UM2262 Rev 6 57/94
UM2262 Step-by-step execution
93
8.5.2 Test protections
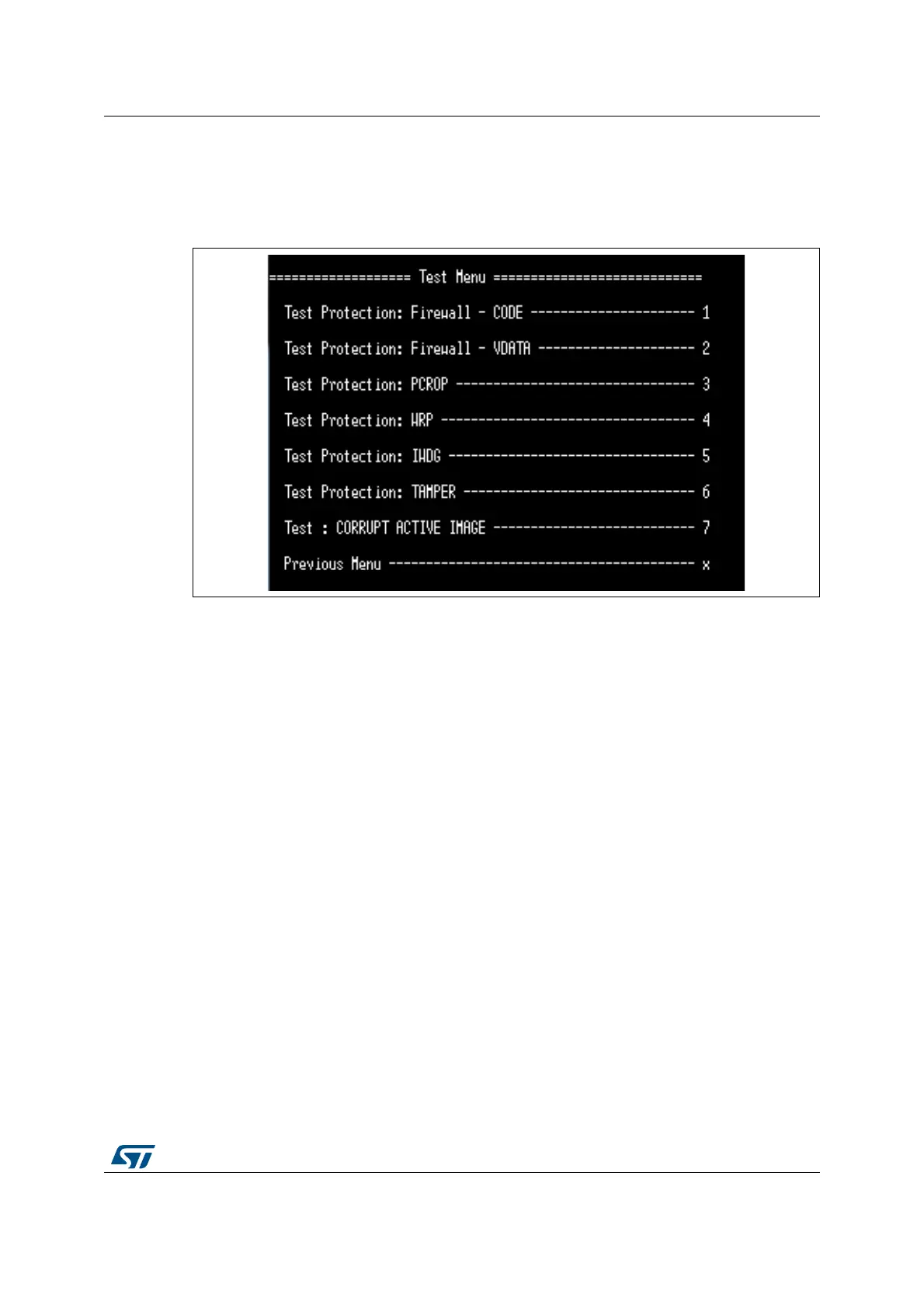
An example of the test protection menu is shown in Figure 30. The actual menu depends on
the STM32 Series.
Figure 30. User application test protection menu
The test protection menu is printed at each test attempt of a prohibited operation or error
injection as a function of the test run:
• Firewall tests (#1, #2)
– Causes a reset trying to access protected code or data (either in RAM or Flash)
• PCROP test (#3)
– Causes an error trying to access the PCROP region protecting the keys
• WRP test (#4)
– Causes an error trying to erase write protected code
• IWDG test (#5)
– Causes a reset simulating a deadlock by not refreshing the watchdog
• TAMPER test (#6)
– Causes a reset if a tamper event is detected
– In order to generate a tamper event, the user must connect PA0 (CN7.28) to GND
(It may be enough to put a finger close to CN7.28).
• CORRUPT IMAGE test (#7)
– Causes a signature verification failure at next boot.
Returning to the previous menu is obtained by pressing the x key.
8.5.3 Test Secure Engine user code
The version and size of the current user firmware are retrieved by means of a Secure
Engine service, and printed in the console.

 Loading...
Loading...