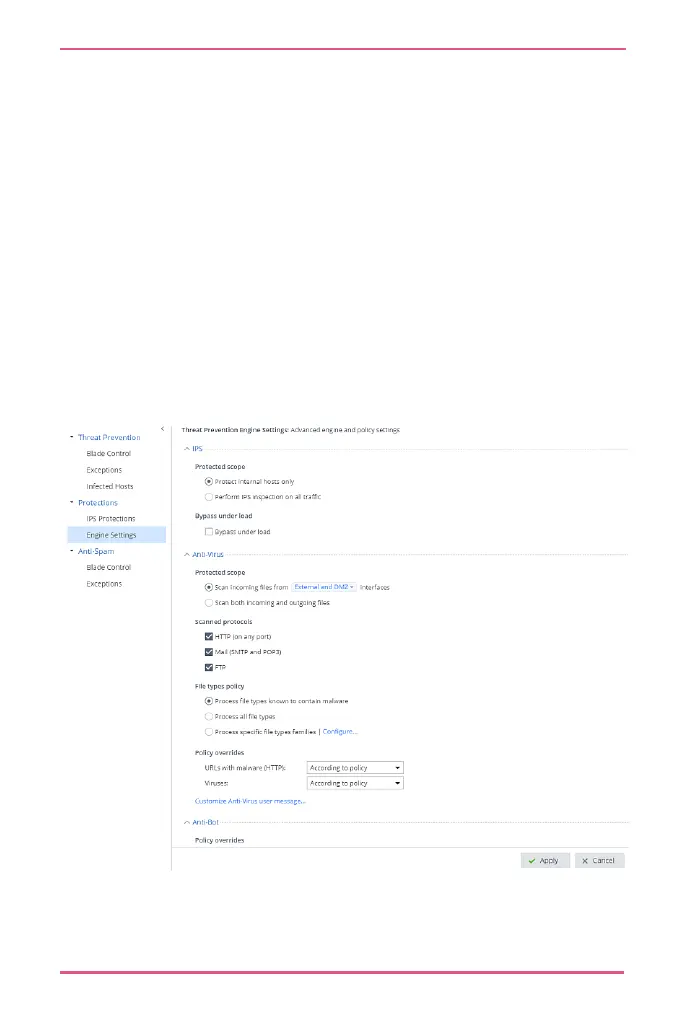
You can:
• Configure when files will be inspected.
By default, only incoming files are inspected.
• Select policy overrides.
• Select file types policy.
• Block viruses from web and mail traffic (HTTP, SMTP,
and POP3) and from the File Transfer Protocol (FTP).
• Prevent virus and bot attacks. You can also set detect
only mode and use the logs to see if there are any
attacks.
• Protect against malicious files.
 Loading...
Loading...











