Dynamic Defense
Whitelist
Allowed IPs and ports range, multiple IP addresses, and port range.
For example:
192.168.2.10-
192.168.2.20 5060:5061
Blacklist
Black List Users will be able to view the IPs that have been blocked by GXW450X.
Table 15: GXW450X Firewall Dynamic Defense
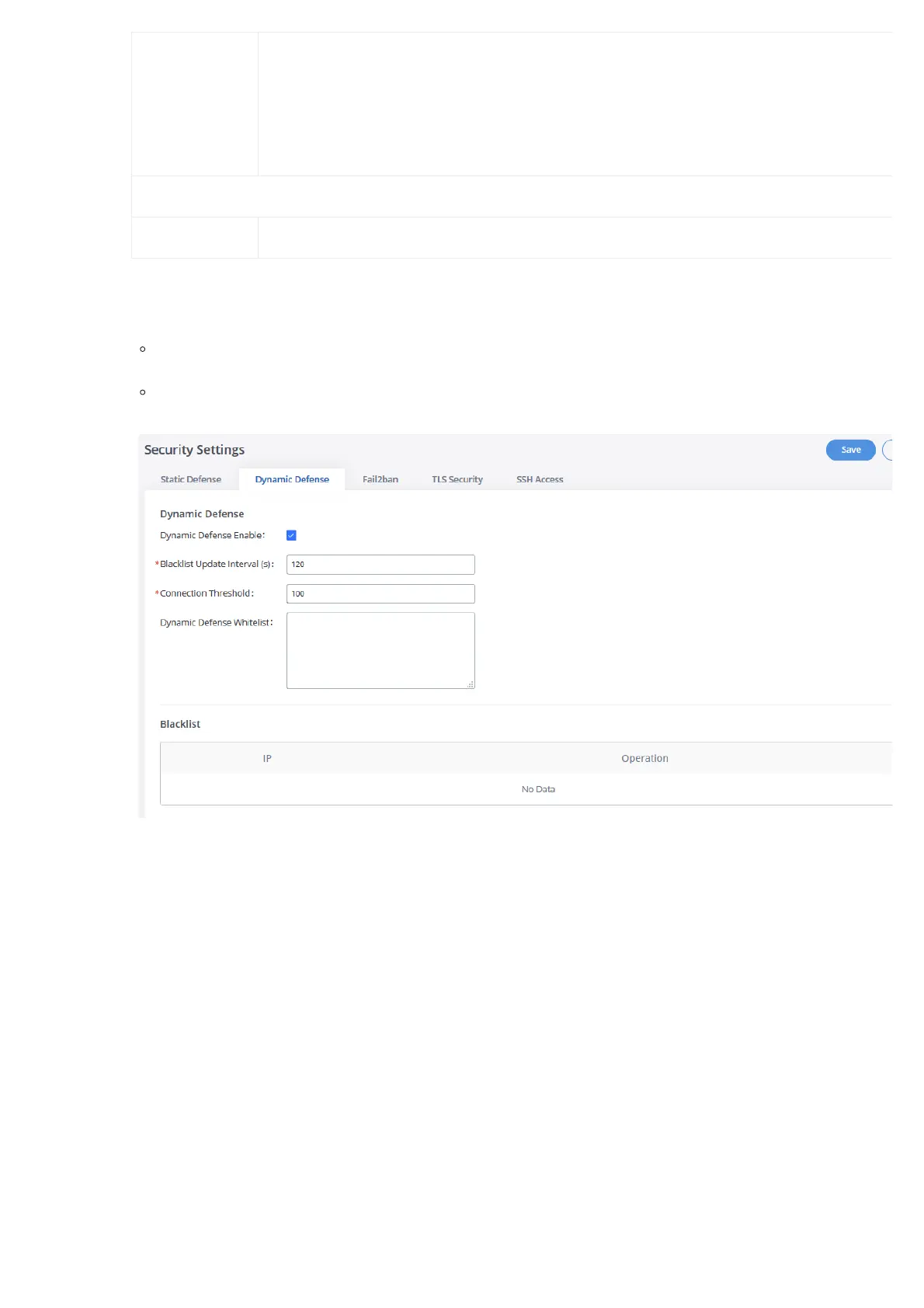
The following figure shows a configuration example:
If a host at IP address 192.168.2.5 initiates more than 100 TCP connections to the GXW450X, it will be added to the GXW450X blacklist. This ho
192.168.2.5 will be blocked by the GXW450X for 500 seconds.
Since IP range 192.168.2.10-192.168.2.20 is in the whitelist, if a host initiates more than 20 TCP connections to the GXW450X within 1 minute,
not be added to the GXW450X blacklist. It can still establish a TCP connection with the GXW450X.
Figure 29: Dynamic Defense Configuration
Fail2Ban
Fail2Ban feature on the GXW450X provides intrusion detection and prevention for authentication errors in SIP INVITE and SUBSCRIBE. Once the en
detected within “Max Retry Duration”, the GXW450X will act to forbid the host for a certain period as defined in “Banned Duration”. This feature he
prevent SIP brute force attacks on the gateway system.

 Loading...
Loading...











