64
AAA for 802.1X users by a RADIUS server
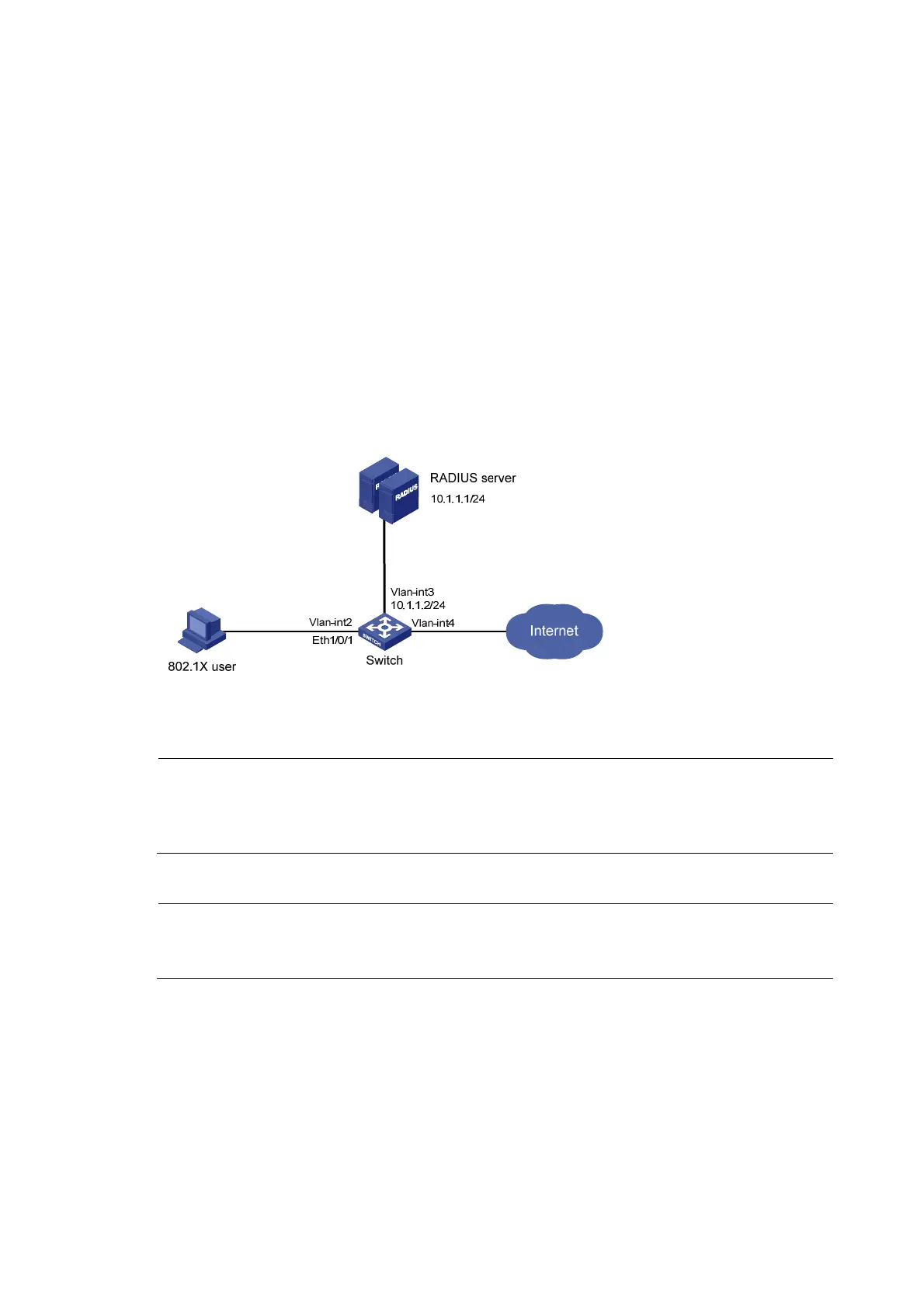
Network requirements
As shown in Figure 26, configure the switch to:
• Use the RADIUS server for authentication, authorization, and accounting of 802.1X users.
• Use MAC-based access control on Ethernet 1/0/1 to authenticate all 802.1X users on the port
separately.
• Include the domain name in a username sent to the RADIUS server.
On the RADIUS server, add a service that charges 120 dollars for up to 120 hours per month and assigns
authenticated users to VLAN 4, configure a user with the name dot1x@bbb, and register the service for
the user.
Set the shared keys for secure RADIUS communication to expert. Set the ports for
authentication/authorization and accounting to 1812 and 1813 respectively.
Figure 26 Network diagram
Configuration procedure
NOTE:
Configure the interfaces and VLANs as shown in Figure 26. Make sure that the host can get a new IP
address manually or automatically and
can access resources in the authorized VLAN after passing
authentication.
1. Configure the RADIUS server (iMC PLAT 5.0)
NOTE:
This example assumes that the RADIUS server runs iMC PLAT 5.0 (E0101), iMC UAM 5.0 (E0101), and
iMC CAMS 5.0 (E0101).
# Add an access device.
Log in to the iMC management platform, click the Service tab, and select User Access Manager > Access
Device from the navigation tree to enter the Access Device List page. Then, click Add to enter the Add
Access Device page and perform the following configurations:
• Set the shared key for secure authentication and accounting communication to expert
• Specify the ports for authentication and accounting as 1812 and 1813 respectively

 Loading...
Loading...















