SBSFU with STM32 and STSAFE-A100 UM2262
84/94 UM2262 Rev 6
Appendix G SBSFU with STM32 and STSAFE-A100
G.1 Introduction to STSAFE-A100
STSAFE-A100 is a tamper-resistant secure element (HW Common Criteria EAL5+ certified)
used to host X509 certificates and keys, and perform verifications that are used for firmware
image authentication during Secure Boot and Secure Firmware Update procedures.
STSAFE-A100 is connected to STM32 using the I
2
C HW interface. Paring keys must be
provisioned inside STSAFE-A100 and STM32 to secure the system:
• Host_Mac_Key: a symmetric key used to pair a specific STM32 with a specific
STSAFE-A100 in order to prevent product cloning
• Host_Cipher_Key: a symmetric key used to encrypt I
2
C communication between
STM32 and STSAFE-A100 in order to establish a secure communication channel
To combine an STSAFE-A100 with an STM32 for an SBSFU application, cryptographic
scheme X509 certificate-based asymmetric scheme without firmware encryption is used
(refer to
Appendix D Cryptographic schemes handling for more details). This cryptographic
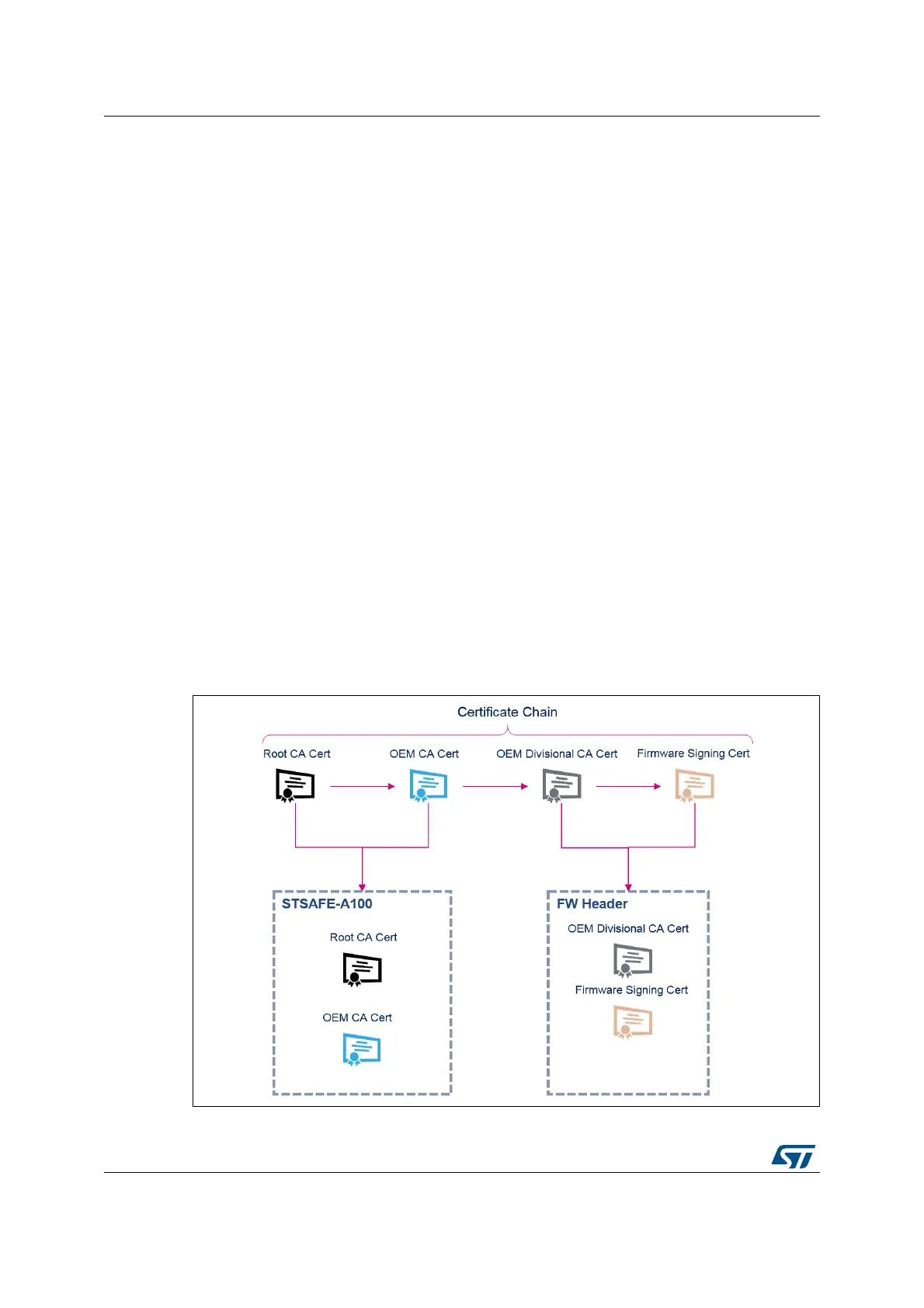
scheme is based on a four-certificate chain principle:
• Root CA Cert: root certificate to be provisioned once inside the STSAFE-A100
• OEM CA Cert: first intermediate certificate from the OEM to be provisioned once inside
the STSAFE-A100
• OEM Divisional CA Cert: second intermediate certificate from the OEM to be inserted
inside the header of each new firmware image
• Firmware Signing Cert: firmware signing certificate from the OEM to be inserted inside
the header of each new firmware image
Figure 49. Certificate chain overview

 Loading...
Loading...