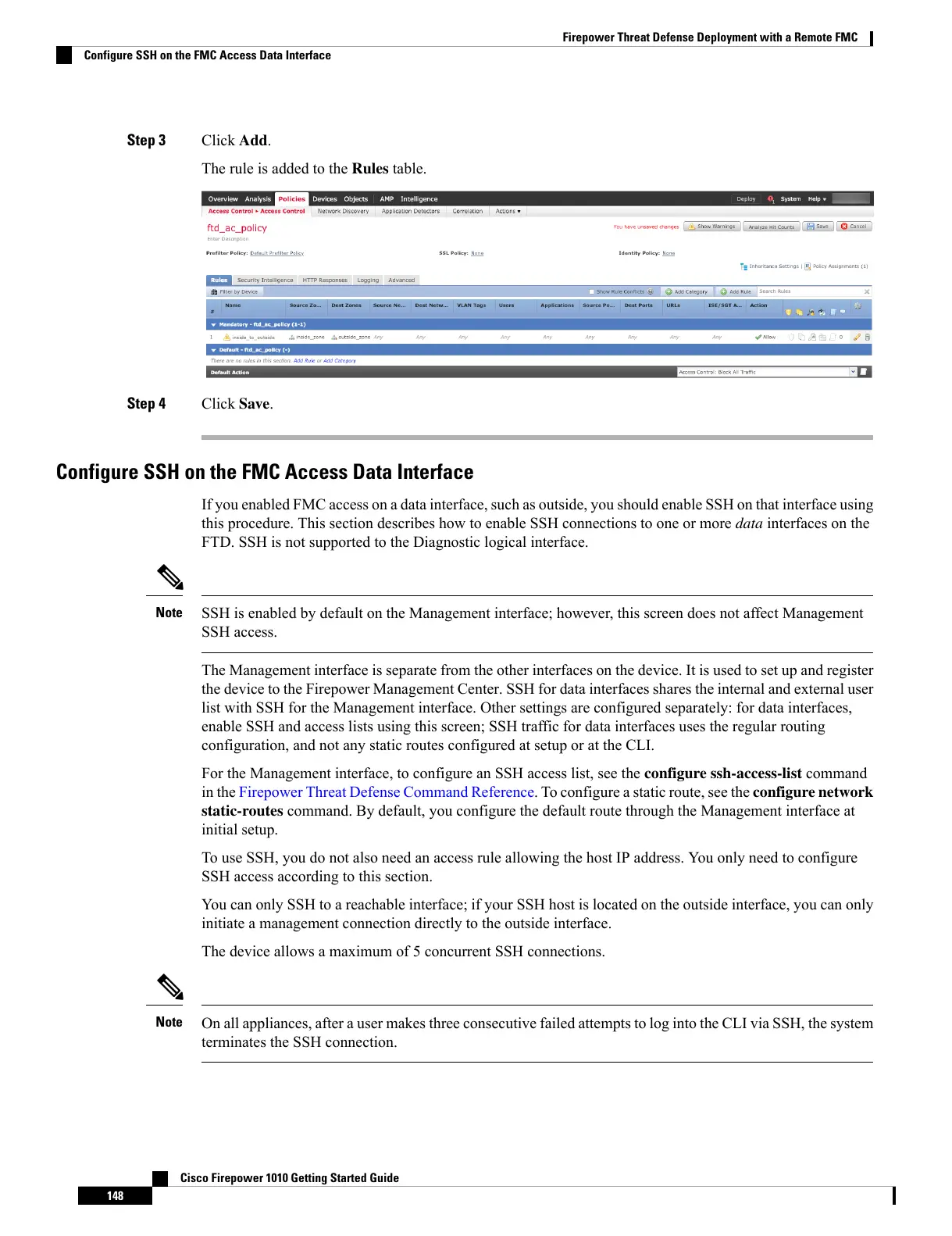
Step 3 Click Add.
The rule is added to the Rules table.
Step 4 Click Save.
Configure SSH on the FMC Access Data Interface
If you enabled FMC access on a data interface, such as outside, you should enable SSH on that interface using
this procedure. This section describes how to enable SSH connections to one or more data interfaces on the
FTD. SSH is not supported to the Diagnostic logical interface.
SSH is enabled by default on the Management interface; however, this screen does not affect Management
SSH access.
Note
The Management interface is separate from the other interfaces on the device. It is used to set up and register
the device to the Firepower Management Center. SSH for data interfaces shares the internal and external user
list with SSH for the Management interface. Other settings are configured separately: for data interfaces,
enable SSH and access lists using this screen; SSH traffic for data interfaces uses the regular routing
configuration, and not any static routes configured at setup or at the CLI.
For the Management interface, to configure an SSH access list, see the configure ssh-access-list command
in the Firepower Threat Defense Command Reference. To configure a static route, see the configure network
static-routes command. By default, you configure the default route through the Management interface at
initial setup.
To use SSH, you do not also need an access rule allowing the host IP address. You only need to configure
SSH access according to this section.
You can only SSH to a reachable interface; if your SSH host is located on the outside interface, you can only
initiate a management connection directly to the outside interface.
The device allows a maximum of 5 concurrent SSH connections.
On all appliances, after a user makes three consecutive failed attempts to log into the CLI via SSH, the system
terminates the SSH connection.
Note
Cisco Firepower 1010 Getting Started Guide
148
Firepower Threat Defense Deployment with a Remote FMC
Configure SSH on the FMC Access Data Interface
 Loading...
Loading...











