 network to the 10.28.30.0 network, and the
reverse, remains in VLAN 3. This allows you to apply one inbound ACL to screen traffic arriving from
either subnet, and one outbound ACL to screen routed traffic going to either subnet.
The subnet mask for this
example is 255.255.255.0.
An ACL assigned to screen
routed, inbound IPv4 traffic
on VLAN 1 screens only the
routed traffic arriving from
the 10.28.10.0 network.
Screening routed traffic
inbound from the 10.28.20.0
network requires
assigning another ACL for
inbound traffic on VLAN 2.

 Loading...
Loading...











