201
User Guide
© 2014 Luxul. All Rights Reserved.
Other trademarks and registered trademarks are the property of their respective owners
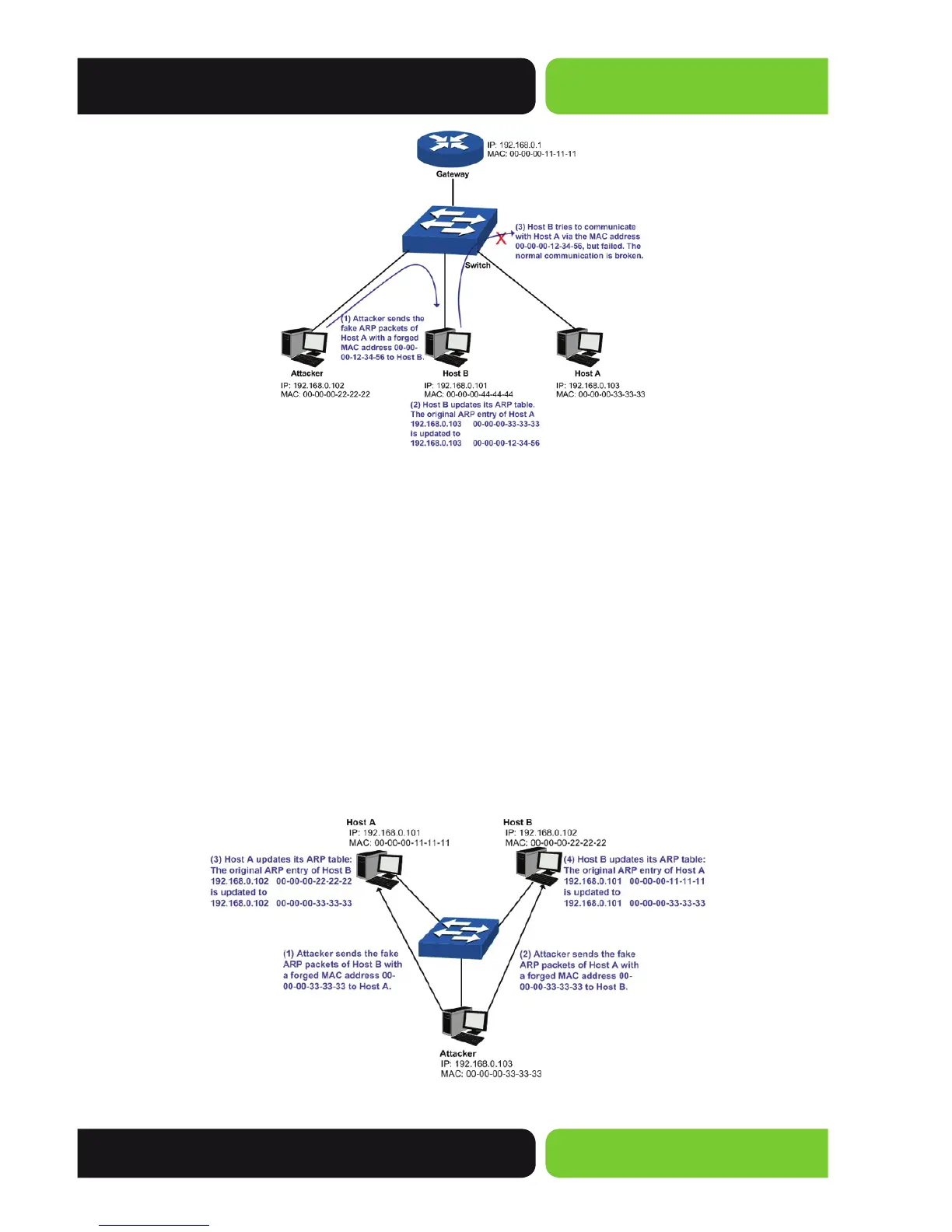
Figure 12-11 ARP Attack – Cheating Terminal Hosts
As the above fi gure shows, when Host B tries to communicate with Host A, it will en-
capsulate the false destination MAC Address, which results in a breakdown of normal
communication.
Man-In-The-Middle Attack
The attacker continuously sends counterfeit ARP packets to Hosts in the LAN to get
the Hosts to maintain a counterfeit ARP Table. When the Hosts in LAN communicate
with one another, they will send the packets to the attacker’s designated ARP table en-
try. The attacker can process the packets before forwarding them. The communication
packets between the two Hosts are stolen and the Hosts are unaware of the attack.
This is called a Man-In-The-Middle Attack. The Man-In-The-Middle Attack is illustrated
in the following fi gure:
Figure 12-12 Man-In-The-Middle Attack

 Loading...
Loading...