5-36
Cisco Wireless LAN Controller Configuration Guide
OL-9141-03
Chapter 5 Configuring Security Solutions
Configuring IDS
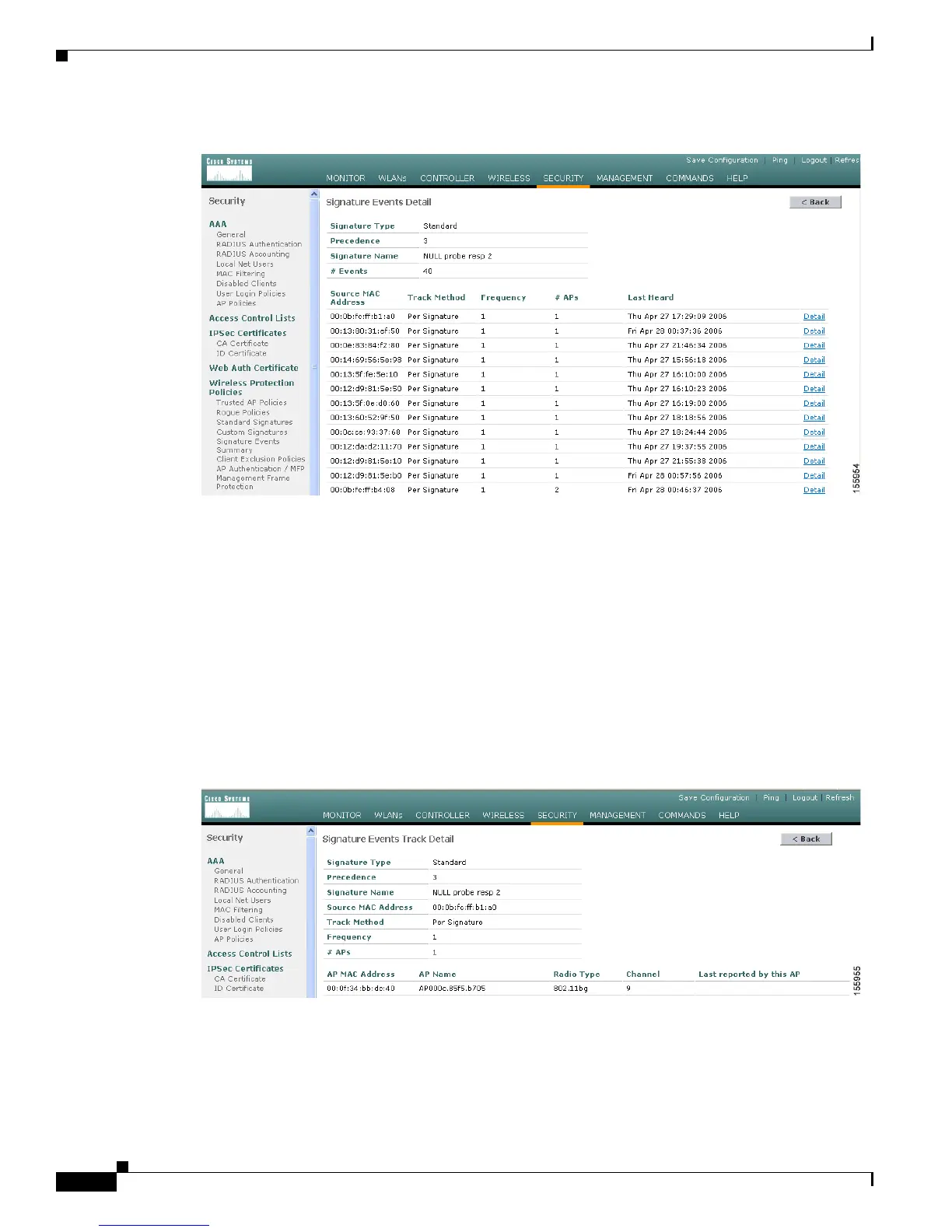
Figure 5-17 Signature Events Detail Page
This page shows the following information:
• The MAC addresses of the clients identified as attackers
• The method used by the access point to track the attacks
• The number of matching packets per second that were identified before an attack was detected
• The number of access points on the channel on which the attack was detected
• The day and time when the access point detected the attack
Step 3 To see more information for a particular attack, click the Detail link for that attack. The Signature Events
Track Detail page appears (see Figure 5-18).
Figure 5-18 Signature Events Track Detail Page
This page shows the following information:
• The MAC address of the access point that detected the attack
• The name of the access point that detected the attack
• The type of radio (802.11a or 802.11b/g) used by the access point to detect the attack

 Loading...
Loading...