• Intrusion—Use the intrusion policies to inspect for known threats. Although you apply intrusion policies
using access control rules, you can edit the intrusion policies to selectively enable or disable specific
intrusion rules.
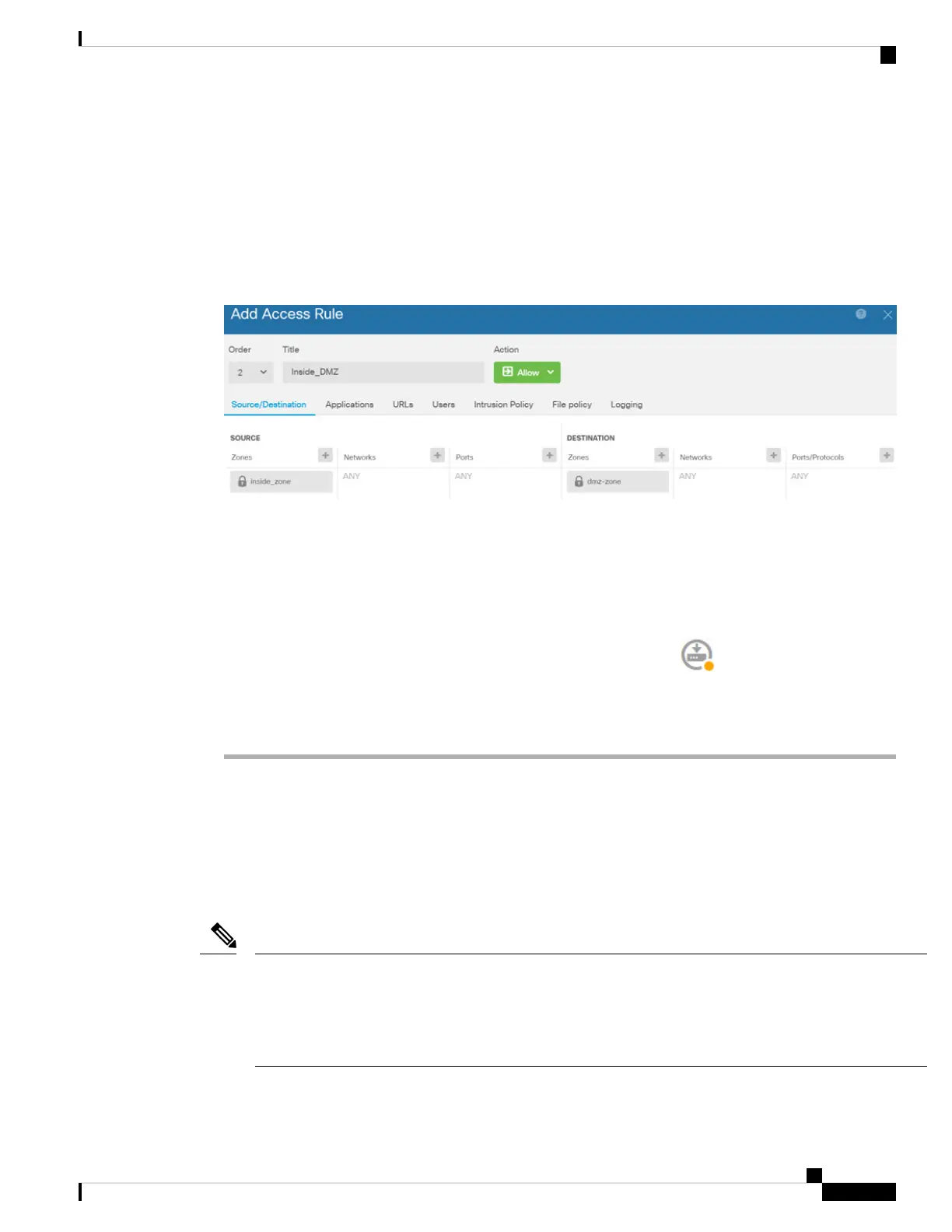
The following example shows how to allow traffic between the inside-zone and dmz-zone in the access control
policy. In this example, no options are set on any of the other tabs except for Logging, where At End of
Connection is selected.
Figure 34: Access Control Policy
Step 6 Choose Device, then click View Configuration in the Updates group and configure the update schedules for
the system databases.
If you are using intrusion policies, set up regular updates for the Rules and VDB databases. If you use Security
Intelligence feeds, set an update schedule for them. If you use geolocation in any security policies as matching
criteria, set an update schedule for that database.
Step 7 Click the Deploy button in the menu, then click the Deploy Now button ( ), to deploy your changes to
the device.
Changes are not active on the device until you deploy them.
Access the Threat Defense and FXOS CLI
Use the command-line interface (CLI) to set up the system and do basic system troubleshooting. You cannot
configure policies through a CLI session. You can access the CLI by connecting to the console port.
You can also access the FXOS CLI for troubleshooting purposes.
You can alternatively SSH to the Management interface of the threat defense device. Unlike a console session,
the SSH session defaults to the threat defense CLI, from which you can connect to the FXOS CLI using the
connect fxos command. You can later connect to the address on a data interface if you open the interface for
SSH connections. SSH access to data interfaces is disabled by default. This procedure describes console port
access, which defaults to the FXOS CLI.
Note
Cisco Firepower 1010 Getting Started Guide
111
Threat Defense Deployment with the Device Manager
Access the Threat Defense and FXOS CLI
 Loading...
Loading...
















