Protection measures and security strategy UM2262
20/94 UM2262 Rev 6
5 Protection measures and security strategy
Cryptography ensures integrity, authentication and confidentiality. However, the use of
cryptography alone is not enough: a set of measures and system-level strategy are needed
for protecting critical operations and sensitive data (such as a secret key), and the execution
flow, in order to resist possible attacks.
Secure software coding techniques such as doubling critical tests, doubling critical actions,
checking parameters values, and testing a flow control mechanism, are implemented to
resist basic fault-injection attacks.
The security strategy is based on the following concepts:
• Ensure single-entry point at reset: force code execution to start with Secure Boot code
• Make SBSFU code and SBSFU secrets immutable: no possibility to modify or alter
them once security is fully activated
• Create a protected enclave isolated from SBSFU application and from User
applications to store secrets such as keys, and to run critical operations such as
cryptographic algorithms
• Limit surface execution to SBSFU code during SBSFU application execution
• Remove JTAG access to the device
• Monitor the system: intrusion detection and SBSFU execution time
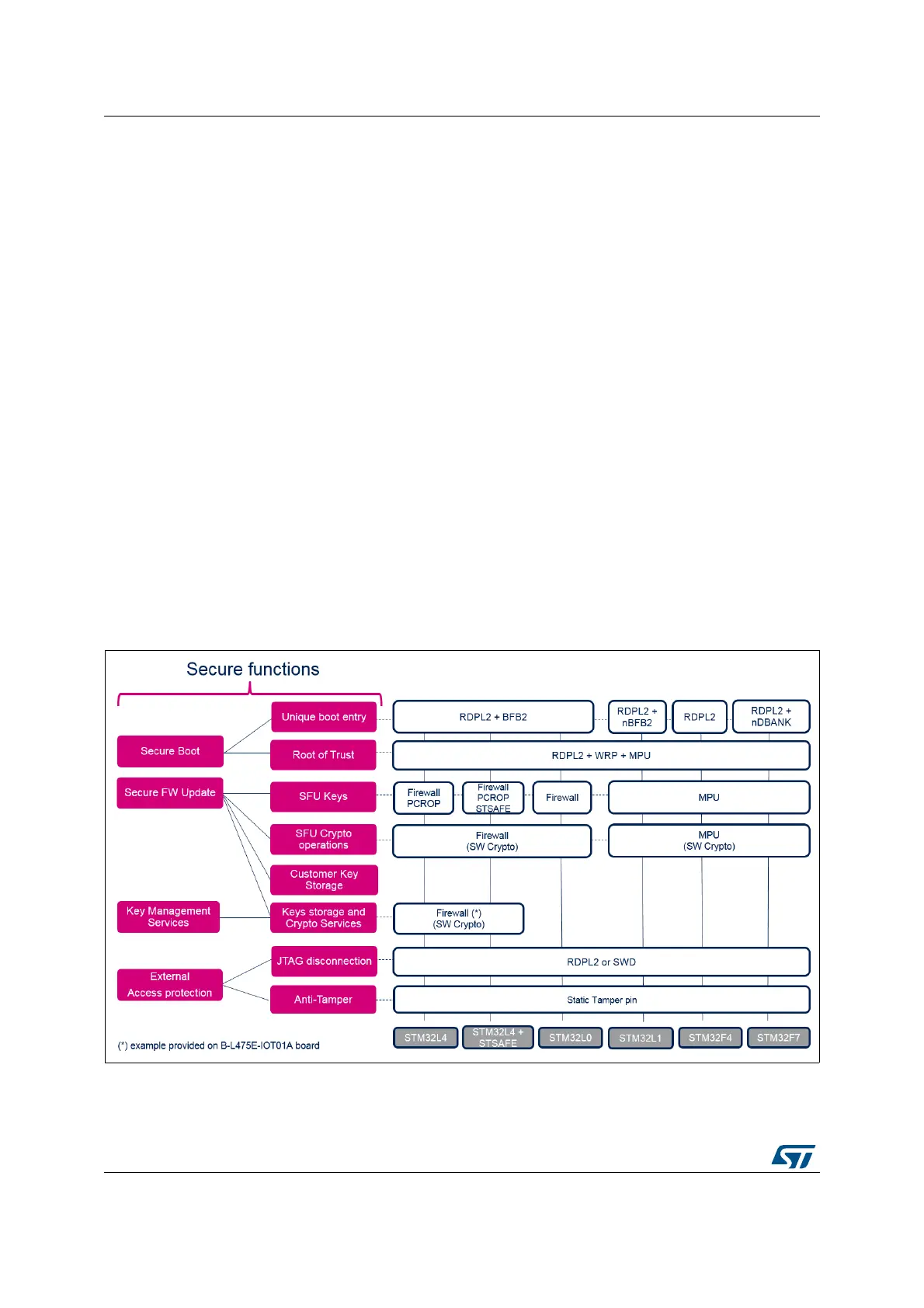
Figure 4 and Figure 5 give a high-level view of the security mechanisms activated on each
STM32 Series.
Figure 4. SBSFU security IPs vs. STM32 Series (1 of 2)
 Loading...
Loading...