195
Triple authentication supporting VLAN assignment and
Auth-Fail VLAN configuration example
Network requirement
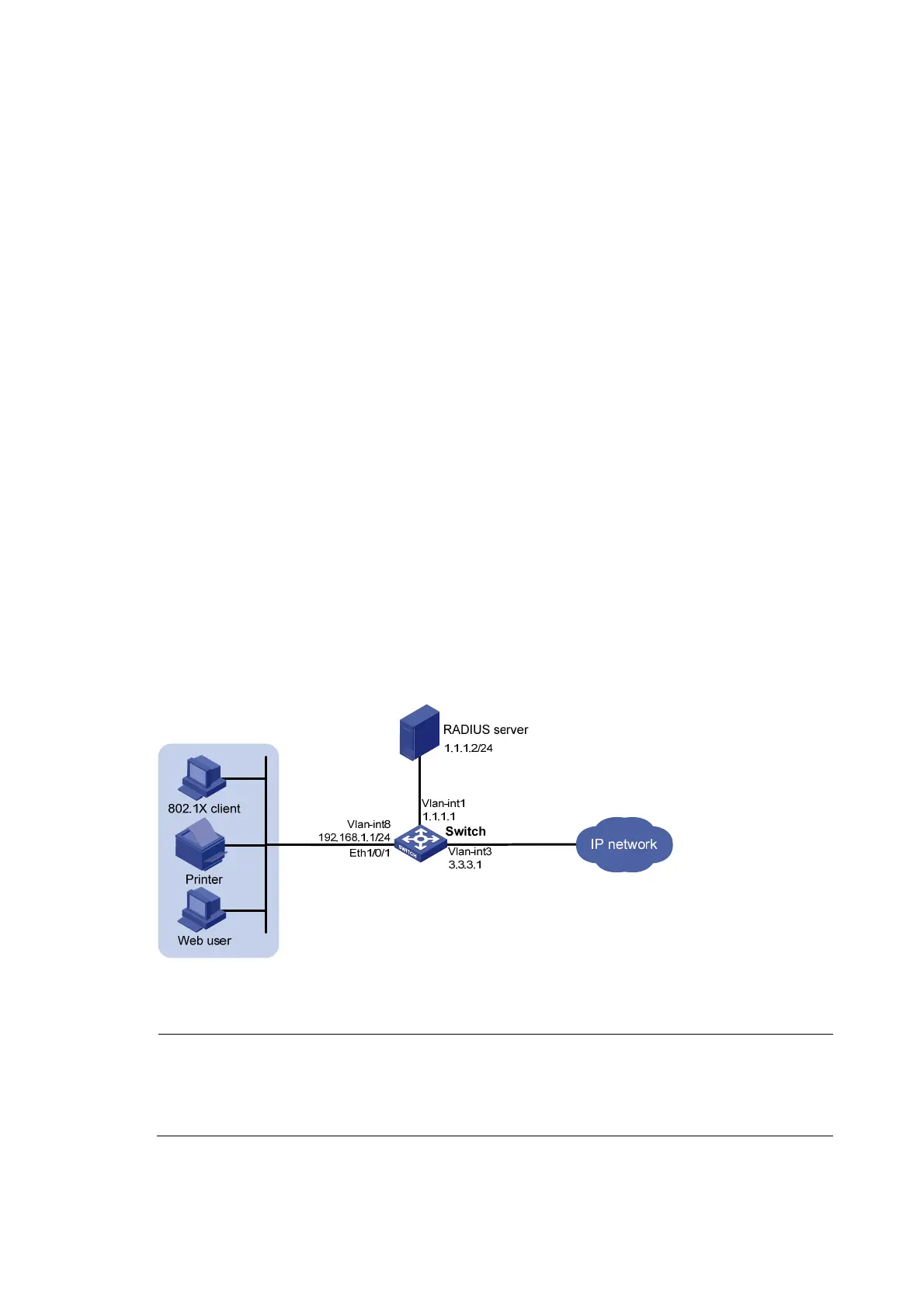
As shown in Figure 87, the terminals are connected to a switch to access the IP network. Configure triple
authentication on the Layer-2 interface of the switch which connects to the terminals so that a terminal
passing one of the three authentication methods, 802.1X authentication, portal authentication, and MAC
authentication, can access the IP network.
• Portal terminals use DHCP to get IP addresses in 192.168.1.0/24 before authentication and in
3.3.3.0/24 after passing authentication.
• 802.1X terminals use IP addresses in 192.168.1.0/24 before authentication, and request IP
addresses in 3.3.3.0/24 through DHCP after passing authentication. If the terminal fails
authentication, it uses an IP address in 2.2.2.0/24.
• After passing authentication, the printer obtains the IP address 3.3.3.111/24 that is bound with its
MAC address through DHCP.
• Use the remote RADIUS server to perform authentication, authorization, and accounting and
configure the switch to remove the ISP domain names from usernames sent to the RADIUS server.
• The local portal authentication server on the switch uses listening IP address 4.4.4.4. The switch
sends a default authentication page to the web user and forwards authentication data by using
HTTPS.
• Configure VLAN 3 as the authorized VLAN on the RADIUS server. Users passing authentication are
added to this VLAN.
• Configure VLAN 2 as the Auth-Fail VLAN on the access device. Users failing authentication are
added to this VLAN, and are allowed to access only the Update server.
Figure 87 Network diagram
Configuration procedure
NOTE:
• Make sure that the terminals, the servers, and the switch can reach each other.
• When using an external DHCP server, make sure that the terminals can get IP addresses from the server
before and after authentication.

 Loading...
Loading...















