7-5
Cisco 850 Series and Cisco 870 Series Access Routers Software Configuration Guide
OL-5332-01
Chapter 7 Configuring VPNs Using an IPSec Tunnel and Generic Routing Encapsulation
Configure a VPN
Enable Policy Lookup
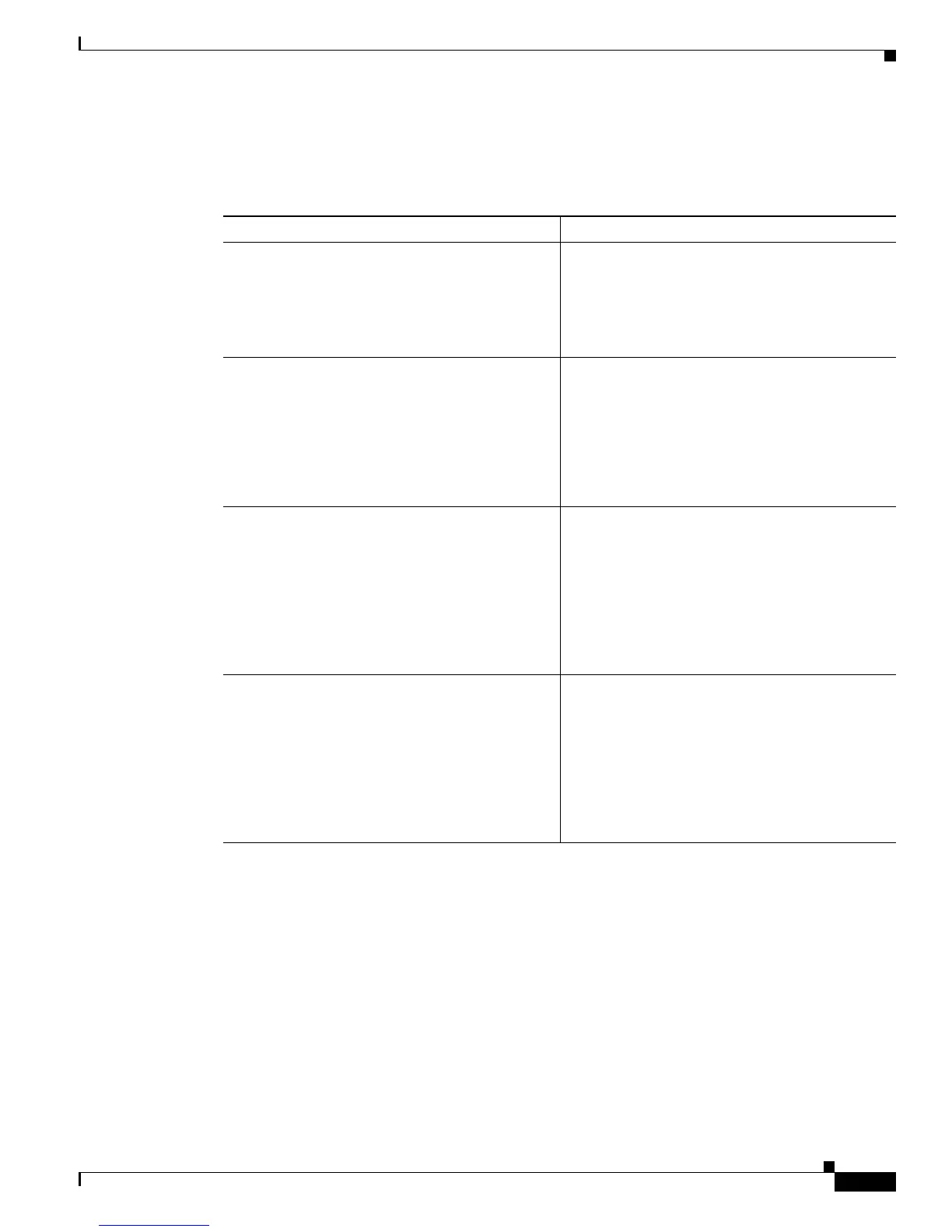
Perform these steps to enable policy lookup through AAA, beginning in global configuration mode:
Command or Action Purpose
Step 1
aaa new-model
Example:
Router(config)# aaa new-model
Router(config)#
Enables the AAA access control model.
Step 2
aaa authentication login {default | list-name}
method1 [method2...]
Example:
Router(config)# aaa authentication login
rtr-remote local
Router(config)#
Specifies AAA authentication of selected users at
login, and specifies the method used.
This example uses a local authentication database.
You could also use a RADIUS server for this. See
the
Cisco IOS Security Configuration Guide and
the Cisco IOS Security Command Reference for
details.
Step 3
aaa authorization {network | exec | commands
level | reverse-access | configuration} {default |
list-name} [method1 [method2...]]
Example:
Router(config)# aaa authorization network
rtr-remote local
Router(config)#
Specifies AAA authorization of all
network-related service requests, including PPP,
and the method used to do so.
This example uses a local authorization database.
You could also use a RADIUS server for this. See
the
Cisco IOS Security Configuration Guide and
the Cisco IOS Security Command Reference for
details.
Step 4
username name {nopassword | password
password | password encryption-type
encrypted-password}
Example:
Router(config)# username cisco password 0
cisco
Router(config)#
Establishes a username-based authentication
system.
This example implements a username of cisco
with an encrypted password of cisco.
Configure IPSec Transforms and Protocols
A transform set represents a certain combination of security protocols and algorithms. During IKE
negotiation, the peers agree to use a particular transform set for protecting data flow.
During IKE negotiations, the peers search in multiple transform sets for a transform that is the same at
both peers. When such a transform set is found, it is selected and applied to the protected traffic as a part
of both peers’ configurations.

 Loading...
Loading...











