Chapter 12 Common Configuration Examples
166 Aerohive
User Profiles
Unlike a traditional PSK SSID, a private PSK SSID can support multiple user profiles. For this example, you create
two user profiles, one for employees with full network access and another for contractors with limited access.
To define a user profile for employees, click Configuration > User Profiles > New, enter the following, leave
the other settings as they are, and then click Save:
Name: Employees(30)
The number 30 is included as part of the user profile name so that you can easily know its attribute.
Attribute Number: 30
The HiveAP uses this attribute number to link the user profile to a user group with the same
attribute. You can use any number between 1 and 4095.
Default VLAN: 1
Description: Corporate employees
To define a user profile for contractors with a firewall policy that allows basic network protocols to the public
network while blocking access to the internal network, click Configuration > User Profiles > New, enter the
following, leave the other settings as they are, and then click Save:
Name: Contractors(35)
Attribute Number: 35
Default VLAN: 1
Description: short-term contractors
Expand Firewalls, and enter the following in the IP Firewall Policy section:
From-Access: Click the New icon to open the IP Firewall Policy dialog box, and then enter the following:
Policy Name: contractors-outgoing-IP-policy
Description: Apply to contractor user profiles
Policy Rules:
To add rules permitting only DHCP, DNS, HTTP, and HTTPS to the public network while denying
any type of traffic to the internal network, enter the following (use CTRL-click or SHIFT-click to
select multiple services):
Click Save to save the IP firewall policy and return to the User Profile dialog box.
From-Access: contractors-outgoing-IP-policy (This is the firewall policy that you just created.)
To-Access: (nothing)
Default Action: Deny
(Click …) Source Destination
*
* The three addresses "10.0.0.0/8", "172.16.0.0/12", and "192.168.0.0/16" that define private network
address space were created in a previous example. See "Address Objects" on page 159.
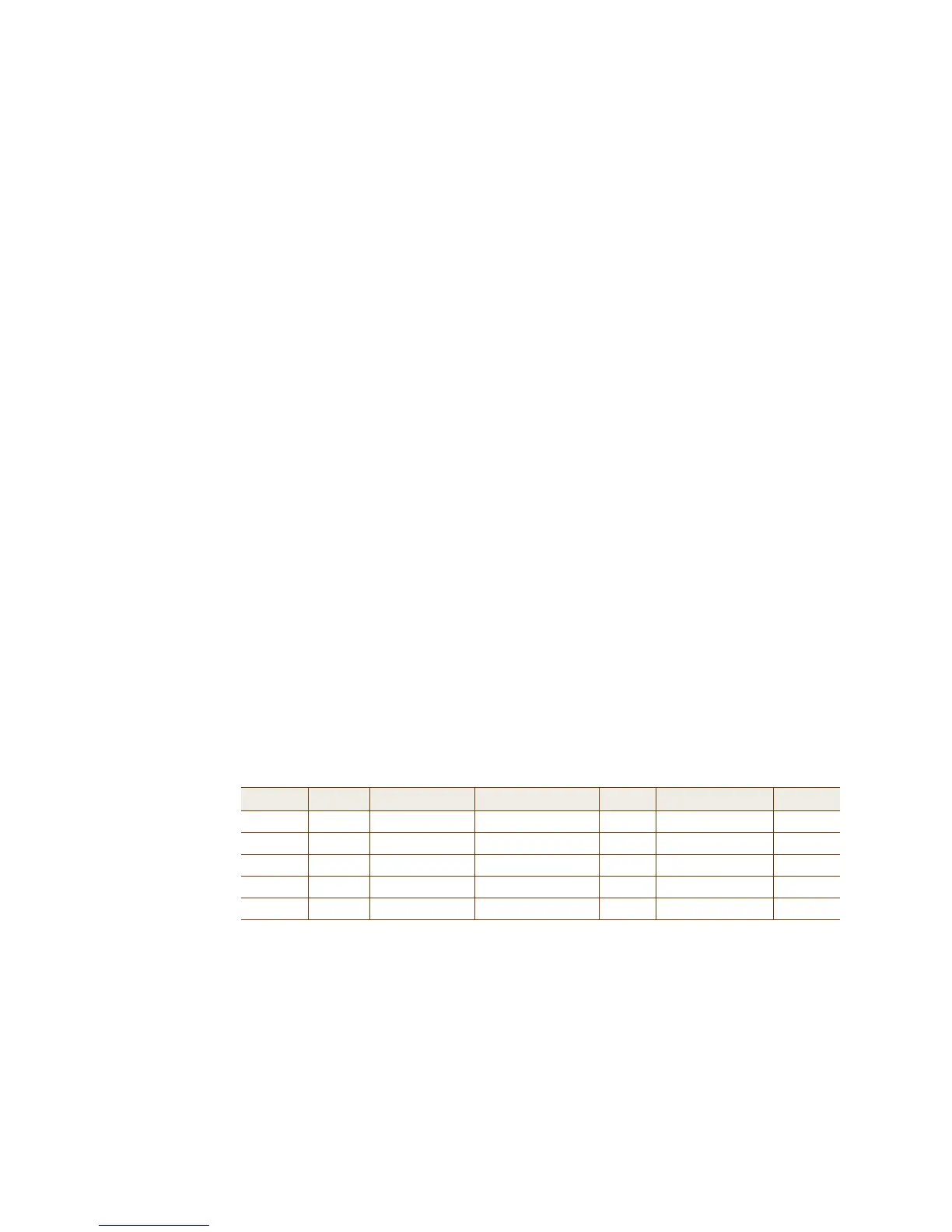
Service Action Logging (Click …)
[-any-] [-any-] DHCP-Server, DNS Permit Off Apply.
New. [-any-] 10.0.0.0/8 [-any-] Deny Dropped Packets Apply.
New. [-any-] 172.16.0.0/12 [-any-] Deny Dropped Packets Apply.
New. [-any-] 192.168.0.0/16 [-any-] Deny Dropped Packets Apply.
New. [-any-] [-any-] HTTP, HTTPS Permit Both Apply.
 Loading...
Loading...