V001 CL64WLAN User Manual
32 of 44
• IGMP Setting
These menus allow to configure some items related with applications running in the network
managed by the slave unit.
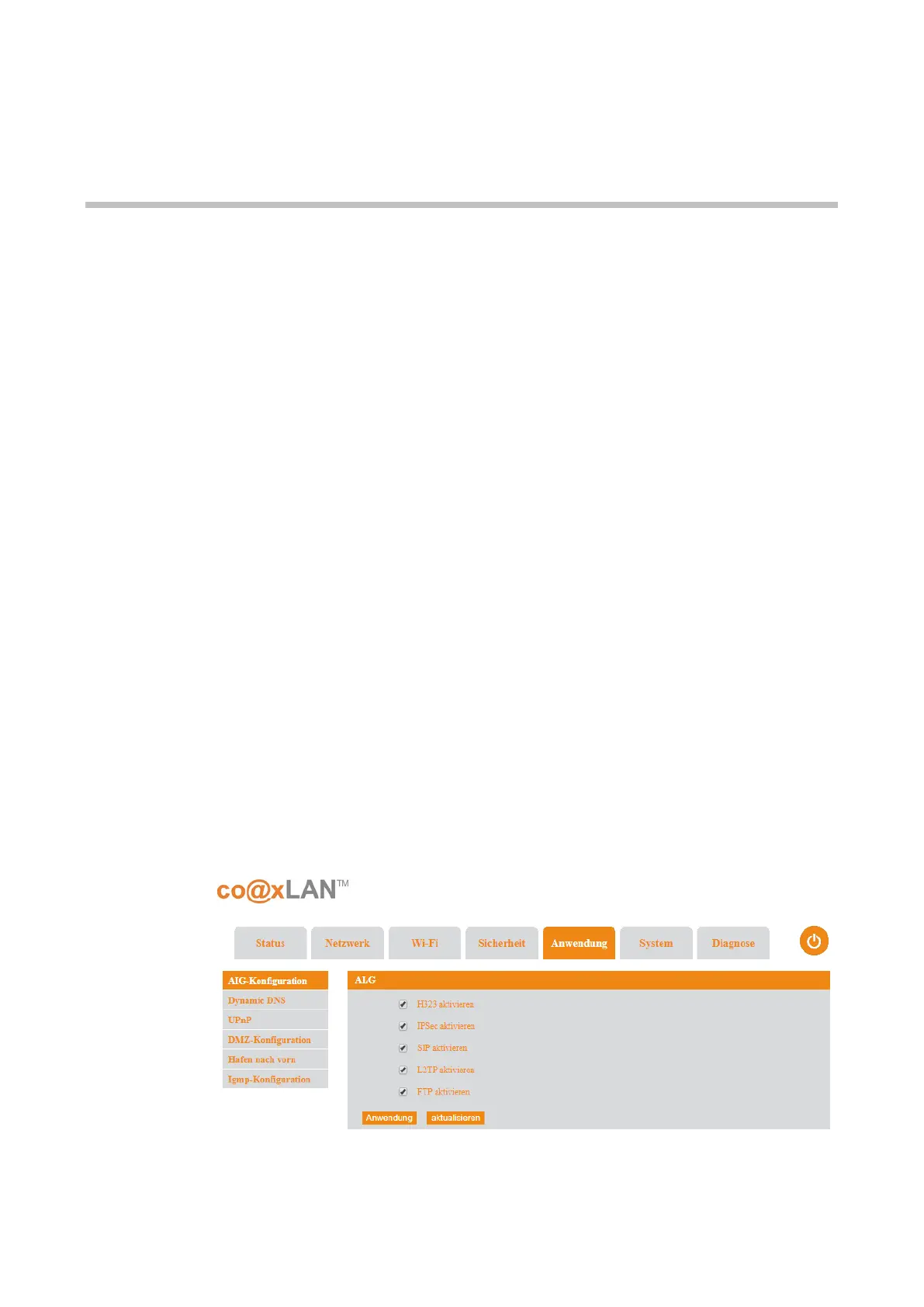
9.1. ALG Setting
If the ALG Setting sub-menu is selected the screen shown in Picture is displayed. This page
allows to enable or disable the following protocols:
• H.323: it is a protocol designed for the setup, management and termination of a
media session. It is one of a set of standards from the ITU-T, which defines a large set
of protocols to provide audio and visual communication over a computer network.
• IPSec: Internet Protocol Security, is a network protocol suite that authenticates and
encrypts the packets of data sent over a network. IPsec includes protocols for
establishing mutual authentication between agents at the beginning of the session
and negotiation of cryptographic keys for use during the session. IPsec can protect
data flows between a pair of hosts (host-to-host), between a pair of security
gateways (network-to-network), or between a security gateway and a host
(network-to-host).[1] Internet Protocol security (IPsec) uses cryptographic security
services to protect communications over Internet Protocol (IP) networks. IPsec
supports network-level peer authentication, data-origin authentication, data
integrity, data confidentiality (encryption), and replay protection. Only IPsec
protects all application traffic over an IP network. IPsec can automatically secure
applications at the IP layer.
• SIP: Session Initiation Protocol, it is a communications protocol for signalling, for the
purpose of controlling multimedia communication sessions. The most common
applications of SIP are in Internet telephony for voice and video calls, private IP
telephone systems, as well as instant messaging over Internet Protocol (IP) networks.
• L2TP: Layer 2 Tunneling Protocol, it is a tunneling protocol used to support virtual
private networks (VPNs) or as part of the delivery of services by ISPs. It does not
provide any encryption or confidentiality by itself. Rather, it relies on an encryption
protocol that it passes within the tunnel to provide privacy
• FTP: File Transfer Protocol, it is a standard network protocol used for the transfer of
computer files from a server to a client using the Client–server model on a computer
network.
Picture 21
 Loading...
Loading...