configuration definition file, users who can use virtual command device
can be restricted. For the details about the settings to
HORCM_ALLOW_INST, please refer to "Configuration definition file".
• Security setting for virtual command device
By using the following environment variable, security can be set to virtual
command device.
$HORCM_IPCMDSEC=<value>
Specify the number (from 0 to 7) to <value> depending on the contents of
the security which you want, in reference with the following table.
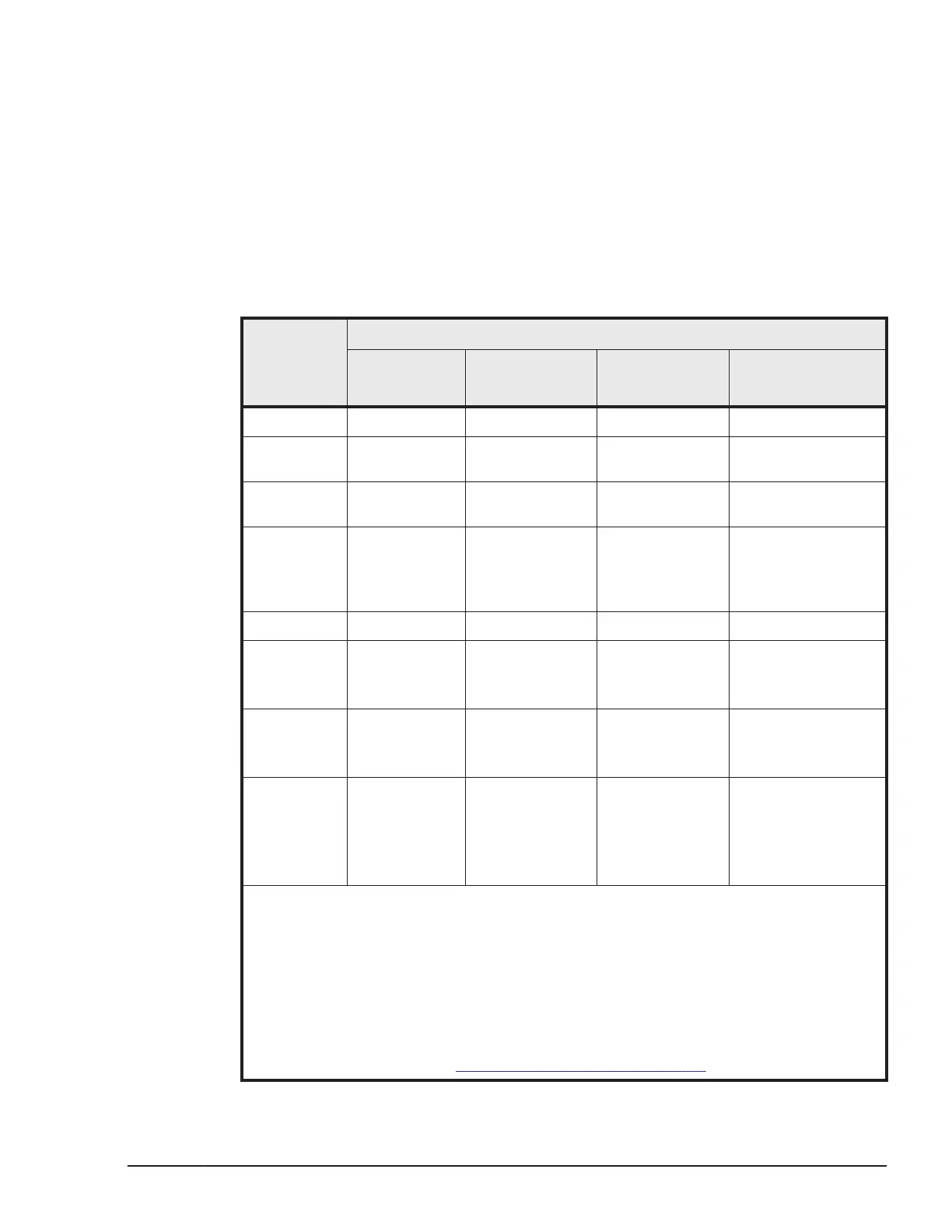
Table 3-1 Security setting for virtual command device
Value
specified
for
<value>
Command device setting
Security
setting
User
authentication
Device group
definition
Security to be set
(see Notes)
0 OFF OFF OFF No security
1 OFF OFF ON Only HORCM_DEV
allowed
2 OFF ON OFF User authentication
required
3 OFF ON ON User authentication
required
Only HORCM_DEV
allowed
4 ON OFF OFF CMD security
5 ON OFF ON CMD security
Only HORCM_DEV
allowed
6 ON ON OFF CMD security
User authentication
required
7 ON ON ON CMD security
User authentication
required
Only HORCM_DEV
allowed
Notes:
• ON: Enabled
• OFF: Disabled
• Only HORCM_DEV allowed: the operation can be performed only for paired logical
volumes described in HORCM_DEV.
• User authentication required: only commands issued by authorized users can be
executed.
• CMD security: only devices recognizable from the host can be operated. For details
about CMD security, see
Data Protection facility on page 7-5.
CCI functions
3-7
Command Control Interface User and Reference Guide

 Loading...
Loading...











