Chapter 2 Deployment Considerations
Basic Deployment Factors for Cisco Secure ACS
2-12
User Guide for Cisco Secure ACS for Windows Server
78-16592-01
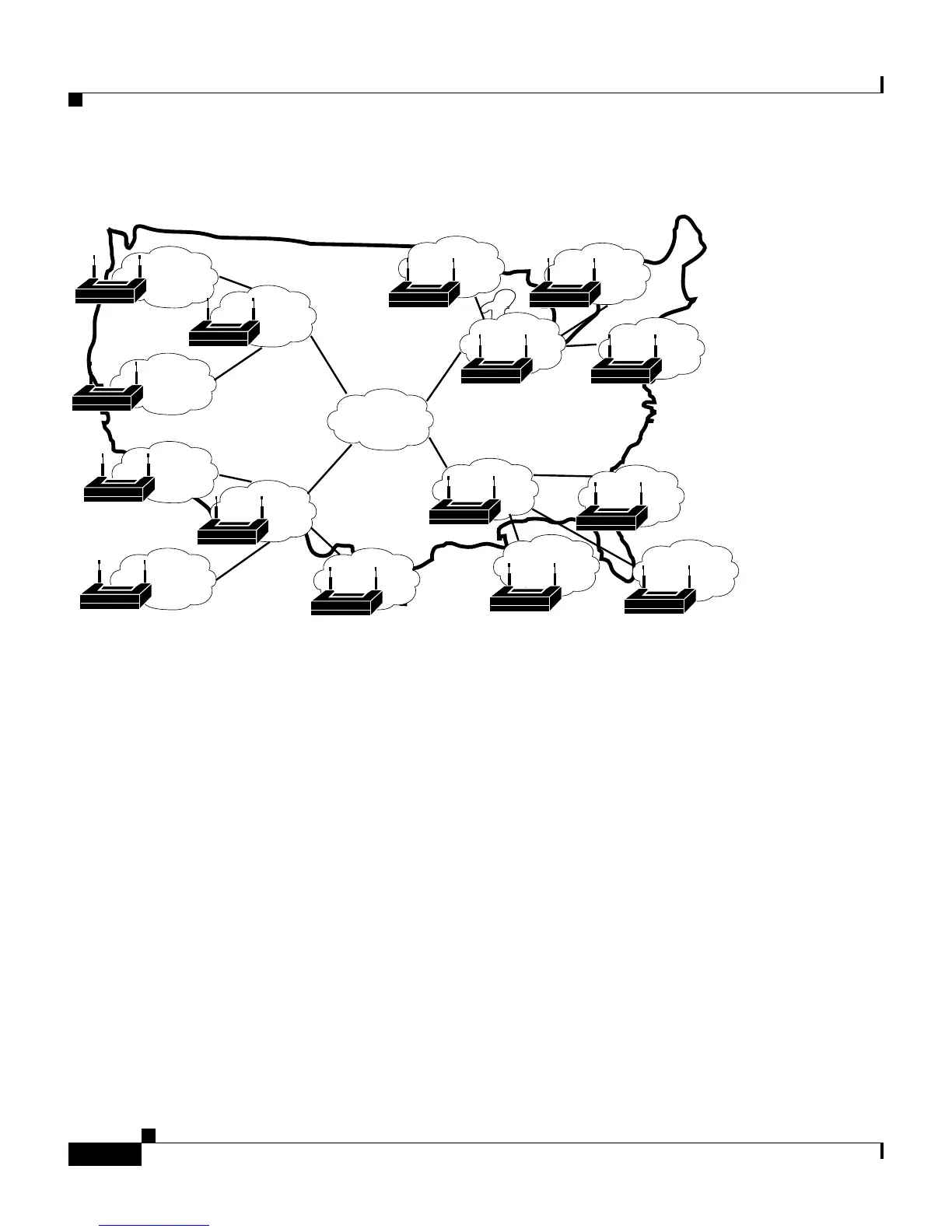
Figure 2-6 Large Deployment of Small Sites
For the model in Figure 2-6, the location of Cisco Secure ACS depends on
whether all users need access on any AP, or whether users require only regional
or local network access. Along with database type, these factors control whether
local or regional Cisco Secure ACSes are required, and how database continuity
is maintained. In this very large deployment model, security becomes a more
complicated issue, too.
Remote Access using VPN
Virtual Private Networks (VPNs) use advanced encryption and tunneling to
permit organizations to establish secure, end-to-end, private network connections
over third-party networks, such as the Internet or extranets (Figure 2-7). The
benefits of a VPN include the following:
• Cost Savings—By leveraging third-party networks with VPN, organizations
no longer have to use expensive leased or frame relay lines and can connect
remote users to their corporate networks via a local Internet service provider
(ISP) instead of using expensive toll-free or long-distance calls to
resource-consuming modem banks.
I
63491
 Loading...
Loading...











