Chapter 2 Deployment Considerations
Basic Deployment Factors for Cisco Secure ACS
2-8
User Guide for Cisco Secure ACS for Windows Server
78-16592-01
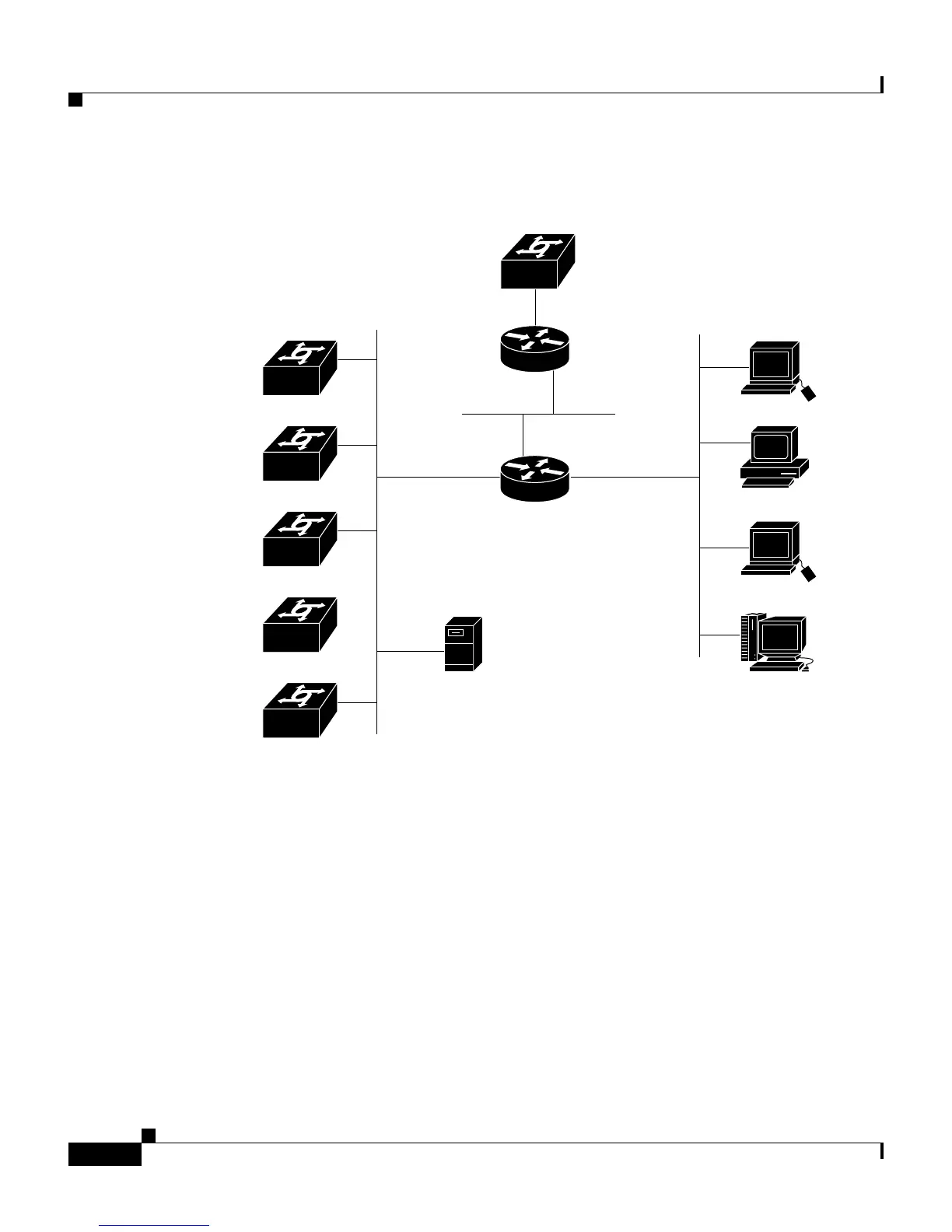
Figure 2-2 Large Dial-up Network
In a very large, geographically dispersed network (Figure 2-3), there may be
access servers located in different parts of a city, in different cities, or on different
continents. If network latency is not an issue, a central Cisco Secure ACS may
work but connection reliability over long distances may cause problems. In this
case, local Cisco Secure ACSes may be preferable to a central Cisco Secure ACS.
If the need for a globally coherent user database is most important, database
replication or synchronization from a central Cisco Secure ACS may be
necessary. Authentication using external databases, such as a Windows user
database or the Lightweight Directory Access Protocol (LDAP), can further
complicate the deployment of distributed, localized Cisco Secure ACSes. While
Cisco Secure ACS uses encryption for all replication and database
synchronization traffic, additional security measures may be required to protect
the network and user information that Cisco Secure ACS sends across the WAN.
63487
Cisco AS5300's
Macintosh server
Novell server
UNIX server
Windows NT server
Cisco Secure
Access Control
Server
Cisco AS5300
 Loading...
Loading...











